"Cursor · camouflage" which displays a large amount of dummy mouse cursor and does not know where you clicked even if you peek over the shoulder

"Shoulder HackIn short, it is a primitive method of "stealing important information such as passwords by stealing the opponent's key type and display over the shoulder." It is powerful because it is very simple, such as PIN for withdrawing money from your bank account via ATM here and there, PIN for credit card that you are required to enter at shop payment, entrance lock on apartment There is always the danger of shoulder hacks in various situations, such as the release number of the bank card, and also the numeric keypad click via the on-screen bank keyboard in online banking.
Basically, "There is no defense method only to" be careful of the surroundings so that they can not be seen ", but finally it came here and finally got a revolutionary saying" I do not know where you clicked even if you shoulder hack " A countermeasure has appeared.
CursorCamouflage: Multiple Dummy Cursors as A Defense against Shoulder Surfing | Keita Watanabe
http://persistent.org/cursorcamouflage.html
CursorCamouflage: Multiple Dummy Cursors as A Defense against Shoulder Surfing - YouTube
People who are peeking from the top left are performing shoulder hacks

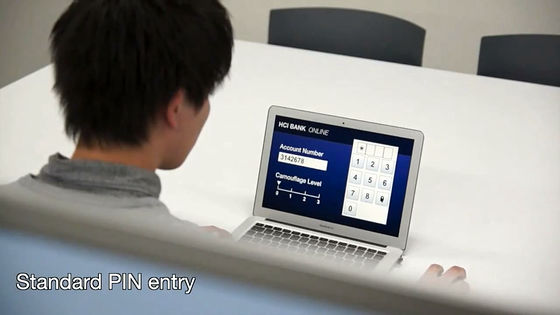
In this way, when clicking on the numeric keypad with the mouse and entering it, it is Morrobare where you are clicking
However, using the cursor · camouflage technique is like this, you can understand by actually playing the movie, but you can not understand exactly which cursor is the real monster from the end.

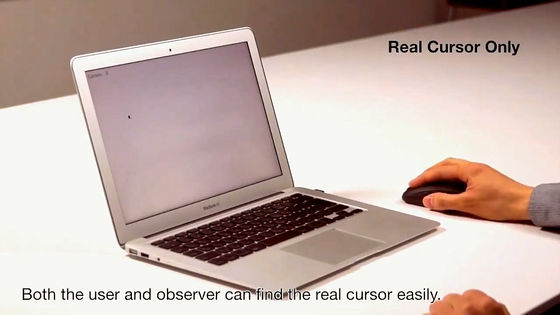
Principle is easy, First of all, if there is only one cursor in this way, both the principal moving the cursor and the third person observing the state from the edge can clearly see the movement of the cursor I will.
However, as soon as the dummy cursor scattered around the mountains and started to move ......
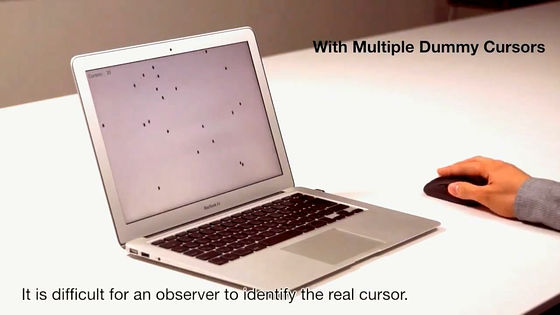
The principal moving the cursor can recognize that "this is the cursor of the real monkey" from the way of movement soon, but what comes from the third party is somehow somewhat.

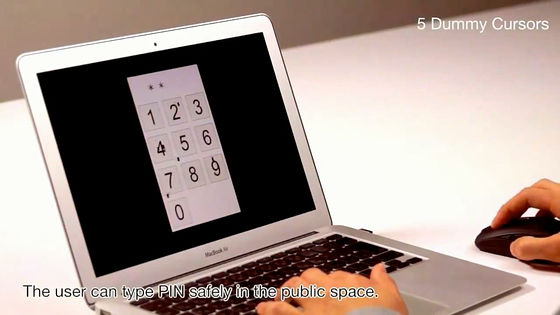
By applying this technology, we are safe and safe to enter PIN at public places. This is when there are five dummy cursors.
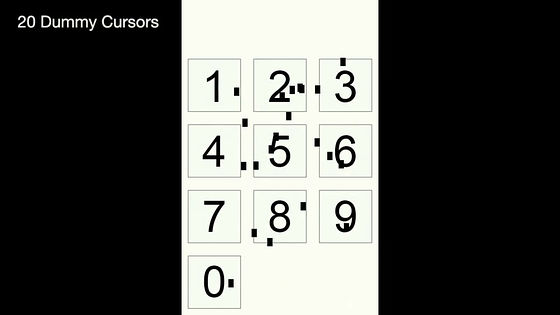
Increase to 20 more. It is as if the flies are flying around, but the principal can recognize without problems.

The movement of this confusing dummy cursor was reproduced by recording the movement when actually entering a numerical value. So, the way of movement is very real, it is very difficult to find out in the way of movement.

It also points to stopping in the same way if you stop the mouse cursor from moving.

It seems like this from the actual manipulating person
Even if the shoulder hack guru is observing the screen of your personal computer over the window with binoculars from the roof of the building opposite ... ....


To

Walla Walla Walla! Become impossible, shoulder hack becomes impossible.

Related Posts:
in Video, Posted by darkhorse