Application developers warn that "the parties you are interacting with by SMS may be totally different people"

The situation that "the other party who is constantly exchanging messages with SMS is a completely different person, in fact it was a malicious attacker" is a perfect fear, but if such an attack is done by smartphone application The iOS application developer is warning. The risk of this type of attack exists in both iOS and Android terminals as well.
Smartphone Security: You'll Never Guess Who Just Messaged You
http://jordansmith.io/address-book-contact-security/
Warning that iOS and Android terminals are attacking to impersonate others and send and receive messages with SMS or iMessage is warning that iOS software developersJordan SmithMr. According to Mr. Smith, there is a danger that the installation of a malicious app impersonates an acquaintance whose contacts are stored on the user's smartphone, and that messages will be sent and received. Naturally, a malicious attacker can merely impersonate others, it can pull out information and guide it to malicious content.
According to Mr. Smith, a series of attacks starts with a malicious application requesting "user's phone number" and "permission to contact" when installing or using the smartphone application. These authorization permissions themselves are done in many applications, and unlawful use is not done with only this, but according to Mr. Smith, if you acquire the authority at the time of installing the application, it makes a conspicuous attack for a while He seems to be waiting.
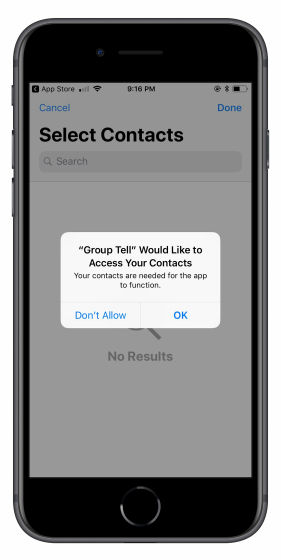
After a malicious app gets permission to access a contact, it sends the contact's data to the server and saves it. And when the time comes, we will add "additional phone number" secretly to existing contacts. Of course, this added phone number is to be exploited by a malicious attacker, SMS from that number is handled as "from acquaintance" and displayed in SMS application, so the user who received the message sent SMS It is difficult to notice that the subject who sent you is an attacker who masquerades as an acquaintance. Of course, you know that a person who speaks to you is exchanging messages with a "spoofed acquaintance" who does not know that a number that is not yours is added to a contact of another person's smartphone It is impossible. According to Mr. Smith, the attack application likes to use the contact information which is deeply related to the user as the attack target from the information added such as "Mama" "Papa" nickname among the contact information .
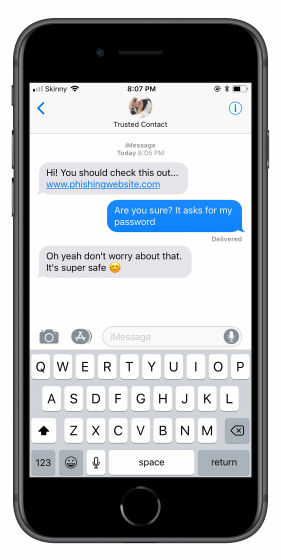
Mr. Smith has already reported possibility of attack against Apple and Google. Although he avoids explicitly about the name of a concrete application that exploits "message impersonating an acquaintance" pointed out by Mr. Smith, "Although it is an application installed several months ago, it can no longer be used on the App Store" And suggests that Apple's regulation of targeted applications is being done.
Mr. Smith says, "I will not mention the specific code to realize the attack, but the idea itself is simple and writing malicious code is easy to implement attacking function." The problem is that Mr. Smith thinks that iOS is able to manipulate both reading and writing with access to one's permission at the time of article creation and hence the root of handling of iOS and Android's permissions There seems to be a problem, and it seems that we have only to wait for improvement on this point. The thing that the user can do for self defense is to inadvertently not allow "access to contacts" to the application. Mr. Smith advises that if the major developer's application is not yet famous by smaller developers, even more vigilance is needed.
Related Posts:
in Software, Smartphone, Security, Posted by darkhorse_log