An example of a 'malicious archive file' aimed at vulnerability of long-established compression decompression software 'WinRAR' looks like this
A security company acquires the real thing and details the contents as to what kind of thing is "malicious archive file" aimed at the vulnerability found in the long-established compression decompression software "WinRAR" .
360 Warranty Reporting Center - Warning! Upgrades in WinRAR Exploit with Social Engineering and Encryption
https://ti.360.net/blog/articles/upgrades-in-winrar-exploit-with-social-engineering-and-encryption/
A security company in China · 360 Threat Intelligence Center (360 Intelligence Center) is a malicious ACE type archive that exploits the vulnerability given the identifier of " CVE - 2018 - 20250 " among the vulnerabilities of WinRAR in 2019 It was discovered on 22nd February.
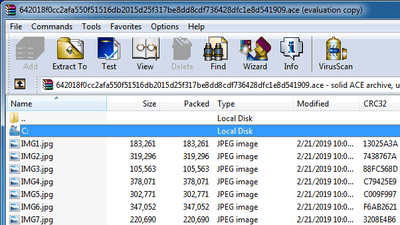
An example of a sample was opened with WinRAR. JPG files are included in large quantities.
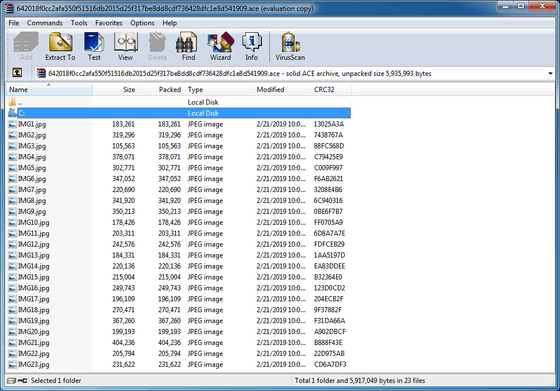
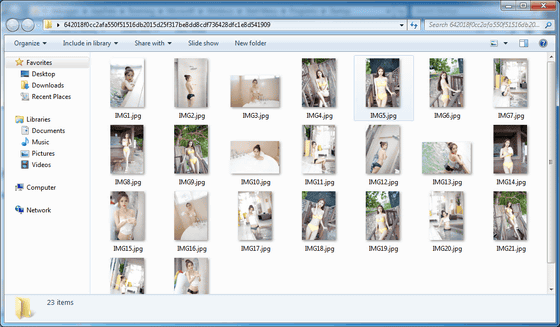
The content is such a picture.

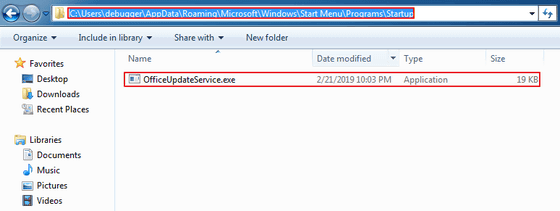
If you worry and thaw it ... ...
A file called "OfficeUpdateService.exe" is expanded in "% AppData% \ Microsoft \ Windows \ Start Menu \ Program \ Startup" and executed when the PC is re-logged in and restarted. This "OfficeUpdateService.exe" contains functions such as PC restart / termination and file management, remote shell, "Trojan horse" management, screen capture and recording.
In addition to the "malicious archive" containing image files as described above, there is an example that there is only one PDF file.
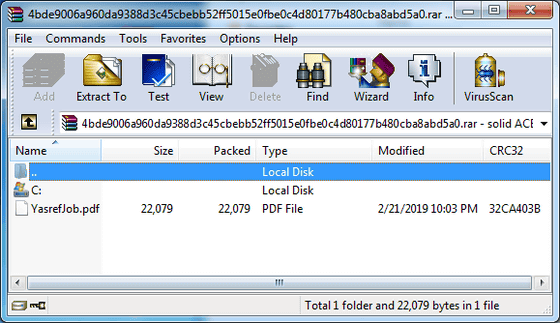
The content of this PDF file is a job description (job description) .

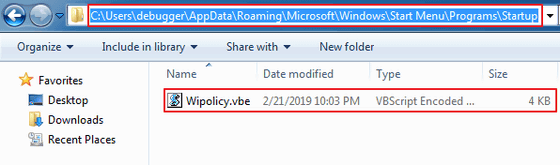
After decompressing, the "Wipolicy.vbe" file will be expanded in the startup folder. The file is encrypted, and it declared that it contained a PowerShell script, and the attacker can create a remote shell, upload and download files, load additional modules, execute other PowerShell scripts, etc. .
360 Threat Intelligence Center calls for updating to "WinRAR 5.70 beta 1" as a measure. If there are circumstances that can not be updated, it is OK even if you delete "UNACEV2.DLL" which is the cause of the vulnerability directly. In this case, an error occurs when loading ACE format files with WinRAR, but no other problem occurs with other usual usage.
Related Posts: