`` GeekTyper '' that anyone can easily feel the feeling of a super hacker who can pass through transcendence security

Steal all the information in one PC, from being Furumae as of God in the IT society
NEW HACKERTYPER-GeekTyper
http://fediafedia.com/geektyper/

By using 'GeekTyper', you can feel the feeling of a hacker like the following movie.
I tried to feel the hacker feeling using `` GeekTyper ''-YouTube
That's why I decided to use it immediately. First, select the hacking screen from the GeekTyper top page. There are 14 themes, and you can use whatever you like.

The screen looks like this, and it looks like it's not likely to be hacked in the future.

To use it, just hit the keyboard freely. Then, the text will be input on the screen and the text that appears to be hacking will be automatically displayed on the screen.

When you press the enter key, 'ACCESS GRANTED' is displayed, and the screen switches to a windy screen in which something was successfully accessed.

Pressing the Enter key again fails access this time. The buzzing sound of the buzzer and security seems to be running away.
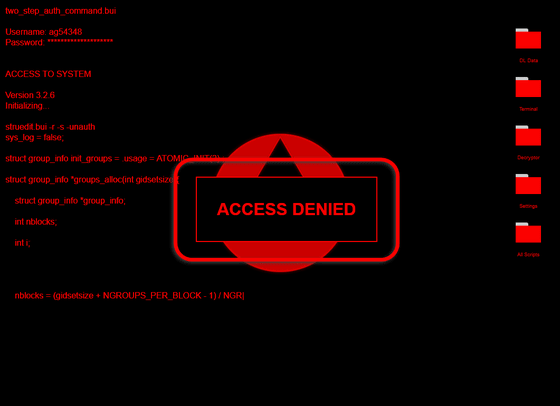
Click 'DL Date' on the screen to start downloading something.
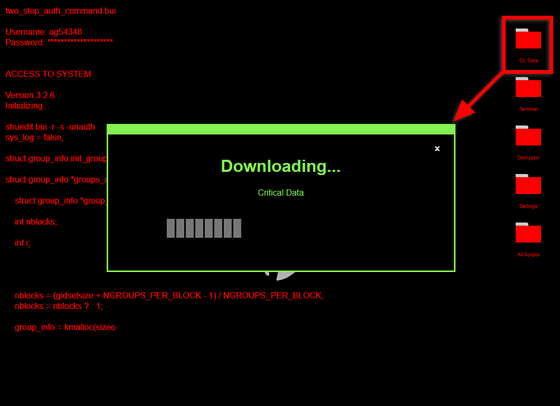
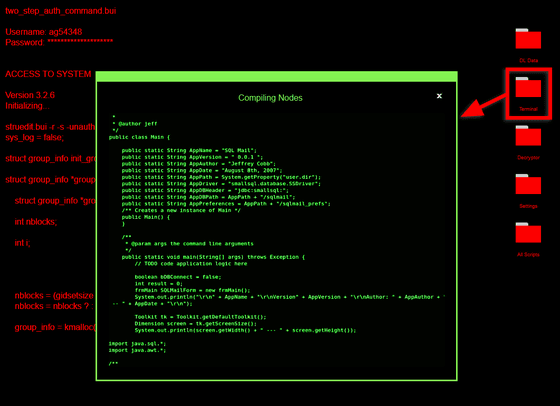
Click 'Terminal' to call the terminal.
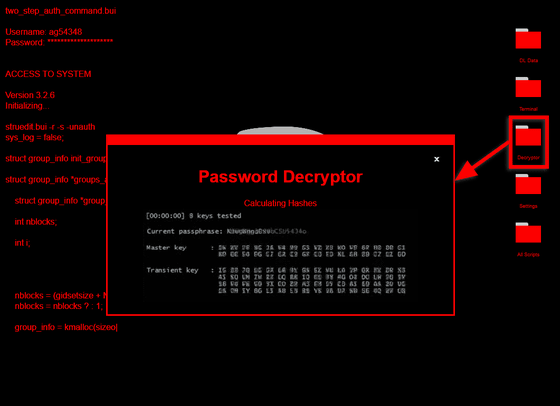
And if you click 'Decryptor', it will be like a screen cracking some kind of password.
Click “Settings” on the screen or press “Tab” key ……
An explanation screen will open that shows what you press on the keyboard and what you get. If you master the key operations here, you will be more likely to be a hacker, and your confidence in saying 'I understand all your address and name' will be greatly improved.
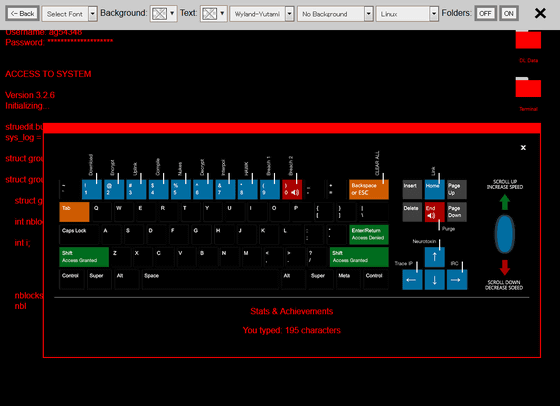
Various settings can be changed from the top of the explanation screen. For example, you can change the font of the text displayed on the screen from the `` Select Font '' on the left end, change the background, change the logo displayed in the center of the screen, the text displayed on the screen Can be freely selected from 'Linux' 'ASP.NET MVC' 'C ++' 'Python' 'Fortan' 'Nmap'.

