What is the “code that changed the world” that forms the modern Internet?

by
The Internet is now a human being, with the latest events happening all over the world being able to know immediately while being far away, or simply searching for what you want from an infinite amount of information. It is an indispensable part of life. Among the technologies that support the Internet, news media Slate Magazine has compiled ' codes that changed the world .'
The lines of code that changed everything.
https://slate.com/technology/2019/10/consequential-computer-code-software-history.html
1725: Binary punch card
Binary programming began long before modern computers appeared. In 1725, Basile Bouchon , working in Lyon, France, devised a way to control a machine with a hole in paper. The holed part means “1” and the part without a hole means “0”, and it seems that the loom was controlled by this binary number. Since the idea of controlling the machine with '0' and '1' is no different from the basics of modern codes, the perforated card that was born in 1725 without a computer is called the first code.

by
1948: First modern code
Clara Dan von Neumann, known as one of the world's first computer programmers, and Nicholas Metropolis , a researcher at the Los Alamos National Laboratory , executed the first modern code using ENIAC . The first code was hundreds of numeric instructions executed from addressable read-only memory.
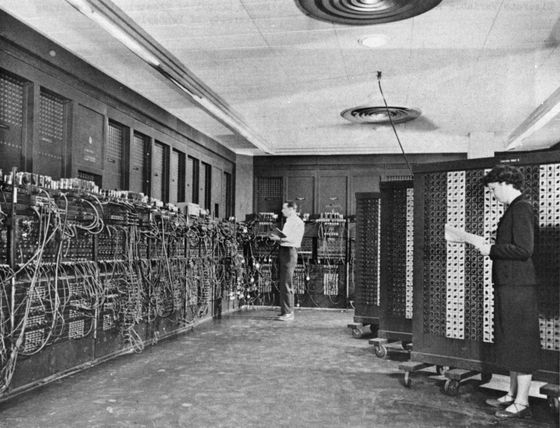
by US Army Photo
It seems that the probability distribution used for the simulation in the atomic bomb design was repeatedly mapped by
1952: World's first compiler
Grace Hopper, also known as the creator of the programming language COBOL , is one of the people who used to program on early computers. When Hopper joined the army during the Second World War as a naval reserve, he saw the military bosses struggling to understand binary code, and programming became a more human language. It seems to have aimed to make it easy to understand.
Hopper's idea was ridiculed by some people, but by the beginning of 1950, he would devise a compiler . The first compiler was to convert code that humans could understand as a language into an instruction set that could be processed directly by a computer.
Subsequently, Hopper has developed the world's first programming language for data processing, FLOW-MATIC , close to English, with colleagues. As for the compiler that Hopper created, Slate Magazine wrote that 'Computers can now process words.'
by Algernai Hayes
1961: World's first computer game ' Space War! '
In late 1961, PDP-1 became available to groups of young employees, students and friends at the Massachusetts Institute of Technology (MIT). At that time, PDP-1, which was the most advanced computer in non-military computing, was an ultra-high-end product sold at $ 120,000 ($ 1 million at the time of article creation: more than approximately 110 million yen). The computer has a word length of 18 bits, a standard main memory with a capacity of 4K words (equivalent to 9K bytes), and can be expanded to a maximum of 64K words (144K bytes).
A group of students uses paper tape for programming storage, and over a period of five months, creates a game called “Space War!” Where two players control the spacecraft. Space War in 1962! Can be seen in the following movie.
Spacewar! (1962)-YouTube
Space War! Was distributed by DEC along with PDP-1 preloaded into the core memory, so it spread rapidly in the early hacker community and had a huge impact on many video game creators. Space war with emulators even at the time of article creation! Can be played , and PDP-1 on display at the Computer History Museum is regularly repeated.
Space War! Steve Russell, who led the team in the development of the company, said in the event at the Smithsonian Museum in 2018: “There were no user complaints and no crash reports. You can use it. '
1965: Origin of email
In 1961, MIT hackers developed a “ time sharing system ” that allows multiple users to log in to the same computer at the same time . In 1965, the coders created a command system that would allow users using the time-sharing system to communicate with each other to send, receive, and display digital documents.
[code] WHENEVER A (1) E FENCE OR A (2) E FENCE OR A (3) E FENCE
PRFULL. ($ 'R'1INSTRUCTIONS: $)
PRFULL. ($ '4MAIL NAME1 NAME2 PROB1 PROG1 PROB2 PROG2 ... $)
PRFULL. ($ WHERE '= NAME1 NAME2' = IS THE FILE TO BE MAILED, $)
PRFULL. ($ AND '= PROBN PROGN' = ARE DIRECTORIES TO WHICH '8 $,
1 $ IT IS TO BE SENT.'B $)
CHNCOM. (0)
END OF CONDITIONAL [/ code]
1969: Apollo 11 lunar module bayout code
Apollo 11 , the first man to land on the moon, automatically controls all Apollo spacecraft navigation functions, called the Apollo Guidance Computer (AGC), and is used by astronauts to check and correct flight information. Computer was installed.
Because AGC was required to operate within limited power and storage space, it was necessary to always be able to focus on the most important tasks. The team that developed AGC's software creates the code “BAILOUT” to account for the possibility of unplanned events. This means that if AGC is in danger of running out of space or overflowing, it will schedule less important data and operations so that only important data and hull operations can be maintained.
When the “Eagle” of the Apollo lunar lander descends toward the moon, the AGC in the Eagle malfunctioned and the “1202” alarm sounded. The reason for this warning was not immediately recognized by Captain Neil Armstrong, but computer experts in mission control seemed to understand that the BAILOUT set up in AGC worked properly. In other words, the low-priority tasks were discarded, and important hull control and other tasks were resumed, so the descent of the moon could be done without problems.
[code] POODOO INHINT
CA Q
TS ALMCADR
TC BANKCALL
CADR VAC5STOR # STORE ERASABLES FOR DEBUGGING PURPOSES.
INDEX ALMCADR
CAF 0
ABORT2 TC BORTENT
OCT77770 OCT 77770 # DONT MOVE
CA V37FLBIT # IS AVERAGE G ON
MASK FLAGWRD7
CCS A
TC WHIMPER -1 # YES. DONT DO POODOO. DO BAILOUT.
TC DOWNFLAG
ADRES STATEFLG
TC DOWNFLAG
ADRES REINTFLG
TC DOWNFLAG
ADRES NODOFLAG
TC BANKCALL
CADR MR.KLEAN
TC WHIMPER [/ code]
1972: Hello, world!
When learning a new programming language, the first thing to do is display the phrase “Hello, world!” On your computer. This phrase is written in a programming textbook called “ Programming in CA Tutorial ” compiled by Bell Laboratories in 1974, but it is also written in another textbook written in 1972. Therefore, it is said that this is the origin.
[code] main () {printf ('hello, world \ n');} [/ code]
1988: World's first malware appears
In 1988, 23-year-old American computer scientist Robert T. Morris developed the world's first malware called the “Morris worm”. This worm is also called 'the first attack that appeared on the Internet' and was used to attack computers connected to the Internet, and it caused a lot of damage. At this time, the New York Times put the word “Internet” on the newspaper for the first time.
Even those who were familiar with programming at the time were very surprised by the wide spread of the Morris worm. Morris says he did not intend to launch an attack using a worm, but it was the first person in the world to be prosecuted under the Computer Fraud and Abuse Act. After three years of probation, Morris became co-founder of Y Combinator and Associate Professor of Computer Science at MIT.
The 'Morris worm', the world's first computer worm developed by Morris, is also summarized in the following article.
`` A History of Hacking '' that understands the history of hacking such as `` the world's first hacking was done more than 100 years ago ''-GIGAZINE

