What is 'Exotic Lily', a cybercriminal organization that is behind the global spread of ransomware 'Conti'?

Google's threat analysis group announces the method of cybercriminal group ' Exotic Lily ', which is said to be greatly involved in the trend of ransomware '
Exposing initial access broker with ties to Conti
https://blog.google/threat-analysis-group/exposing-initial-access-broker-ties-conti/
Google exposes tactics of a Conti ransomware access broker
https://www.bleepingcomputer.com/news/security/google-exposes-tactics-of-a-conti-ransomware-access-broker/
According to Google's threat analysis group, Exotic Lily exploits the zero-day vulnerability ' CVE-2021-40444 ' of the rendering engine ' Trident ' installed in Internet Explorer to target corporate networks by phishing . It is an access broker that breaks in and sells the information inside the network to the ransomware group. Exotic Lily sends more than 5,000 emails to up to 650 organizations a day, demonstrating the scale of its approach.
As a result of analyzing the behavior pattern of Exotic Lily, it was found that the activity time is from 9 am to 5 pm on weekdays in Eastern Standard Time, and it is hardly active on weekends. From this, it can be seen that Exotic Lily is not a disorderly gathering of free crackers , but a business form that receives salary by hacking the network under certain working conditions, just like a company. increase. In addition to just gathering information from the network, you can edit business proposal templates, register domains for spoofing, send emails using domains, upload malware payloads , build relationships with targets, and share links with targets. It is said that it is also doing steady work to collect information from the target network.
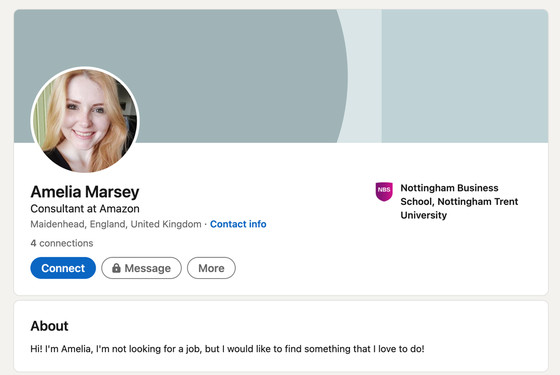
The phishing method by Exotic Lily is to let the target access the counterfeit site and download the malware, and the means of contacting the target is to use a public email address or the inquiry form of the website. In addition, it is said that LinkedIn , which is a business-specific SNS, may prove that it is working in a spoofed organization by using fake images generated by AI and photos of actual employees as they are.
A fake profile image actually created on LinkedIn
Exotic Lily emails serious business stories, such as emailing business suggestions and service requirements first to build relationships with targets, so that targets don't seem to be spoofing by cybercriminal organizations. Behave to. Then, when the target is alert, the attacker shares the malware download link via various file-sharing and cloud services.
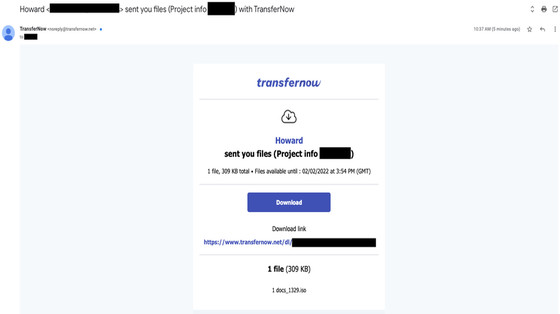
The malware distributed by Exotic Lily provides backdoor access called ' BazarLoader ', which was initially distributed as a forged document file, but recently it is in ISO format including DLL format files and shortcut links. It is distributed as an image file. Google's threat analysis group has been rampant as targeted ransomware in recent years Conti and Diavol are not used by Exotic Lily, but by another organization that purchased corporate network information and backdoor access from Exotic Lily. There is. Google's threat analysis group also suggested a relationship with a Russian cybercriminal group known as ' WizardsPider ' based on the malware and attack methods used.
Google's Threat Analysis Group is committed to sharing our findings to raise awareness of companies and individuals who may have been targeted or damaged by the activities of cybercriminal organizations. We hope that a better understanding of Exotic Lily's tactics and technologies will improve our ability to detect threats and enhance user protection across the industry. '
Related Posts:
in Security, Posted by log1i_yk







