Apple releases iOS 26.3

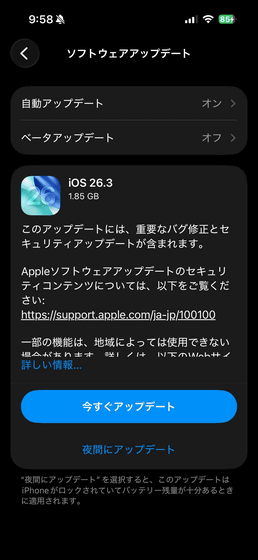
On February 11, 2026, Apple released the latest version of iOS, iOS 26.3 , and the iPad OS, iPadOS 26.3 . iOS 26.3 is 1.85GB in size and fixes several vulnerabilities.
About the security content of iOS 26.3 and iPadOS 26.3 - Apple Support (Japan)
Apple releases iOS 26.3 for iPhone, here's what's new - 9to5Mac
https://9to5mac.com/2026/02/11/apple-releases-ios-26-3-for-iphone-heres-whats-new/
You can update to iOS 26.3 by going to 'General' → 'Software Update' in the 'Settings' app. The file size is 1.85GB.
The vulnerabilities fixed by Apple are as follows:
CVE-2026-20645
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: Fixed a user interface inconsistency issue with improved state management.
CVE-2026-20674
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: Addresses privacy concerns by removing sensitive data.
◆CVE-2026-20650
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An attacker in a privileged network position may be able to perform a denial of service attack using crafted Bluetooth packets
Description: A denial of service issue was addressed through improved validation.
CVE-2026-20638
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: The identifying information of users who turn off the Live Caller ID app extension may be revealed to the extension
Description: Logic issues addressed through improved checks.
◆CVE-2026-20660
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: A remote user may be able to write arbitrary files
Description: Improved logic and fixed path handling issues.
CVE-2026-20611
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: Processing a maliciously crafted media file may lead to an unexpected application termination or process memory corruption
Description: An out-of-bounds access issue was addressed through improved bounds checking.
CVE-2026-20609
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: Processing a maliciously crafted file may lead to a denial of service or memory disclosure
Description: The issue was addressed with improved memory handling.
CVE-2026-20617
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An app may be able to gain root privileges
Description: A race condition was addressed with improved state handling.
◆CVE-2026-20615
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An app may be able to gain root privileges
Description: A path handling issue was addressed through improved validation.
CVE-2026-20627
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An app may be able to access sensitive user data
Description: An issue existed in the handling of environment variables. This issue was addressed through improved validation.
◆CVE-2026-20700
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An attacker with memory write privileges may be able to execute arbitrary code. Apple is aware of reports that this issue may have been exploited in highly sophisticated attacks targeted at specific individuals in versions of iOS prior to iOS 26. Following this report, CVE-2025-14174 and CVE-2025-43529 were also made public.
Description: Improved state management to address memory corruption issues.
CVE-2026-20649
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: A user may be able to view sensitive user information
Description: Addressed a logging issue with improved data editing.
◆CVE-2026-20675
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: Processing a maliciously crafted image may lead to the disclosure of user information
Description: This issue was addressed through improved bounds checking.
◆CVE-2026-20634
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: Processing a maliciously crafted image may lead to the disclosure of process memory
Description: The issue was addressed with improved memory handling.
◆CVE-2026-20654
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An application may cause an unexpected system termination
Description: The issue was addressed with improved memory handling.
◆CVE-2026-20626
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: A malicious application may be able to gain root privileges
Description: This issue was addressed with improved checks.
CVE-2026-20671
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An attacker in a privileged network position may be able to intercept network traffic
Description: A logic issue was addressed with improved checks.
◆CVE-2026-20663
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An app may be able to enumerate a user's installed apps
Description: Issue resolved by sanitizing logs.
CVE-2025-59375
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: Processing a maliciously crafted file may lead to a denial of service
Description: A vulnerability in open source code affecting Apple software among other projects. More information on this issue can be found at cve.org .
CVE-2026-20667
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An application may be able to escape the sandbox
Description: Logic issues addressed through improved checks.
CVE-2026-20655
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: Authorization issue resolved through improved state management.
CVE-2026-20677
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: A shortcut may be able to bypass sandbox restrictions
Description: A race condition was addressed through improved handling of symbolic links.
◆CVE-2026-20642
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: A person with physical access to an iOS device may be able to access photos from the lock screen
Description: Addressed an input validation issue.
◆CVE-2026-20628
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An application may be able to escape the sandbox
Description: Addressed a permissions issue with additional restrictions.
CVE-2026-20678
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An app may be able to access sensitive user data
Description: Addressed authorization issue with improved state management.
◆CVE-2026-20682
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An attacker may be able to discover a user's deleted notes
Description: Logic issues resolved through improved state management.
◆CVE-2026-20653
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An app may be able to access sensitive user data
Description: A parsing issue in handling directory paths was addressed and path validation was improved.
CVE-2026-20680
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: Sandboxed apps may be able to access sensitive user data
Description: This issue was addressed with additional restrictions on the observability of application state.
CVE-2026-20641
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An app may be able to identify other apps the user has installed
Description: Addresses a privacy issue with improved checks.
◆CVE-2026-20606
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An app may be able to bypass certain privacy settings
Description: This issue was addressed by removing the vulnerable code.
CVE-2026-20640
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An attacker with physical access to an iPhone may be able to take and view screenshots of sensitive data from an iPhone when mirroring it on a Mac.
Description: Improved state management addresses inconsistent user interface issues.
CVE-2026-20661
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: Addressed authorization issue with improved state management.
CVE-2026-20652
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: A remote attacker may be able to cause a denial of service
Description: The issue was addressed with improved memory handling.
◆CVE-2026-20608
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: Processing maliciously crafted web content may lead to an unexpected process crash
Description: Resolved by improved state management.
CVE-2026-20676
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: Websites may be able to track users through Safari web extensions
Description: Resolved by improved state management.
◆CVE-2026-20644, CVE-2026-20636, CVE-2026-20635
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: Processing maliciously crafted web content may lead to an unexpected process crash
Description: The issue was addressed with improved memory handling.
CVE-2026-20621
Compatible models: iPhone 11 and later, iPad Pro 12.9-inch (3rd generation and later), iPad Pro 11-inch (1st generation and later), iPad Air (3rd generation and later), iPad (8th generation and later), iPad mini (5th generation and later)
Impact: An application may cause an unexpected system termination or kernel memory corruption
Description: The issue was addressed with improved memory handling.
iOS 26.3 also adds an easier way to switch from Android to iPhone, and adds astronomy and weather wallpapers.
The beta version of the next major version, iOS 26.4, is scheduled to be released in the last week of February 2026, and it is planned that Siri with Gemini will be released in this version.
Apple pays Google 150 billion yen a year to adopt Gemini's custom model for the new Siri - GIGAZINE

Related Posts:
in Software, Smartphone, Security, Posted by logu_ii