The possibility that 120 thousand users' personal information leaked out from Facebook quiz app

By Book Catalog
From the applications available on Facebook, it turned out that personal information was in a state of leakage again. Although the problem has already been resolved, there is a possibility that personal data of 120 million people was leaked.
This popular Facebook app publicly exposed your data for years
https://medium.com/@intideceukelaire/this-popular-facebook-app-publicly-exposed-your-data-for-years-12483418eff8
This problem was discovered by Mr. Inti De Ceukelaire ("Inti") who himself appeared as "hacker". It is pointed out that an application called "NameTests" of the German application development company Social Sweethearts had acquired user's name, birthday, photo, friend's name and included it in the JavaScript file.
NameTests said that they provided quizzes titled "Which Disney Princess Are You?" (Which Disney Princess?) On SNS.
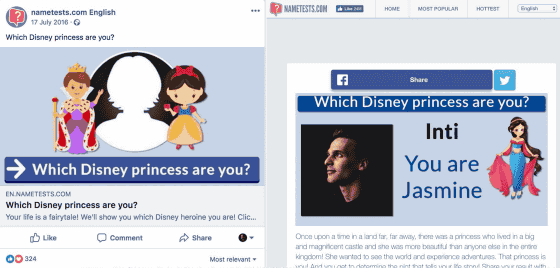
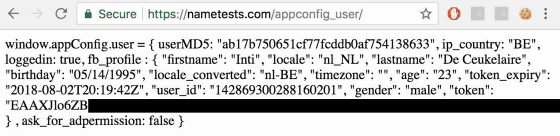
When a user tries to use NameTests from the Facebook application, the user is asked to log in by accessing the site "nametests.com" which is providing quizzes. At this time, if you choose the method of logging in with your Facebook account the same way that other applications use it, the site gets the necessary information to login from Facebook, but the user The following information about JavaScript was written to the JavaScript file. In this state, another site opened in the same browser accessing NameTests could access the relevant JavaScript file and see the contents.
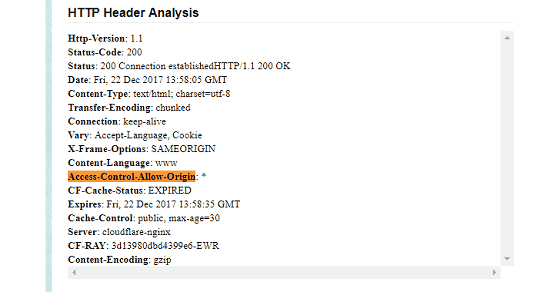
Since the Cross-Origin Resource Sharing (CORS) policy sharing (CORS) policy is applied to the browser, tabs accessing another site can not readily see information on another tab Analyzing the HTTP header of NameTests, since the item "Access - Control - Allow - Origin" was set to "*" as a wildcard, another Name Origin (access source) It means that JavaScript file was ready to be accessed.
Mr. Inti reported on the issue on Facebook from April 22, 2018 to Facebook via "Facebook Data Abuse Bounty, a personal data fraud reporting incentive program operated by Facebook. Later, on April 30th, Facebook received a response and he received reports that he was investigating the problem. Later on May 14th, when Mr. Inti contacted Facebook on the progress of the problem, there was a reply saying "It will take several months to investigate" on May 22nd, and Mr. Inti will be informed Mr. Inti about progress Reply. Finally, on June 25, Inti confirmed that the improvement was done at NameTests and the problem that third parties were looking at personal information was resolved.
In this case, Inti earned the right to receive a reward of 4000 dollars (about 440,000 yen) according to Facebook regulations. However, since Mr. Inti elected to donate its entire amount to "Freedom of the Press foundation", this also donates twice as much as $ 8000 (about 880,000 yen) to the foundation It was said that it was decided.
When Mr. Inti publishes this matter, Facebook releases an entry stating that the problem was solved as follows. While Mr. Inti feels pleasure about the problem being solved by the report of himself, it has a complex emotion that such an unacceptable event is leaning over 100 million users It is said that.
Data Abuse Bounty report results in fixed third-party bug
Posted by Facebook Bug Bounty Thursday, June 28, 2018
We wanted to call out a fix by nametests.com that happened ...
Related Posts:
in Web Service, Security, Posted by darkhorse_log