Free car hacking manual "Car Hacker 's Handbook" is open now
ByIntel Free Press
Modern automobiles are becoming more computerized,Infotainment, Navigation system, Wi-Fi, automatic software update, etc. are becoming more convenient. However, these techniquescrackerIf it becomes a target of, the danger of being taken over quickly is high, and it is the present situation that it is not matured in terms of security. "Free of charge"Car Hacker's Handbook"Computer system installed in the car andEmbedded softwareAccording to Craig Smith, author of the book, by disclosing this technology, it is possible to improve the security of cars to be developed in the future and to train new engineers It seems that it aims to prompt
Car Hacker's Handbook
http://opengarages.org/handbook/
Access the above URL and scroll down.

You can read "Car Hacker's Handbook" by clicking "View Book Online".

The table of contents of "Car Haker's Handbook" is as follows.
◆ Chapter 1 Understanding the Threat Model
◆ Chapter 2 Bus Protocol
◆ Chapter 3SocketCANIn-vehicle communication using
◆ Chapter 4 DiagnosisLogging
◆ Chapter 5CANof the busreverse engineering
◆ Chapter 6ECUhacking
◆ Chapter 7 ECUTest benchHow to build and use
◆ Chapter 8 How to Attack ECUs and Other Embedded Systems
◆ Chapter 9 Automotive Infotainment System
◆ Chapter 10Inter-vehicle communication
◆ Chapter 11 Using the contents of CAN investigation in practice
◆ Chapter 12 Attack Using Software Radio
◆ Chapter 13 Performance Tuning
The purpose of the "Car Hacker's Handbook" is written in the foreword, mainly "Understanding the car system" "Verifying the security level of your car" "Broad publicly disclosed attack techniques written in this book By doing so, technical assistance to automobile manufacturers "is mentioned.
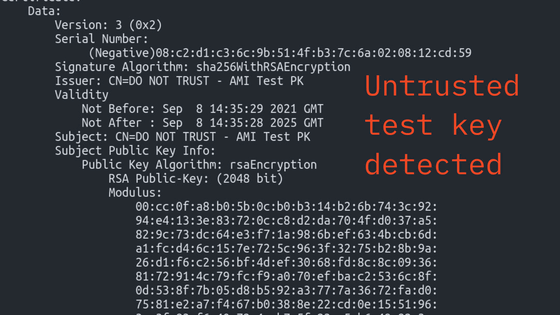
In chapter 1, we describe the method of evaluating the safety of a car and the fragile part of the in-car system. It is very useful to have this point of view when working at a car maker.

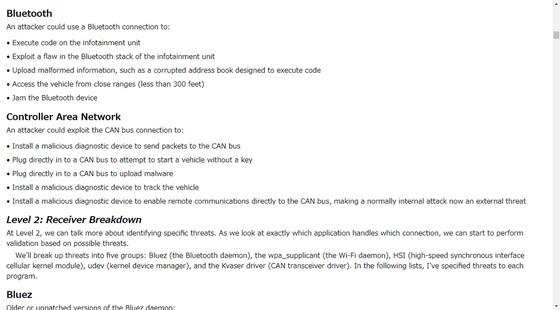
For example,BluetoothIf you exploit misuse, it seems that you can execute a special code with Infotainment Unit or access the vehicle from a distance of about 90 m radius.
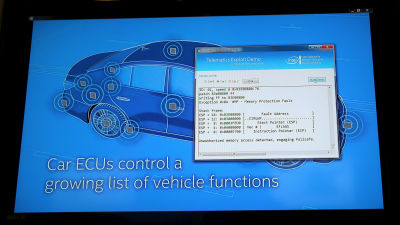
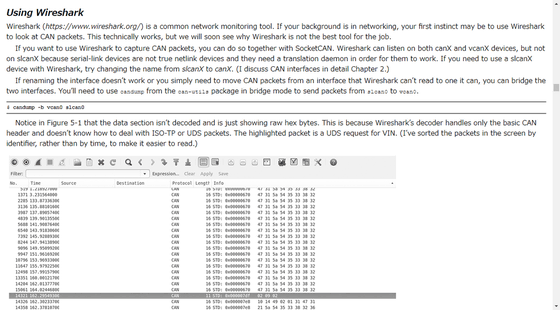
In Chapter 2, in the car networkpacketThis section explains the bus protocol for transfer.

In Chapter 5, reverse engineering of the CAN bus which is the main bus protocol of the car ... ...

WiresharkThe packet analysis method, etc., which is used, is mentioned.
In chapter 9, we describe attacks that exploit system updates against automotive infotainment systems.
Also, in Chapter 13 "Performance Tuning", even when tuningTrade offDepending on the precautions such as not necessarily achieving the best result and the specific tuning, ECU tuning method etc. are introduced.

In addition, when actually doing the contents described here, "Unauthorized Computer Access Prohibition ActThere is a possibility that it may be regulated by such as, or you may accidentally destroy the car. It seems that it is good to treat it as technical data to the last.
Related Posts:
in Software, Web Service, Hardware, Ride, Posted by darkhorse_log