When I change the logo in the center of the screen as a trial, it looks like this. At a stretch, the squattingness is improved and the hackeriness is increased.
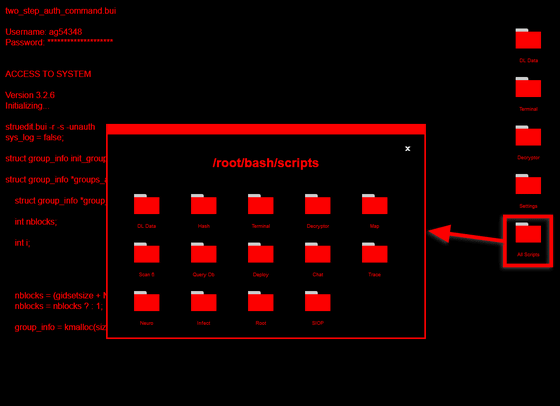
In addition, all hacking tools that can be used with GeekTyper can be displayed by clicking 'All Scripts'. In addition to decrypting and downloading files, you can use a variety of tools, so if you use it so far, you will no longer be able to fully enjoy the feeling of hacking alone.
There are 14 screens that can be used with GeekTyper, so it seems that they can be used properly according to
GeekTyper original 'GeekTyper Blue'.
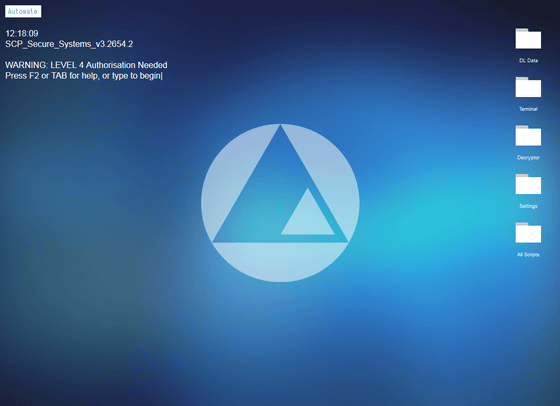
A windy 'SCP' that is invading somewhere in the security system

'Umbrella Corp' is a screen conscious of Umbrella, a fictional company that appears in the live-action movie version of Resident Evil. It could be possible to hack Umbrella and spread zombies all over the world.

'Aperture Science' appearing in the game '

`` Combine '' where a low-resolution background image creates a mood like that
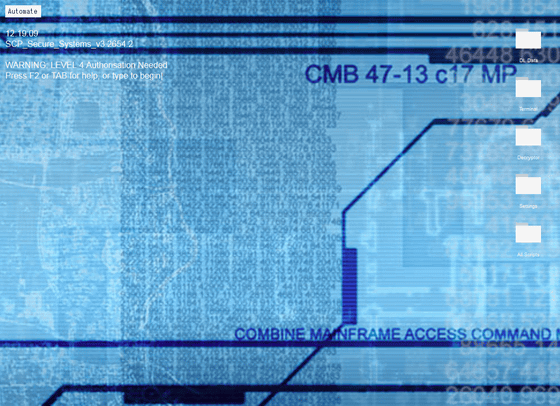
`` Black Mesa '', a remake MOD of Half-Life's masterpiece
'Plain Terminal', the most orthodox terminal screen

`` Matrix '' that can be hacked on a matrix-like screen

It is also possible to hack with the logo of the fictional agency 'Dharma' appearing in the overseas TV drama

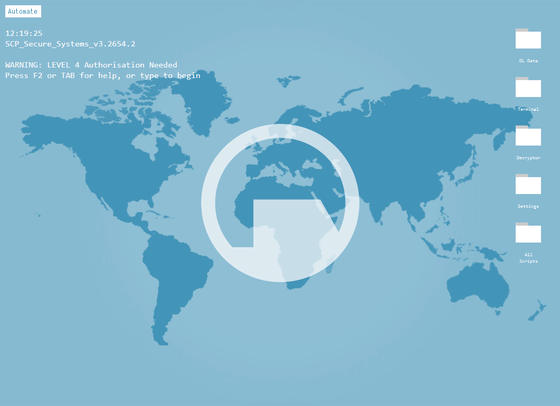
'Sliv'

'MLP Typer' is a screen image of

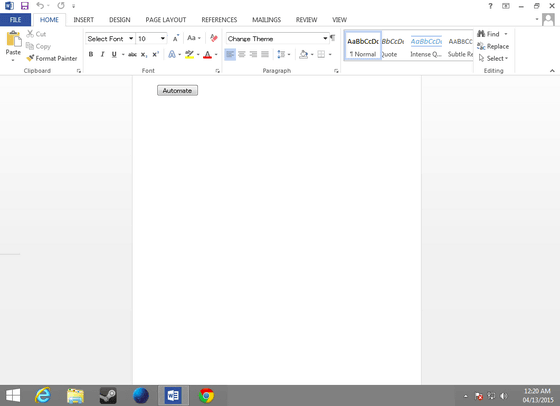
'Microsoft Word' that hacks from the Microsoft Word screen.
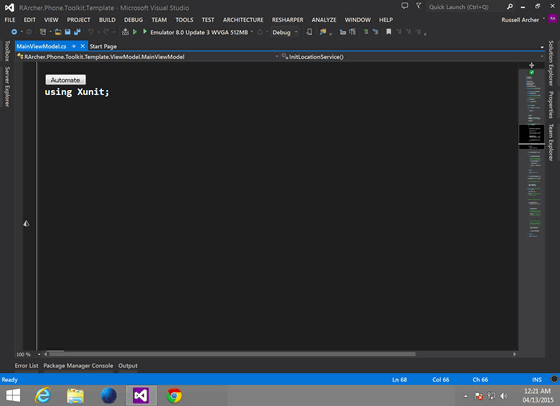
Microsoft development tool 'Visual Studio' style hacking screen.
If you use 'GeekTyper' in a public place, it's suspicious, so it seems better to choose where to use it carefully.
Related Posts:
in Video, Web Service, Review, Posted by logu_ii