Vulnerability to control cars from smartphones is also discovered, demonstration of brake operation performed in Corvette is carried out

I am driving on a highway by remote controlExperiment stopping Jeep's air conditioner and cutting engineThere are great reactions,Discover vulnerability that takes over communication of smartphone and unlock car and engineSecurity issues of cars connected to the net are closing up, such as doing. In an experiment conducted by a research team, another new method has been reported that a command can be sent by smartphone SMS so that the vehicle's wiper and brake can be operated.
Hackers Cut a Corvette's Brakes Via a Common Car Gadget | WIRED
http://www.wired.com/2015/08/hackers-cut-corvettes-brakes-via-common-car-gadget/
The state that the wiper and brake of the Chevrolet · Corvette are actually being operated with the smartphone is introduced in the following movie.
Fast and Vulnerable - YouTube
The 2013 type Chevrolet Corvette was used for the experiment. The movie is titled "Fast, fragile car".

Although the detailed procedure is not described, firstly a message is sent from the smartphone to the Corvette. This corvette has a system that monitors the state and driving condition of the vehicle using a mobile phone network and it seems that a message is being sent to the phone number of the built-in SIM card.

And after 60 seconds ...
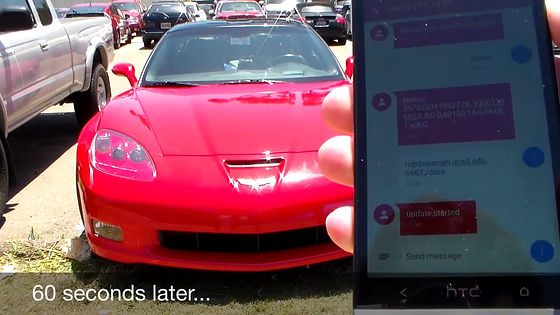
The message "Welcome to the Danger Zone (Welcome to the Danger Zone)" was displayed on the screen of the smartphone.
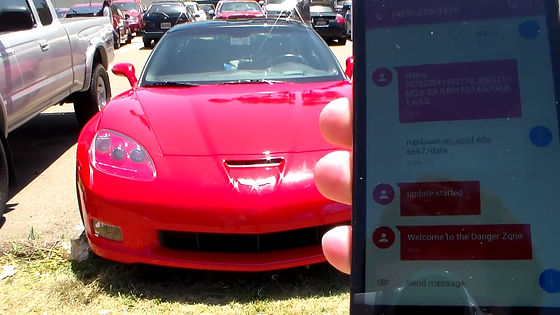
Then, the Corvette wiper began to move suddenly. It seems that nobody is inside the car, so the wiper started to move on its own.

Furthermore, experiments that brakes remotely. Sending SMS towards Corvette running at a slow speed ... ...

The brake stopped, the vehicle stopped. Of course the driver does not operate anything.

A scene containing the inside of the car. Sending a command via SMS in a slow corvette ......

Brake was applied with two sounds "Phu" and "Guoon". Note that this operation is designed to operate only when the vehicle is at or below 5 mph (approximately 8 km / h).

Moreover, it can also cancel the brakes.
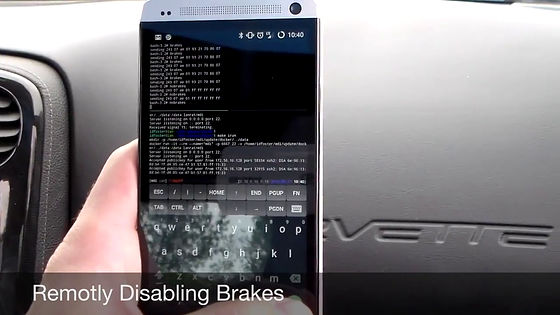
It is a car that the driver had stopped by stepping on the brake, but as soon as I sent SMS it started moving. At this time, it seems that the feel of the driver who stepped on the brake did not feel like moving the pedal at all.

This experiment was conducted by the research team of the University of California, Signature Diego (UCSD), and the results of the research will be held from August 12USENIX Security ConferenceIt is supposed to be announced at.
Home | USENIX
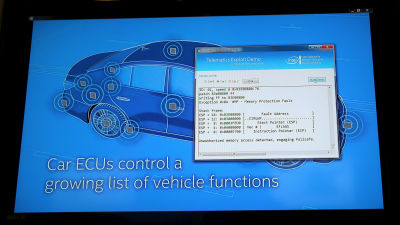
The mechanism of using the SMS to control the vehicle is by using a certain device installed in the dashboard of the car. Many of modern automobiles are not limited to the Corvette this time, but a self-diagnosis function for grasping the state and running condition of the vehicle "OBD 2This information can be retrieved by connecting a device called "dongle" to the connector installed in the dashboard. In UCSD, by connecting a unique dongle to the vehicle, a special SMS is sent from the smartphone to the vehicle and a command is sent to the system called "CAN bus" which manages the hardware of the vehicle via the OBD 2, and the wiper and brake are operated It seems that he succeeded in doing it.

Professor Stefan Savage, who studies computer security at UCSD, said: "We have found these security problems with equipment by getting these devices and reverse engineering, so that vehicles fitted with dongles We have found several ways to manipulate it. "
The research team used a French company "Mobile Devices"Developed by the American insurance-related startup"MetromileThe dongle provided by. Metromile is developing automobile insurance services according to mileage, and this dongle is adopted to grasp the detailed condition of the vehicle. Metromile provides a device called "Metromile Pulse" which sends data obtained by the dongle on the mobile phone network, and this experiment is applied to this experiment, but the same system is also adopted by Uber It is said that it is.
The research team has already notified Metromile of this problem and Metromile has already sent security patches to each device via mobile phone network and implemented it. Uber also informed each driver of the corresponding matter, but it seems that the problem which was concerned even before that was not reported.
However, it seems that it is too early to say that the problem on this matter has been completely solved yet, it seems that there are many terminals with security problems mainly in Spain. By sending an SMS to the phone number of the SIM card inserted in the terminal, "It is a mechanism to take over and the service companies have explained that there is no danger because the number of the SIM card is not disclosed" , UCSD researchers say that there is a method to guess a phone number by a malicious method, and point out that it is not a safe situation.
This problem is not limited to Chevrolet · Corvette but it seems to be able to be a problem potentially equipped in many of the vehicles equipped with OBD 2. Devices and applications that can grasp the state of the vehicle using OBD 2 are on the market in Japan, so it seems better to memorize the person in sight in the head.
Related Posts: