What is the code name "Egotistical Giraffe" of NSA that attacks Tor users?

ByLennart Tange
It is one of the standards of net communicationTorIs a technology to enhance the anonymity of IP addresses where individuals are encrypted by encrypting the connection path from the source to the other party. Because of its high anonymity, it is said to be used for anti-social forces, but it was made clear by Mr. Edward SnowdenSpy activity by NSA, It turned out that an attempt was made to attack and decrypt Tor communication.
'Peeling back the layers of Tor with Egotistical Giraffe' - read the document | World news | theguardian.com
http://www.theguardian.com/world/interactive/2013/oct/04/egotistical-giraffe-nsa-tor-document
Secret NSA documents show campaign against Tor encrypted network - Washington Post
http://articles.washingtonpost.com/2013-10-04/world/42704326_1_nsa-officials-national-security-agency-edward-snowden
In October 2007, the National Security Agency (NSA) had a conversation with Tor developer, Roger DingledineNSA top secret materialIt is recorded in. Tor as a tool to preserve confidentiality of business and protection from tyranny and to conduct surveys without being noticed by opponents, Mr. Dingledine said "NSA officials will protect terrorists and monitored targets It seems that it looked like a tool. " At the same time, as pointed out that "NSA was trying to break through Tor", as confirmed in the leaked confidential document, it is known that the document showing Tor analysis by NSA was written.
[PDF] doc1-1.pdf
http://s3.documentcloud.org/documents/801433/doc1-1.pdf
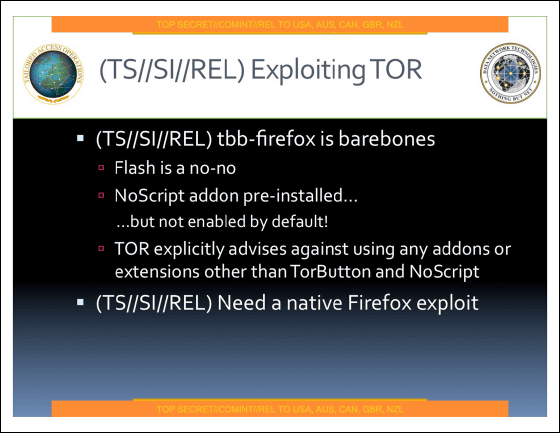
On the first page is entitled "Peeling Back the Layers of Tor with EGOTISTICALGIRAFFE (Egotistical Giraffe to strip Tor's encryption)".

On the second page is the letter "TOP SECRET".
The third page looks like the table of contents.
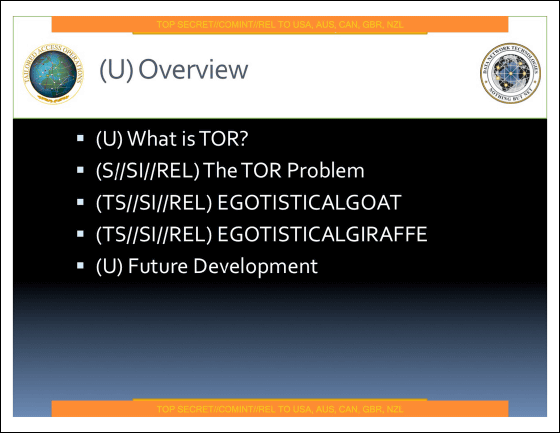
On the page titled "What is Tor?", It is an acronym for "The Onion Router", it provides anonymity on the Internet (confidentiality of IP address), and it is used for hundreds of thousands of users It is stated that "target" such as China, Iran, and terrorists are using it.
Tor also mentioned that it is necessary to break through Firefox itself (cracking) by using a browser based on Firefox as a tool.
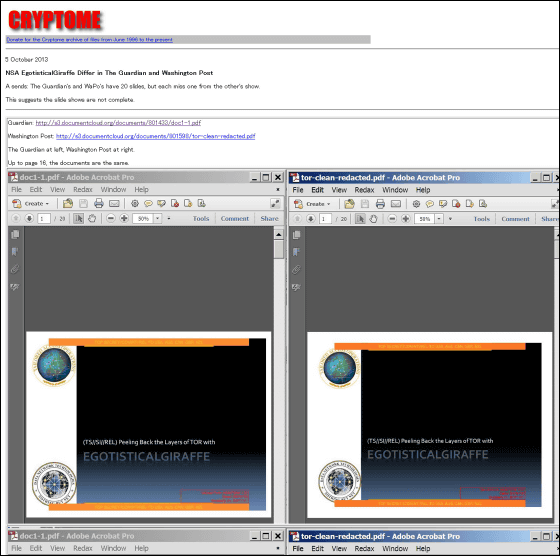
Unfortunately this document does not describe the detailed method of breaking through Tor, but if the description on the third page is a table of contents, the 20 page PDF document which was revealed this time is part of the whole It can also be read as if it implies that it is. In addition, it is also clear that the contents of documents published by The Guardian and Washington Post are different in the following site, and it is pointed out that the document is partially published.
NSA Egotistical Giraffe Differ in The Guardian and Washington Post
http://cryptome.org/2013/10/nsa-ego-differ/nsa-ego-differ.htm
In a confidential document revealed by Mr. Snowden, it is known that NSA had decrypted the source IP of several users by bypassing Tor's encryption system, and NSA has a strong encryption system Indicates that it has advanced ability to decipher it. In this case the code nameEgotisticalGiraffeIt has also been found that it was also used to elucidate the IP of the leading leader of al - Qaeda latent in the Arabian Peninsula. Also, if FBI reveals that Freedom Hosting was the world's largest child porn provider,When the founder of Silk Road of the online market, which had become a hotbed for illegal transactions, was arrested and the site was closedIt has become obvious that it was also used.
Garth Bruen, who lives in Boston and conducts internet crime research, says "Tor can be diverted to both good and bad purposes, just like any other internet tool, the point is that it is a problem on the side of use. If a criminal can master it, it will be like a nightmare. " Human rights promoters also say that "Tor is worthwhile, even if it is used for crime, it should be protected".The American Association for Freedom of Human RightsChristopher Soghoian says "Tor is one of the technologies of the network, it should be said to be equivalent to postage stamps and highways, both good and bad parties are the same as using highways" .
Related Posts:
in Note, Posted by darkhorse_log