by
Around 1990s: One virus
A Fork bomb is a type of DoS attack performed against a computer system. The most famous of these is just one line of code:
[code]: () {: |: &};: [/ code]
Certain conditions are required to make this code work, such as using Bash , but running it consumes all the memory available to the computer and will not stop until the device crashes. The code is very simple and still dangerous, but what makes it more unique is the use of a colon (:) in the function. Most functions have descriptive names such as 'Print' or 'isThisEmailValid', but there is no rule that you need to do so. In most computing languages, you can't use a colon in a function name, but Bash's use seems to have led to the creation of a brutal virus that works on a single line.
1990: HTML / Hyperlink
Hyperlink was created by Tim Berners-Lee , who invented the World Wide Web (W3) and implemented and developed a hypertext system, as a 'reference' (link) function for connecting multiple documents in hypertext . .
[code] GIGAZINE [/ code]
The hyperlink created by Tim Berners-Lee is the basis for all buttons and links that exist on the Internet, including the current retweet button and the Buy Now button. That's why Slate Magazine describes hyperlinks as 'a tool that can connect everything to everything' and 'changed the world'.
1992: Appearance of JPEG
In 1992, Joint Photographic Experts Group released JPEG as a standard specification for making image files compact. Other data compression formats were available at the time, but one of the main reasons that JPEG became the global standard format is thought to be “because it was royalty-free ”. In addition, JPEG employs a lossy compression method, which is a process that removes the side of an image that cannot be detected by the human eye, and it has a major impact on the lossy compression data compression format such as MP3 later. It was.

by Scott Henderson
1993: Birth of NCSA Mosaic , the foundation of the current web
NCSA Mosaic is a web browser released in 1993 and developed by the National Supercomputer Application Laboratory (NCSA). Until NCSA Mosaic appeared, the browser was very unfriendly, and it was possible to render text, but there was a restriction that images could only be displayed in a separate window. NCSA Mosaic, which was born in the midst of such circumstances, was the first to realize the basics of today's web browser that can display images and text in a single window. Now that images and text can be displayed side by side on the same screen, the content on the Internet is easy to get close to, like a magazine or newspaper, and it has also become a big kick that attracts many users.
There are also services that allow you to surf the web with NCSA Mosaic, so check it out if you're curious about what the dawn of the Internet was like.
`` Oldweb.today '' that can surf the Internet with Internet early browsers such as Mosaic and Netscape-gigazine

Mid-1990s: Birth of pop-up ads
It was in the mid-1990s that the “ pop-up ads ” that were automatically displayed on top when a particular web page was opened were born. From here, pop-up ads will explode on the Internet.
You can put your favorite content on the free homepage, but to maintain such a page, you need to make money by displaying ads. However, advertisers have come up with the idea of separating ads from content on the web because they did n’t always think that users who visit the page where they advertise are likely to like ads. This is a pop-up ad.
Pop-up advertisement was an idea to display content and advertisement separately, but when the page is displayed, the advertisement window is displayed in the foreground of the screen, so it is just right to push out the advertisement That's why it got explosive popularity.
1996: Google page rank algorithm
Google uses ' page rank ' as an algorithm to determine the importance of web pages in search engines. Until then, it seemed that information was organized based on whether the search query matched a word in the document, but Google's page rank is 'ranking pages based on the number of pages linked online Is an algorithm.
2002: Rumba guidance system
Robot vacuum cleaner Roomba appeared in 2002. It may not have been so smart at the time of its appearance, but in 2019 it has transformed into a very high performance robot cleaner . Rumba's developer iRobot did not develop the first robot cleaner, but Rumba has the first guidance system as a robot cleaner, and this led to a revolution with robot cleaner Slate Magazine Says.
[code] (define-behavior (bounce
: start-when (or (bump?)
bounce-trigger?)
: abort-when (bump-edge?)
: onetime? t
)
) [/ code]
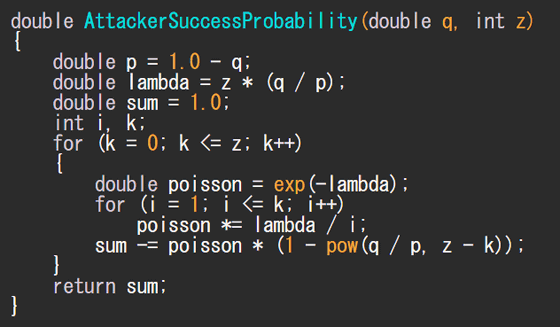
2008: Bitcoin
Bitcoin is the place where the word “virtual currency” has become popular because of its explosive popularity. Bitcoin started with a white paper published in 2008 by developer Satoshi Nakamoto. Bitcoin includes codes to limit the possibility of an attacker taking over the Bitcoin blockchain indefinitely. The code says, “Even if Bitcoin is a system made by untrustworthy people, it was convinced that the world can be trusted, opening up the future of at least 2777 other cryptocurrencies ,” Slate Magazine said. Is written.
2009: Like button
In 2009, Facebook implemented “Like Buttons” inspired by designers and programmers such as Lear Perlman and Justin Rosenstein. Until then, Facebook assumed that users did not have enough time to write comments on friends' posts frequently. Therefore, a like button is born as a function that can show that you are following the posted content more simply and easily. As a result, users all over the world share a lot of information, and by 2012, it seems that more than 1 trillion likes buttons were pushed.
The Facebook like button is realized by the following code.
[code] {'__ typename': 'PageLikeAction', 'action_type': 'LIKE', 'label': {'text': 'Like'} [/ code]
Related Posts:
in Software, Posted by logu_ii