Clearly traceable methods revealed even if visitors are cutting cookies

ByAndy Arthur
Researchers announced that there is a way to know the domain and history of sites that users have visited before, even if cookies are deleted to prevent behavior tracking by websites.
Unpatched browser weaknesses can be exploited to track millions of Web users | Ars Technica
http://arstechnica.com/security/2015/10/unpatched-browser-weaknesses-can-be-exploited-to-track-millions-of-web-users/
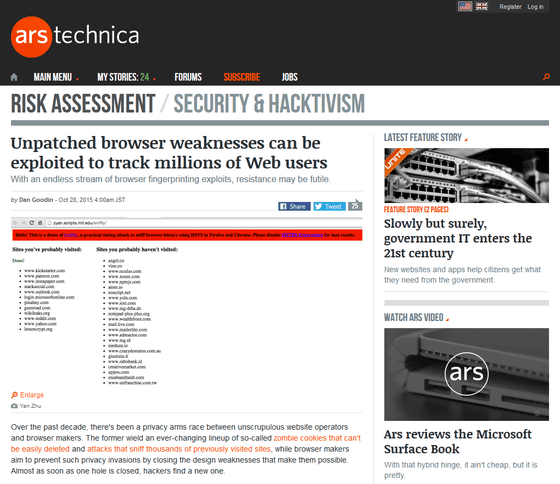
This is an independent researcher'sYan ZhuThinks "ToorCon: San Diego 2015What I told you in. A PDF file of the lecture at the time of the lecture can be downloaded from the following tweets.
Thanks for everything, toorcon! Browser fingerprinting slides up athttps://t.co/zwckiglcYR(Pdf)
- Yan ⚠ (@ bcrypt)2015, October 25
According to Mr. Zhu, the method is two, ironically, it is adopted by exploiting the new function installed in Chrome and Firefox.
The first oneHTTP Strict Transport Security (HSTS)History sniffing using sniffing (sniffing).
HSTS is a function to tell the browser that the website is "to communicate with HTTPS that is more secure than HTTP". In sites where security is required when accessing banks and so on, if the site side uses HSTS, once you access with HTTPS you will understand that the browser will use HTTPS instead of HTTP, so that security will be ensured Become.
An attacker can cause the target browser to load images from nonexistent sites that appear as "sites protected by HSTS". On the site, Javacript is used to measure how long it will take for an error to be displayed on image loading. If the user has accessed this "site protected by HSTS" in the past, the error will be displayed in a short time of milliseconds. However, if it takes time to display the error, you can see that the user never visited the site.
This case has already been communicated to the development team of Google as of September, but it seems that there is a reply saying that there is no plan to fix at the moment.
In fact, using this method, we make a site where Mr. Zhu is confirmed to disclose what kind of site visits it will be balanced. When you access the following URL with Firefox or Chrome, "Site you visited" and "Site that will not be visited" are displayed.
http://zyan.scripts.mit.edu/sniffly/
What code the site is running on is published on GitHub.
Diracdeltas / sniffly · GitHub
https://github.com/diracdeltas/sniffly
Another approach isHTTP public key pinning extension (HPKP)Used.
HPKP is a function used to prevent counterfeit certificates and secure public key reliability, and the browser stores the linking (pinning) information between the client's server and the public key for a certain period of time . By letting the browser remember the specific text that appears to be pinning information, an attacker can track the user's movements as if it were just loading the cookie. What you can do is the same as cookie, but as it is a certificate binding, the point is that this pinning information will remain even if the user deletes all cookies.
Adding / deleting the pinning information of the browser is possible by accessing "chrome: // net-internals / # hsts" if it is chrome, but it is necessary to put in the domain name at the time of deletion, You do not have a means to display a list of "Do you remember?"
Another way to delete pinning information is to delete all the information stored by the browser, but if you are using login information and history, convenience will be greatly compromised.
For now, the information "eavesdropped" by these two methods is a category that can be said to be quite useful compared with the conventional attack, for example, not all URLs are seen in history eavesdropping by HSTS, HSTS Protected sites, and only domains and subdomains. It is believed that as more sites using HTTPS are used in the future, the attack time will increase more and more false positives judgment will increase and code improvement will also be overcome.
However, it is a threat that the weak point that newly threatens the people among the added functions aiming for security improvement is a threat, Zhu said "Some people think that it is in vain to take defensive measures in such a way I think that opinion is partly correct though it is not everything. "
Related Posts:
in Security, Posted by logc_nt