Subaru's connected car service 'SUBARU STARLINK' was found to have a vulnerability that could allow location information from the past year to be obtained and remote start, stop, lock, and unlock the car
Subaru offers a connected car service called ' SUBARU STARLINK ', but it was discovered that there was a security vulnerability that allowed unlimited targeted access to all vehicles and customer accounts. After being pointed out by experts, the vulnerability has already been fixed.
SUBARU STARLINK | SUBARU
Hacking Subaru: Tracking and Controlling Cars via the STARLINK Admin Panel
The problem was pointed out by security expert Sam Curry.
Curry had previously been investigating whether there were vulnerabilities in the services provided by automakers, but had not had the opportunity to investigate Subaru. However, about a year ago, his mother started driving a Subaru Impreza, and he began investigating Subaru's services around Thanksgiving in November 2024.
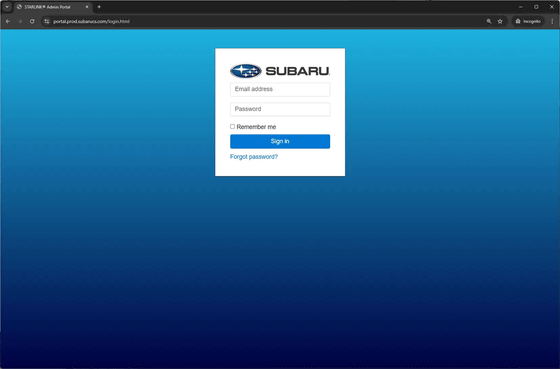
Curry says that when he first tried the My Subaru app, 'everything seemed to be properly secured,' but then his friend Shubham Shah gave him some unknown domains related to Subaru. He dug deeper and found what appeared to be an administrator portal.
Curry discovered a vulnerability in the JavaScript code stored in the portal service domain that allowed him to hijack valid employee email addresses, and after further investigation, he found he could view information about his mother's Impreza and remotely lock the cars of his acquaintances.
According to Curry, any attacker who knew 'the gender, zip code, email address, or license plate number of a customer account' could remotely start, stop, lock, or unlock the vehicle.
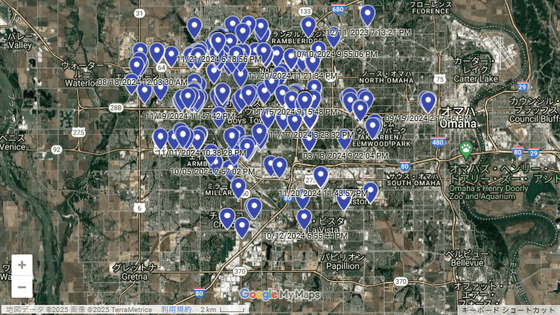
Additionally, the system was able to obtain vehicle location information, both current and for the past year, with an accuracy of within 5 meters.
In addition, it was possible to introduce and obtain personal identification information such as emergency contact information, addresses, the last four digits of a credit card number, and vehicle PIN, and it was also possible to access user data such as support call history, owner history, sales history, and mileage information.
The vulnerability was addressed within 24 hours of being reported by Curry in November 2024 and is no longer exploitable.
Related Posts:
in Web Service, Vehicle, Security, Posted by logc_nt






