What is the Linux container environment that supports Claude's AI assistant 'Cowork mode'?

Anthropic's AI assistant, 'Cowork,' is a powerful tool that can assist with daily tasks and perform file operations based on user instructions. Cowork mode runs in a Linux container environment, and
linux-container-environment-report.md
https://gist.github.com/simonw/35732f187edbe4fbd0bf976d013f22c8
Survey method
Regarding the investigation method, Willison said, 'To see how the sandbox works, I instructed Claude Code itself to look at the '/Applications/Claude.app' directory.' The final output of the investigation was instructed to Cowork by prompting it to 'Write a detailed report about the Linux container environment you are running in.'
◆Hardware configuration
| CPU | ARM64 core (48 BogoMIPS ) x 4 |
|---|---|
| RAM | 3.8GiB (2.8GiB of which is the maximum available capacity) |
| Swap | (none) |
| Root disk | 10GB NVMe |
| Session Disc | 10GB NVMe |
Regarding the use of the ARM64 processor, it is stated that 'it has advanced features such as hardware cryptographic acceleration (AES, SHA1, SHA2, SHA3, SHA512), atomic operations , pointer authentication (PACA/PACG), and branch target identification (BTI) for security,' indicating that Anthropic highly values the efficiency of the ARM architecture as the hardware configuration for AI inference models. The 2.8 GiB available limit in cowork mode is thought to be a measure to ensure resource management and stability. As for storage, 10 GB of NVMe is allocated to both the root disk and session disk, which is thought to enable high-speed data access.
◆OS configuration
| Distribution | Ubuntu 22.04.5 LTS (Jammy Jellyfish) |
|---|---|
| kernel | Linux 6.8.0-90-generic (PREEMPT_DYNAMIC) |
| Architecture | aarch64 (ARM64) |
| Hostname | Claude |
At the time of writing, the latest Ubuntu LTS is 24.04, but the Cowork mode container environment uses 22.04. The kernel version is 6.8.0-90-generic, the same as 24.04 LTS. The kernel uses a preemption model called PREEMPT_DYNAMIC, which allows for flexible support for applications that require real-time performance.
◆Container configuration
| Sandbox Method | Bubblewrap (bwrap) |
|---|---|
| Network Isolation | --unshare-net creates an independent network namespace |
| PID isolation | --unshare-pid creates a separate process namespace |
| Die-with-parent | The container will exit when the parent process exits. |
| New Session | Preventing device hijacking attacks |
Bubblewrap (bwrap) is used in cowork mode container environments. bwrap is a lightweight sandbox tool that uses the Linux namespace feature to isolate processes, and is particularly excellent for security and resource management. In cowork mode, the network namespace and process namespace are independent, making it less susceptible to influence from other containers or the host system. In addition, the die-with-parent option automatically terminates the container when the parent process terminates, reducing the container's impact on the system and preventing unnecessary resource consumption.
◆Seccomp filtering
| Seccomp mode | 2: filter mode |
|---|---|
| Active Filter | 2 |
| NoNewPrivs | Enabled: Prevents privilege escalation |
| Capabilities | Drop all privileges (CapEff = 0) |
Secure computing mode (Seccomp) is a Linux kernel feature that enhances security by restricting the system calls that a process can use.Capabilities is a Linux privilege management feature that allows specific privileges to be granted or revoked to a process, but in Cowork mode, all privileges are dropped, preventing a process from affecting the entire system.
◆Network Proxy Architecture
| protocol | Proxy Port | UNIX domain sockets |
|---|---|---|
| HTTP/HTTPS | http://localhost:3128 | /tmp/claude-http-*.sock |
| SOCKS5 | socks5h://localhost:1080 | /tmp/claude-socks-*.sock |
| FTP/gRPC | socks5h://localhost:1080 | /tmp/claude-socks-*.sock |
In a container environment in Cowork mode, communication with the outside world goes through a local tunnel as a proxy. An HTTP proxy running on port 3128 is used for HTTP/HTTPS communication, and a SOCKS5 proxy running on port 1080 is used for FTP and gRPC . The socat command is used to create the local tunnel, which forwards network traffic to the host system via a UNIX domain socket . Properly configuring the network proxy architecture makes it possible to monitor and control communications, enhancing security and privacy protection.
◆Partition configuration
| device | Mount points | size | File System |
|---|---|---|---|
| nvme0n1p1 | / | 9.6GB | ext4 |
| nvme0n1p15 | /boot/efi | 98MB | vfat |
| nvme1n1 | /sessions | 10GB | ext4 |
The root filesystem is mounted in ext4 format on a 10GB NVMe device where all system resources are expected to reside. The /boot/efi directory has a 98MB vfat EFI system partition mounted for UEFI booting. The /sessions directory has another 10GB NVMe device mounted, which is used to store data related to user sessions.
◆ Execution process configuration
| PID | process | overview |
|---|---|---|
| 1 | bwrap | bwrap sandbox control |
| 2 | bash | Shell wrapper for managing proxy daemons |
| 3 | socat | HTTP Proxy Forwarder (port 3128) |
| 4 | socat | SOCKS Proxy Forwarder (Port 1080) |
| 5 | Claude | Claude Code agent process body |
The main Claude process runs under the model claud-opus-4-5-20251101 and can use certain authorized tools, such as Task, Bash, Glob, Grep, Read, Edit, and Write.
Additionally, two Model Context Protocol (MCP) servers have been configured.
| MCP Server | overview |
|---|---|
| Claude in Chrome | Browser automation features |
| b89c1e3a-f5c6-4dec-9d8a-0b3db0a78353 | Cloudflare Integration |
Summary
The information is summarized briefly as follows: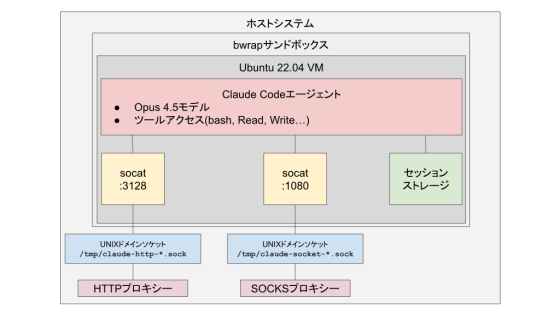
The Cowork mode container environment is a carefully designed sandbox for AI-assisted computing, aiming to balance functionality and security. It is also optimized for the Claude Code agent, allowing it to safely and efficiently execute tasks based on user instructions. By building this advanced container environment, Anthropic has succeeded in improving the performance of its AI assistant while maintaining its reliability and security.
Related Posts: