It was discovered that someone had hacked 10,000 routers without permission to increase security

by Peter Dahlgren
Malware that enters a user's network often uses the user's router to launch further attacks. However, the malware discovered by Symantec, called Linux.Wifatch , was found to have infected as many as 10,000 routers running Linux, but rather than exploiting it, it was found to be ``moving to increase device security.'' .
Is there an Internet-of-Things vigilante out there? | Communauté Symantec Connect
http://www.symantec.com/connect/blogs/there-internet-things-vigilante-out-there
Someone Has Hacked 10,000 Home Routers To Make Them More Secure - Forbes
http://www.forbes.com/sites/thomasbrewster/2015/10/01/vigilante-malware-makes-you-safer/
Malware called Linux.Wifatch was discovered in 2014. A security researcher noticed something strange in his home router and discovered a mysterious code in the software that said to connect to a P2P network made up of devices infected with Linux.Wifatch.
In April 2015, Symantec learned more about Linux.Wifatch and investigated the malware's impact on devices. During the initial investigation, Linux.Wifatch appeared to be an unremarkable piece of code, but as the investigation progressed, it became clear that Linux.Wifatch was more sophisticated than other malware's code. You will understand. Analysis of the code revealed that Linux.Wifatch is written in the Perl language, and once infected, the device connects to a P2P network and continues to receive updates to protect against threats on the Internet. .

'The more I researched Linux.Wifatch, the more I felt that something was wrong with this code,' says Symantec. Looking at the code, it appears that the Linux.Wifatch authors were trying to make malware-infected devices more secure rather than exploiting them. After that, Symantec monitored Linux.Wifatch's P2P activity for several months, but as expected, no malicious activity was found.
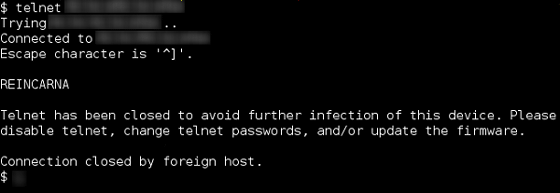
Aside from people with specialized knowledge, users of ordinary routers and IoT devices often have a hard time realizing that their devices are infected with malware. Linux.Wifatch not only prevents external access to the user's device, but also displays messages to the user asking ``Please change your password'' and ``Please update the firmware.'' It also contained a module that attempts to disable malware that is affecting the device.
Free software activist Richard Stallman signed a message at the end of every email he sends: ``To the NSA and FBI employees reading my email: Please learn from Snowden 's example to protect the U.S. Constitution from enemies both foreign and domestic.'' However, it seems that a comment similar to this message was also added to the Linux.Wifatch code. Additionally, while it would have been easy for the author to complicate the code, Linux.Wifatch is deliberately written simply to be easy to parse, and is not afraid of others casting doubt on the code. .
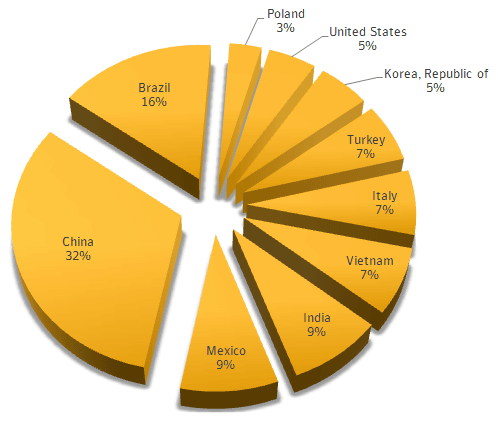
The percentage of countries where devices infected with Linux.Wifatch were discovered by Symantec is as follows. China has the highest number, followed by Brazil, Mexico, and India.
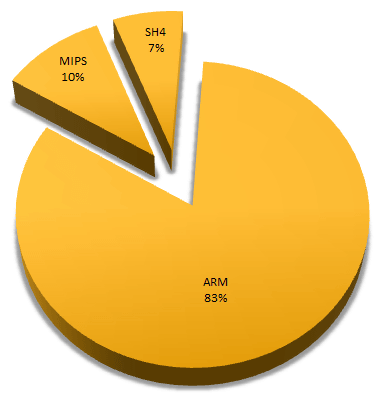
The architecture with the most infections was ARM, by an overwhelming 85%.
Perhaps it has hidden agendas, but from what Symantec has learned, Linux.Wifatch appears to be working like a comic book superhero to keep IoT device users safe. Masu.
However, even though the above-mentioned functions are acknowledged, it is true that Linux.Wifatch is a malware that affects the device without the user's permission. It is believed that the purpose is to prevent others from taking over the P2P network, but backdoors have also been discovered. Symantec says, ``We will continue to monitor the trends of Linux.Wifatch and the author so that we will be aware of any movements in the future.''
Related Posts:
in Security, , Posted by darkhorse_log