China Telecom continues to misguide and intercept Internet traffic

by chuttersnap
Software company · Blog operated by Oracle 's security team · Internet Intelligence Blog , China Telecom , the largest Internet operator in China, operates BGP , which is one of the routing protocols, to mislead Internet traffic · You are alerted to interception.
Chinaâ • Žs Maxim â • fi Leave No Access Point Unexploited: The Hidden Story of China Telecomâ "Žs BGP Hijacking
(PDF) https://scholarcommons.usf.edu/cgi/viewcontent.cgi?article=1050&context=mca
China Telecom's Internet Traffic Misdirection - Internet Intelligence Blog
https://internetintel.oracle.com/blog-single.html?id=China+Telecom% 27s+Internet+Traffic+Misdirection
Naval War University, an American naval college, discovered that China Telecom operates BGP and intercepts Internet traffic. BGP is a protocol for enabling Internet communication to be performed quickly even in distant areas. Researchers at Naval War university publish papers claiming that China Telecom has conducted a malicious method "BGP hijacking" that misguide the Internet route and intercept communication contents by utilizing this property doing.
While pretending that the Internet Intelligence Blog "will not touch on the argument written in the paper on the motive for intercepting traffic by the Chinese government," he says, "China China, the biggest carrier in China, is not intentional It is fact that it is wrong to make many destinations in Internet traffic in recent years, "he says that China Telecom has done BGP hijacking as a fact.
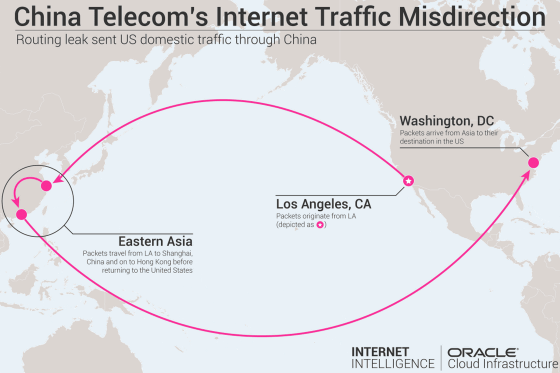
In the image below, the packet that should be sent from Los Angeles to Washington, DC is sent to the destination via Southeast Asian Shanghai and Hong Kong. This is a misdirection of the net route by BGP hijacking.
An example of BGP hijacking by China Telecom is a short route (less than 1 minute) experienced by Korean Internet service provider (ISP) SKBroadband (formerly Hanaro) on December 9, 2015 Routing) leak. Due to this incident, more than 300 routing via Verizon will end up knocking ASN to BGPstream, an open source BGP data analysis tool.
Woah, An the ASN In Korea Just Hijacked A Bunch Of Other ASNs Across APAC. Pic.Twitter.Com/46Ih5CaVmi
- Compose Button Richard Westmoreland (@ RSWestmoreland) December 9, 2015
Based on this route leak, SK Broadband (AS 9318) is using international carriers Telia (AS 1299), Tata (AS 6453), GTT (AS 3257), GTT It is clear that AS of Vodafone (AS 1273) is also passing. As a result, it seems that the worldwide network somehow sends traffic to Verizon APAC (AS 703) via China Telecom (AS 4134).
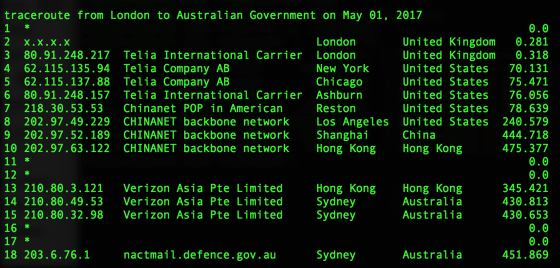
The following image shows the route that Internet traffic sent from London to the address belonging to the Australian government traced. Until then, even though it was the same recipient, it did not pass through China Telecom's network, which is not what resulted from China Telecom rerouting the route to intercept communication contents It is thought that.
In Oracle, it seems that Verizon and Telia have warned about this problem. Ultimately, Telia and GTT installed a filter to block communication via Verizon via China Telecom. As a result, we succeeded in reducing 90% of communication via China Telecom. However, it seems that it was impossible to shut off the route directly connecting to China Telecom.
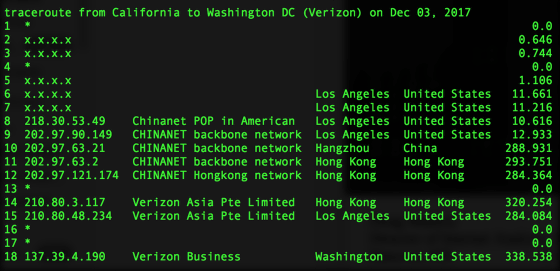
In the past year, Verizon APAC created a route called China Telecom (AS 4134) → SKBroadband (AS 9318) → Verizon APAC (AS 703) → Verizon North America (AS 701) and was flowing Internet traffic. As a result, it will flow to the AS 701 route via AS 4134, so even if you are sending traffic from the US to the US, the traffic flow is sent to China once. It is the major Internet infrastructure company in the United States affected by this.
A screenshot showing the fact that we have traced thousands of trace routes in China when traffic is actually sent from Verizon in the same country to the Verizon in the USA is the image below.
The Internet Intelligence Blog, which has long worked on the problem of BGP hijacking done by China Telecom, is working on Alexander Azimov of Qrator Labs and the development of (PDF) IETF standard for RPKI based AS path verification. If we succeed in introducing such a mechanism, it seems possible to drop a BGP that uses an AS path that violates properties without a valley (PDF) based on the known relationship between AS, for example .
Related Posts:
in Security, Posted by logu_ii