Notepad++ was hijacked by state-sponsored hackers to distribute malware installers

There has been a continuing problem where traffic from WinGUp , an updater for the text editor Notepad++ , was being redirected to malicious domains and distributing malware, and it has now been revealed that state-sponsored hackers were behind this.
Notepad++ Hijacked by State-Sponsored Hackers | Notepad++
https://notepad-plus-plus.org/news/hijacked-incident-info-update/

Notepad++ Official Update Mechanism Hijacked to Deliver Malware to Select Users
https://thehackernews.com/2026/02/notepad-official-update-mechanism.html
In 2025, there was an issue where traffic from the Notepad++ updater, WinGUp, was redirected to malicious domains, distributing malware. To address this issue, Notepad++ released version 8.8.9 in December 2025.
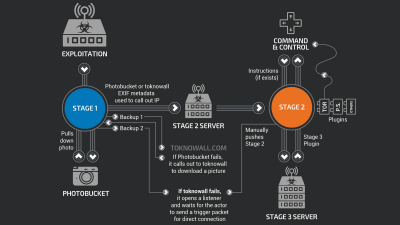
The company is currently working with external security experts to investigate the details of the hack. According to security experts, the attack involved an infrastructure-level breach, where a malicious attacker intercepted and redirected update traffic from the Notepad++ domain, 'notepad-plus-plus.org.'
While the exact mechanism of the hack is still under investigation, it has been revealed that the breach occurred at the hosting provider level, rather than exploiting a vulnerability in Notepad++'s code itself. Notepad++ explained the hacking attack as follows: 'Traffic from specific targeted users was selectively redirected to a malicious update manifest controlled by the attacker.'
According to Notepad++, the hacking attacks began in June 2025, and multiple independent security researchers have assessed that the perpetrators are likely a group backed by the Chinese government.
Independent security researcher Kevin Beaumont has pointed out that the Notepad++ hack was carried out by a China-backed threat actor called Violet Typhoon (APT31).
Security experts have already proposed an incident response plan, and Notepad++ is facilitating direct communication between the hosting provider and the incident response team. After the IR team worked with the provider to review the situation, the provider explained to them that the shared hosting server had been compromised until September 2, 2025.
According to the report, even after losing access to the servers, the attackers retained credentials for internal services and continued to redirect Notepad++ update traffic to the malicious servers until December 2, 2025. The attackers specifically targeted Notepad++ domains, attempting to exploit insufficient update verification functionality in older versions of Notepad++. The provider completed all repairs and security enhancements by December 2, 2025, successfully preventing further attacker activity.
To address this serious security issue, the Notepad++ website has moved to a new hosting provider with significantly improved security measures, and Notepad++ itself has also hardened WinGup in version 8.8.9, modifying its specifications to verify both the certificate and signature of downloaded installers.
In addition, the XML returned from the update server will be signed (XMLDSig), and certificate and signature verification will be enforced starting with version 8.9.2, which is scheduled to be released in about a month.
Some on the social message board Hacker News have pointed out that 'Notepad++ is known for sending political messages in its updates, such as to Taiwan and Ukraine ,' and that Notepad++'s support for Taiwan's sovereignty is the reason it has become a target for Chinese government-backed hackers.
Notepad++ v8.6.9 - Support Taiwan's Independence | Notepad++
https://notepad-plus-plus.org/news/v869-about-taiwan/