Honda's overseas affiliates had disclosed over 50,000 customer information on the cloud

Indian corporation of automaker "Honda"Honda Cars IndiaSo, an application that works with carsHonda ConnectWe are offering. The IT company says that "more than 50,000 personal information of users who are registered in this application has been published on the cloud service"KromtechSecurity Department "Kromtech Security Center"Announced on May 30, 2018.
Honda leaked personal information from its Honda Connect App
https://kromtech.com/blog/security-center/honda-leaked-personal-information-from-its-honda-connect-app
Honda India Left Details of 50,000 Customers Exposed on an AWS S3 Server
https://www.bleepingcomputer.com/news/security/honda-india-left-details-of-50-000-customers-exposed-on-an-aws-s3-server/
Honda Connect is an application for smartphones and mobile devices provided by Honda Cars India. By cooperating with the application and the Honda car, it is possible to grasp the information of own car through the application. Confirming the remaining amount of fuel of the Honda car owned by the user and warning of the engine temperature, sending warning of maintenance state, recording driving information, sending mail of vehicle position information, sending a signal to Honda's call center at the time of accident, You can use functions such as navigation linked with map application.
Honda Connect

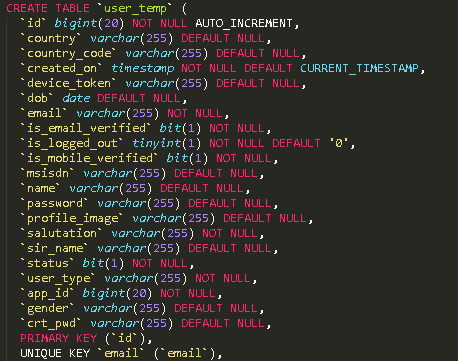
The data that was ready to view is the name registered in the application · phone number · password · gender · mail address · contact information. Also included vehicle identification number and access ID of information on cars.
Where Kromtech experts found the customer information database, the web storage service on Amazon AWS S3. The data leaked out was not a problem on Amazon, but because Honda Cars India had set the "Buckets" setting in the directory where data is saved to "open state" for anyone to browse. Among the two buckets in the open state, Honda Connect's user data totaled more than 50,000 people in total.
If these information leaks out to the malicious attacker, it may be possible to access all the smartphones listed in the database. In addition, if the leaked smartphone information and the car are paired, many user actions are tracked. The attacker can grasp where the user started and stopped driving the automobile, so from the use history of the automobile, knowing the user's daily activities such as the residence, work, shopping, playing place of the car owned by the car etc. I can.
In the event that these personal information leaks, malicious attackers may not be dangerous to impersonate a leaked contact and risk sending fraudulent mail or malware e-mails that deprive the device's access rights.

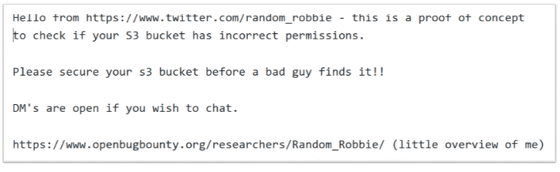
Before Kromtech experts browse this database, we know that there was at least one other viewer. Because, when Kromtech experts discovered this public database, security researcher Random Robbie (@ Random_Robbie) Because it contained a file with a time stamp of February 28, 2018 called "poc.txt" that Mr. left behind. In other words, Honda Car India did not care about the bucket containing this database and did not notice that this file was left in the bucket.
Kromtech experts told Honda Cars India about the state of the public database. Kromtech's Diachenko said "Honda Cars India protected the database about two weeks after notice"Bleeping ComputerCommented on.
So, finally,@ HondaCarIndiasecured those two buckets (that I know of). Thank you to my followers, and specifically to@ Random_Robbieand@ fs 0 c 131 yfor assisting in getting@ Hondaattention on this issue. We will publish incident report shortly.pic.twitter.com/74 PIhorIuw
- Bob Diachenko (@ Mayay DayOne)May 29, 2018
Related Posts:
in Mobile, Software, Web Service, Vehicle, Security, Posted by darkhorse_log







