What is the "10 major threats" shown in the Information Security White Paper 2006 edition?

It is a good impression that we handle considerably timely story. It is a thing created by the Information-technology Promotion Agency of Japan, so it is well organized. We recommend following brief explanation and furthermore because it is possible to grasp the basic knowledge about security by quickly seeing the diagram summarized well visually. Information Security White Paper 2006 Edition - 10 Major Threats "Accelerate Economic Incidents" and Future Measures (PDF: 2.6 MB)
http://www.ipa.go.jp/security/vuln/documents/2005/ISwhitepaper2006.pdf
# 1 SQL Injection to Case
In 2005, similar incidents where major websites were targeted frequently occurred and became news.
Because "SQL injection vulnerability" was used as an attack method in some cases,
It became a topic as a keyword showing the case.
Because I do not know what it is in a sentence quote figure

I wonder what it is like. If you try to make sure the check is tight
It is possible to prevent to a certain extent.
2nd place Information leakage frequently caused by virus infection through Winny
Also in 2005, with virus using P2P file exchange software typified by Winny,
Information leakage from companies, organizations, etc. was conspicuous.
In addition to personal information such as roster and customer information, technical documents, confidential documents, photographs of digital cameras,
Information that leaked also varies.
Although it was reported in each news etc. until now, this figure is fairly easy to understand

3rd place Case of 'function similar to root kit' stored in music CD
A commercially available music CD, such as used for a malicious tool called "root kit"
There is a software which installs software having a function to hide a specific file on a computer,
It became a problem.
A diagram that explains the mechanism that the rootkit hides files, the "root kit weapons store" ...

Fourth place Phishing fraud which becomes malicious
On banks' websites, phishing fraud countermeasures have become common.
However, weasel has been followed by those who take countermeasures and attackers.
We have also found malicious cases of limiting targets to fraud by using acquaintances' names etc.
It is called "spear type phishing scam".
A figure that explains how it is going down in an interesting way, the next one is anxious ...

No. 5 sophisticated spyware
Attacks with psychological pitfalls of users such as installing software with linguistic words
Is increasing.
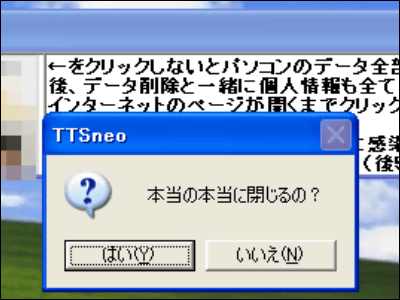
A so-called one-click fraud of unlawful billing screen merely by clicking a link
Increasing, spyware which we call spyware countermeasure software, etc. are appearing.
Why not hesitate If you actually out such screen because people who click the "OK" is often shock
No. 6 Bot which the trend continues
It infects via the network by various means such as virus mail and unauthorized access,
A bot (bot) continues to be popular, which starts attacks against others in accordance with an external command.
A figure of a bot network which is easy to understand, people who are on such a stepping stone are surely
I guess spyware is also infected with cancer ...

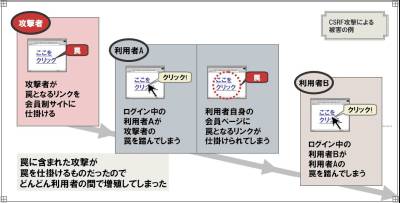
No. 7 CSRF epidemic aiming at website
The CSRF vulnerability is a link to a function such as "post" or "delete" provided on the website
By placing it as a trap, it is a problem that the user performs the function not intended by the user.
Although existence was known well, it is now used for attacks of actual websites.
The bulletin board and so on are quickly messed up when it is used
No. 8 Vulnerability hidden in embedded software such as information appliances and mobile devices
Among what is called embedded software, home appliances such as microwave ovens and video recording devices,
In mobile devices such as mobile phones, digital cameras, portable music players
Software that uses the network is not rare.
Therefore, threats in the world of computers, such as viruses and unauthorized access,
It is becoming a reality even in the world of embedded software.
It's certainly going to be a problem in the future

No. 9 vulnerability of security products
Throughout the year, various vendors such as intrusion detection systems and vaccine software
A serious vulnerability has been discovered one after another in the security products to be provided.
It's been a disastrous thing like OfficeScan
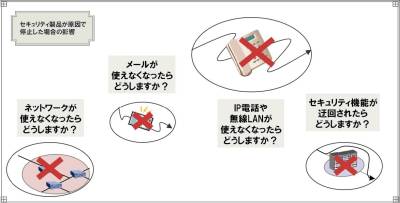
No. 10 Zero-Day Attack
The zero-day attack is a method of providing information such as workaround measures from the vendor and correcting methods before being released to the public
An attack is to be done.
At the end of 2005, a zero-day attack against a vulnerability with an unpublished and very broad influence was discovered,
It became a problem.
This "zero day attack" is a vulnerability in the example WMF file

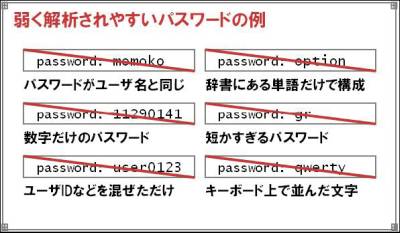
Other examples of weakly parsable passwords
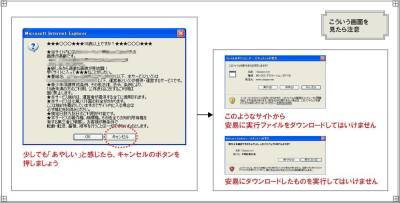
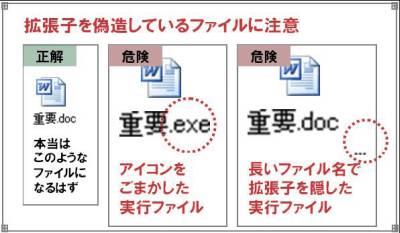
Be aware of files that are forged extensions
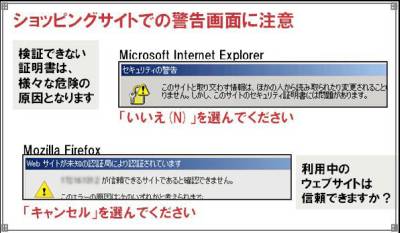
Attention to the warning screen at the shopping site
There are many very easy to understand commentaries, as well as many difficult terms, but I wonder if I can understand how much I can understand it. Also, it is a very useful document for commenting on people who do not know anything, this is.
Related Posts:
in Note, Posted by darkhorse_log