Discovery of anti-virus software by charging malware in PNG images in Android application is discovered

ByTechStage
We have found an Android application that embeds an encrypted "Trojan horse" in the PNG image included in Android application and avoids anti-virus software.
Android Malware: Android malware drops Banker from PNG file
http://b0n1.blogspot.jp/2015/11/android-malware-drops-banker-from-png.html
I am studying about malwareLukas StefankoIs in the file data of the PNG imageBase64It seems he found an Android application embedded with a Trojan horse of the encoding type. It is common practice that malware is hiding in files, but it is very unusual how to put encrypted viruses in images.
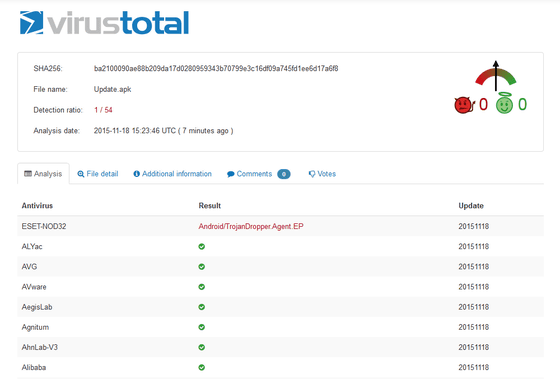
A free online service that inspects files using malware-embedded applications using over 40 anti-virus productsVirusTotal"It was revealed that most antivirus products were unable to detect PNG images embedded with viruses.
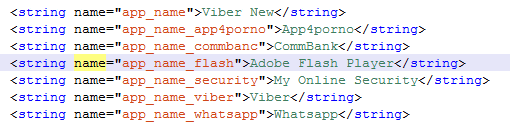
The first application discovered by Stefanko is a Trojan horse disguised as Adobe Flash Player, and other maliciously-named names such as Viber New, App4porno, CommBank, My Online Security, Viber, Whatsapp etc. I found that there are multiple applications that are hidden.
Looking at the file structure of the application, it seems that only the one image of the dice called "out.png" exists in the "assets" folder, but Stefanko is as large as 3.6 MB in file size It seems that it became anxious.
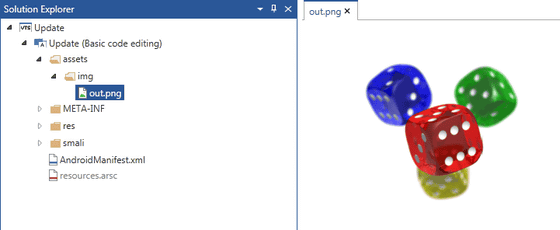
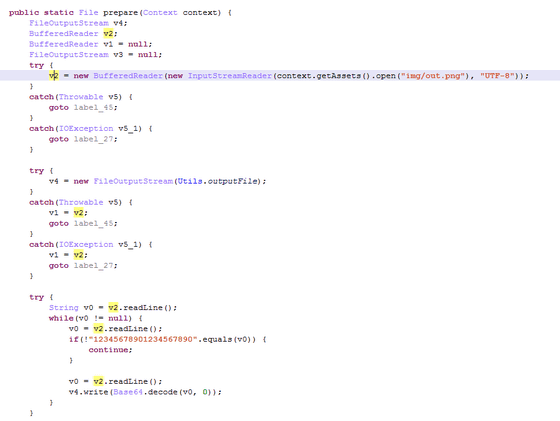
As a result of examination, if this PNG image is opened, the Trojan launches instead of displaying the image after checking the code and refers to the character string indicating the beginning of the data. In the image below "12345678901234567890" corresponds.
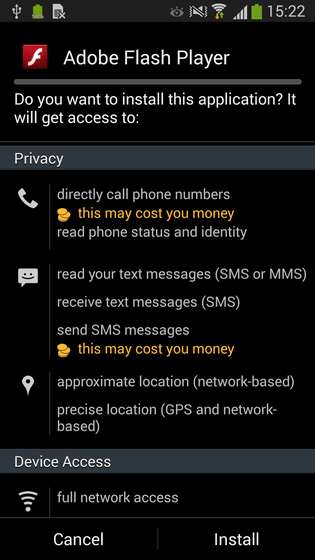
The character string is saved as "prefix.apk" in the external storage area of the smartphone and a request is displayed on the application to install Adobe Flash Player on the terminal.
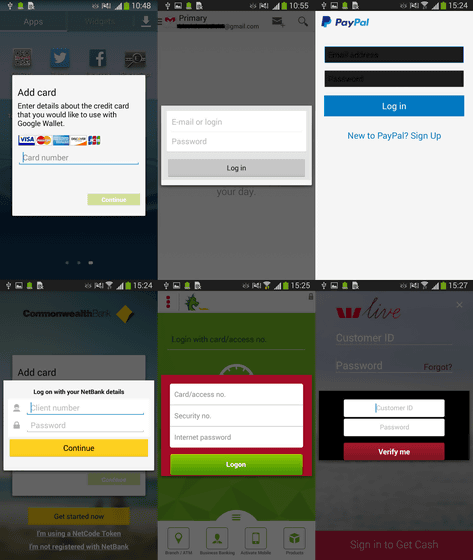
Once you install prefix.apk, your personal information such as credit card number and various account information will be stolen when opening the Google Play Store or bank mobile site.
The information stolen by the application is said to be transmitted to the server in text format in such a way that "Account name" "Password" "Service name" is seen as follows.
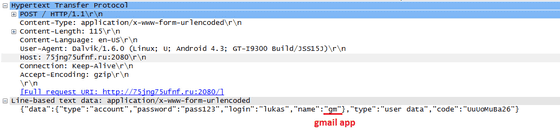
Also, because it is requested to grant administrator privileges to the application, it is difficult to uninstall the virus.
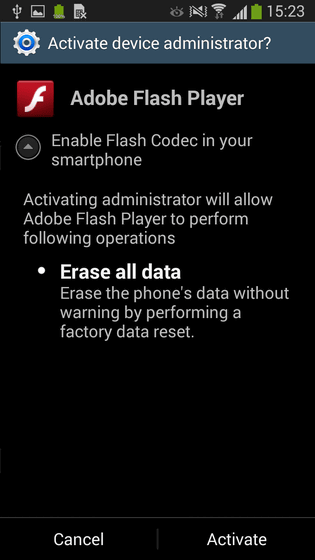
According to Stefanko, in order to avoid this virus, "Please move the terminal to safe mode, delete the administrator's privilege of the application and uninstall the application", or "Android Debug BridgeIt is possible to deal with in two ways, forcibly deleting an application using ".
Related Posts:
in Mobile, Web Service, Security, Posted by darkhorse_log