It turns out that popular sites such as GitHub and Vimeo were being exploited by a malware campaign with ``unprecedented'' obfuscation capabilities

Mandiant, a cybersecurity company affiliated with Google, has announced that it has identified a series of cyber attacks that involve complex combinations of seemingly harmless text files and random URL strings. Mandiant has confirmed that video sharing site Vimeo, software development platform GitHub, and popular IT news site
Evolution of UNC4990: Uncovering USB Malware's Hidden Depths | Mandiant
https://www.mandiant.com/resources/blog/unc4990-evolution-usb-malware
Ars Technica used in malware campaign with never-before-seen obfuscation | Ars Technica
https://arstechnica.com/security/2024/01/ars-technica-used-in-malware-campaign-with-never-before-seen-obfuscation/

Italian Businesses Hit by Weaponized USBs Spreading Cryptojacking Malware
The malware campaign Mandiant reported this time was carried out by the Italian-based cybercrime group UNC4990, which has been active since at least 2020. The main targets of UNC4990 are European and American companies, and the target industries are diverse, including healthcare, transportation, construction, and logistics.
The most notable feature of UNC4990 is its careful camouflage to make it difficult to detect, and Yash Gupta, a researcher at Mandiant, told Ars Technica, ``This is a novel method to disguise legitimate services. 'The exploit makes it very difficult to detect. This is something you don't see in normal malware, and this was very interesting to us and something we wanted to draw particular attention to.' .
The series of attacks can be broadly divided into three stages to covertly spread the infection, but the first stage is a very classic method of using a USB drive infected with malware. Mandiant calls this first stage malware 'Explorer.ps1.'

In parallel, seemingly innocuous posts are made to legitimate services such as Vimeo, GitHub, and Ars Technica. An example of this is shown below, where a random string of characters appears in the summary section of this

However, this string is actually a malware
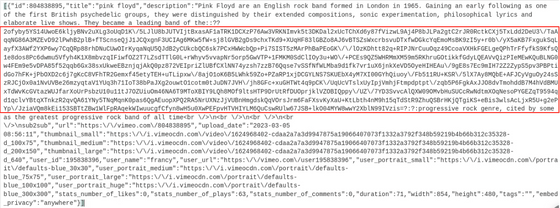
Once the above Vimeo post was removed, UNC4990 switched to exploiting news site Ars Technica. Viewers can leave comments on Ars Technica's articles, which requires user registration, but one user has pasted an introductory sentence saying ``I love pizza'' and an image of pizza.
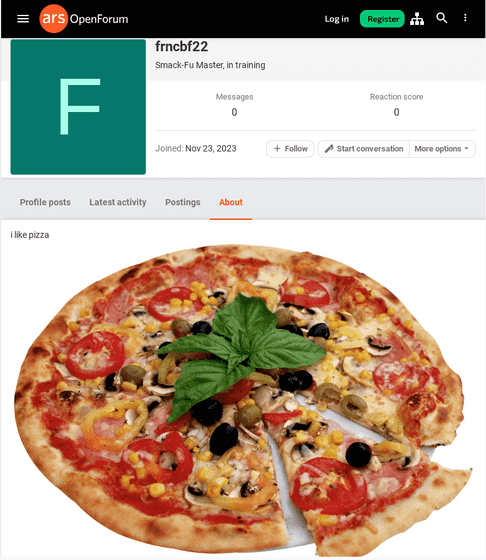
However, the URL used to paste this image was also loaded with malware. The only thing that is dangerous is the payload part after the '?' that is disguised as a URL parameter; the image or image URL itself is normal. As a result, the user account in question has already been deleted, but the image still has the URL 'https://purepng.com/public/uploads/large/purepng.com-pizzafood-pizza-941524644327twewe.png' at the time of article creation. You can access it safely from.

Mandiant said, ``The sites exploited by UNC4990, including Ars Technica, GitHub, GitLab, and Vimeo, were not vulnerable, and none of these entities made any mistakes that would allow the exploitation. , the content itself hosted on these legitimate services was completely benign and posed no direct risk to regular users of these services.'
The device thus exposed to the second stage infection called 'EMPTYSPACE' continuously queries the command and control server , and upon receiving the instructions, the device is infected with the third stage malware, which includes a backdoor called 'QUIETBOARD'. Download and run.
This 'QUIETBOARD' is a Python-based backdoor that can execute arbitrary commands, change the address of the virtual currency wallet copied to the clipboard and change the remittance destination to a UNC4990 wallet, and place malware on a removable drive. It was equipped with various functions such as collecting screenshots and system information.
'We observed a clear evolution of TTPs (Tactics, Techniques, and Procedures) from the early stages of malware campaigns to their current form,' Mandiant said in the report. The use of programming languages to create different EMPTYSPACE downloaders, and the switch to exploiting Ars Technica after the Vimeo post was deleted, demonstrate a tendency for attackers to experiment and adapt.' said.
Related Posts:
in Security, Posted by log1l_ks