Google began testing for quantum computer era encryption technology at Chrome

ByHans Splinter
In March 2016A quantum computer with the ability to decipher the current encryption method in the future is bornThere was news that it did. In other words, it will come that someone will eventually break through the encryption method currently in use using a quantum computer. To prepare for the coming day, Google began testing encryption using Post Quantum Algorithm in Chrome's Canary version (a test version made with the latest source coat).
Google Online Security Blog: Experimenting with Post-Quantum Cryptography
https://security.googleblog.com/2016/07/experimenting-with-post-quantum.html
Google starts experimenting with quantum-secure connections in Chrome | TechCrunch
https://techcrunch.com/2016/07/07/google-starts-experimenting-with-quantum-secure-connections-in-chrome/
Safety is preserved in the current Internet,Public key cryptographythanks to. Its typical method isRSA encryptionAnd the basis of safety was in the part that "factorization of large number of digits is not easy to solve even with a supercomputer", but as the performance of quantum computers goes up, this grounds are fluctuating.
Since December 2015, Google began to address the problem of how to do "Public key cryptography in the quantum computer era", the most promising at that timeNew Hope algorithm"I took an eye out.
Post-quantum key exchange - a new hope
(PDF file)https://eprint.iacr.org/2015/1092.pdf
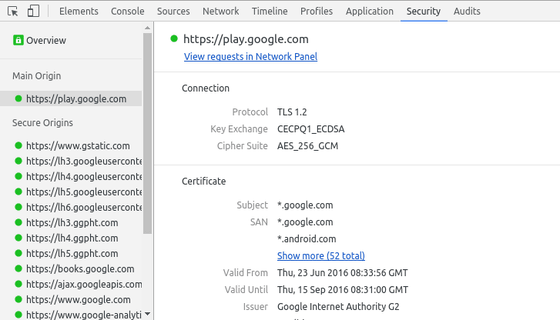
In the Canary version of Chrome, for example, if you access Google Play and the item "Key Exchange" on the security panel is "CECP Q 1", you are using the new encryption method.
However, after Google began this initiative, similar efforts are being made by semiconductor manufacturers NXP, Microsoft, the Netherlands theoretical computer science and mathematics division research firms Centrum Wiskunde & amp; Informatica, McMaster University, and even Google engineers We also started with a team that added and we are planning to complete the ongoing experiment within 2 years, as research is under way.
As a new network protocolQUICAlthough it developed and implemented, it is said that there is an intention not to create a new de facto standard (de facto standard) in encryption.
Related Posts:
in Software, Posted by logc_nt







