Seven things you should know to use the anonymous communication system "Tor"

ByQuinn norton
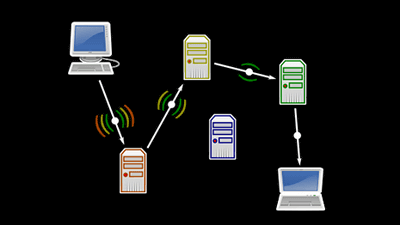
Tor(TOA) is an anonymous communication system that allows you to connect to the Internet and send mail without knowing the IP address of the other party. World famousBlack Hat Security conference, Lecture contents which invalidate Tor's encryption, as requested by a lawyer at the university where the lecturer is enrolledit was CancelledSometimes, it has spread to the security industry. Tor who is familiar with the Internet, I know Tor, I heard the name but there are a lot of people I do not know well in fact, and there are many people who do not know the existence itself, and activities on free rights of the digital society doingElectronic Frontier FoundationBut,"Seven things to know about Tor"Is released to the public.
7 Things You Should Know About Tor | Electronic Frontier Foundation
https://www.eff.org/deeplinks/2014/07/7-things-you-should-know-about-tor
◆ 1: Tor is still alive

ByPeddhapati
A system in which government agencies can access personal information from servers of net companies in Edward Snowden in 2013 "PRISMRevealed. About PRISM released by British information guards GuardianSecret documentIt was written that "I could not defeat the Tor user's anonymity." However, PRISM was operatingNSASucceeded in identifying Tor users under special circumstances. The situation is that of the Tor browserTor Browser BundleWhen a vulnerability is found in the browser, or when the user misconfigured the browser. For these reasons, the Electronic Frontier Foundation says "Tor is safe with respect to encryption, but we must be careful when browser bugs or configuration errors occur."
◆ 2: Only criminals are not using Tor

ByHeath Robinson
Among the misunderstandings that users have against Tor, there are a lot of people out there that "Tor users are mostly criminals". According to the Electronic Frontier Foundation, using Tor, such as activists use to avoid censorship, troops use to make secure communications, parents use it to protect children's privacy People who are not only criminals but people of various occupations are said to be. In addition to that, using Tor can also help protect you from criminals.
◆ 3: Tor does not have a military backdoor

ByMark Menzies
One thing the user misunderstood about Tor is that "Tor has a military backdoor". Although it is true that the US Navy contributed Tor development, investigation of experts and security researchers in encryption creation has denied the existence of backdoor.
◆ 4: People charged with operation of Tor server is zero in the US

ByJiva
To the extent that the Electronic Frontier Foundation knows, there are no people in the United States prosecuted because Tor Tor server was operated by 2014. The Electronic Frontier Foundation says, "We do not think that Tor server operation is against the laws of the US, but we can not guarantee that the action is legal if we are managing Tor's exit relays."
◆ 5: How to use Tor is very simple

ByEbayink
Although it seems that there are many cases that the impression of "Tor usage seems to be difficult" in many cases, the actual usage method is very simple. The easiest way to use Tor is "Tor Browser BundleDownloading a browser called ". How to use Tor Browser Bundle is almost the same as general browsers. Another simple way is to use Linux-based Live OS "TailsUse ". Tails erases everything running by the user at the end of the PC.
◆ 6: Tor is not late

ByDigon 3
It is a fact that connecting to the Internet via Tor will be slower than when connecting normally. However, many Tor developers are making daily efforts to improve the network speed. In fact the current connection speed is faster than before.
◆ 7: Tor is not perfect

ByNick
Tor will not be a perfect thing depending on how you use it. Therefore, it is very important to always use the Tor Browser Bundle or Tails and update the software to the latest version. Also, even if you log in to Google or Facebook via Tor, Google and Facebook can access your information.
Related Posts:
in Software, Web Service, Posted by darkhorse_log