When working on a job change assignment on a company PC, the entire company was actually damaged by an attack by the North Korean hacker group 'Lazarus'

It has been discovered that the North Korean hacker group 'Lazarus' poses as a Meta recruiter and poses as a coding challenge for job seekers, and installs the Trojan horse 'LightlessCan' on the PCs of job seekers. did. A case report compiled by ESET reveals that an employee at a Spanish aerospace company downloaded a fake assignment onto a company PC, resulting in a breach of the company's network.
Lazarus luring employees with trojanized coding challenges: The case of a Spanish aerospace company
Lazarus is a hacker group with North Korean backgrounds that has been involved in numerous cyberattacks, including the hacking of Sony Pictures Entertainment in 2014 and the development of the ransomware ' WannaCry ' that was rampant in 2017. is known. In addition, in 2022, the Financial Services Agency, the National Police Agency, and the Cabinet Cyber Security Center (NISC) described Lazarus as ``a cyber attack group known as Lazarus, which is said to be a subordinate organization of the North Korean authorities'' and linked it to North Korea. We have taken the unprecedented step of clearly declaring that
Regarding cyber attacks targeting crypto asset-related businesses, etc. by a cyber attack group called Lazarus, which is said to be a subordinate organization of the North Korean authorities (alert)
(PDF file) https://www.npa.go.jp/bureau/cyber/pdf/R041014_cyber_alert.pdf

Lazarus remains active as of 2023 and is constantly developing new attack methods. A new method reported by ESET is to ``pose as a recruiter at a major IT company and force job seekers to download coding assignments containing malicious files.'' The target of the attack was the person who was present.
Examples of damage are as follows. First, Lazarus members posed as Meta recruiters and contacted job seekers on the business-specific social networking service LinkedIn. Messages exchanged on LinkedIn show that the attacker, claiming to be Steve Dawson, a Meta recruiter, sent the victim a friend request and engaged in a friendly chat. I understand.
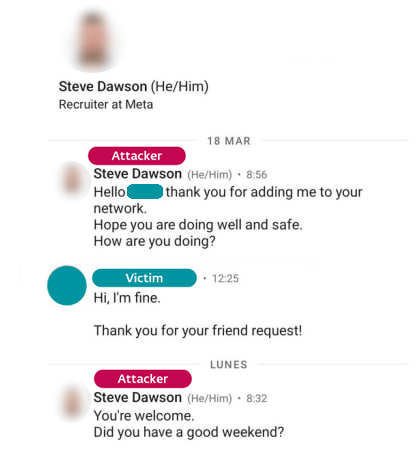
The attacker convinced the victim that he was a Meta recruiter and then asked them to complete a coding challenge for a recruitment exam. The coding assignment is ``Download and run an executable file, understand the logic, and write code with the same behavior in C++'', and the executable file for the assignment is ``Quiz1.exe stored in Quiz1.iso''. and 'Quiz2.exe stored in Quiz2.iso' are prepared. Quiz1.exe 'outputs 'Hello, World!'' and Quiz2.exe 'outputs the Fibonacci sequence.' It was said to be easy.

Quiz1.iso and Quiz2.iso have a built-in function that introduces malicious files in addition to the assignment executable file, and when the victim runs Quiz1.exe or Quiz2.exe to check the assignment content, the malicious file is installed. It was a system that was executed within the PC. The malicious file contains 'NickelLoader', which has the ability to download malware from the Internet, and as a result of NickelLoader being executed on the victim's PC, it becomes a remote access Trojan horse that Lazarus has used in the past. 'LightlessCan', the successor program of '
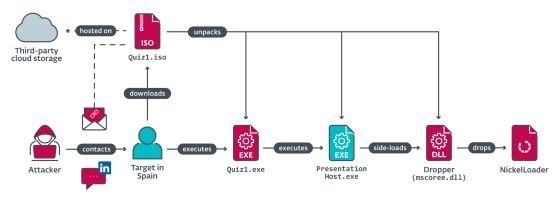
Lazarus, who succeeded in installing LightlessCan on the victim's PC, gained access to the network of the victim's aerospace company. ESET speculates that Lazarus' ultimate goal was cyber espionage targeting the aerospace industry.
Related Posts:
in Security, Posted by log1o_hf