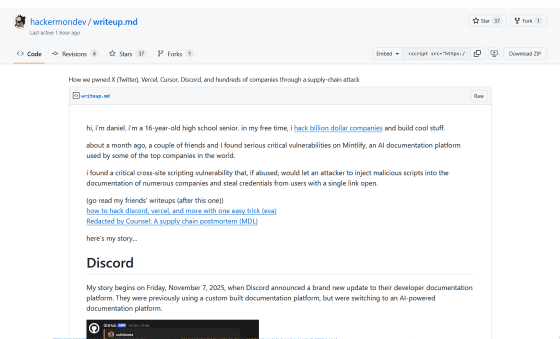
A 16-year-old high school student discovered a vulnerability in Mintlify, an AI document generation tool used by Discord.

How we pwned X (Twitter), Vercel, Cursor, Discord, and hundreds of companies through a supply-chain attack · GitHub
https://gist.github.com/hackermondev/5e2cdc32849405fff6b46957747a2d28
Daniel has been actively searching for vulnerabilities for some time, and Discord is one of his favorite places to do so because of his familiarity with the API and platform. Over the past few years, Daniel has reported nearly 100 vulnerabilities for Discord, putting him at the top of the bug bounty leaderboard.
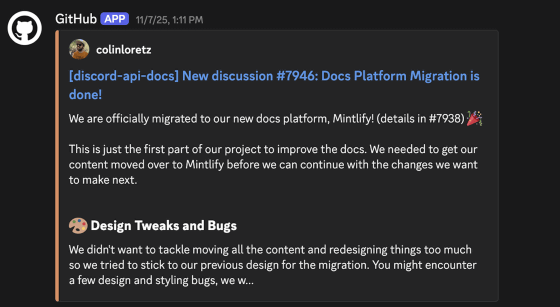
Discord announced that it would be migrating its developer documentation platform to Mintlify in November 2025. Intrigued by this announcement, Daniel began looking into how Mintlify was implemented.
Mintlify is an AI-powered documentation platform that converts documents written in Markdown format into a beautiful documentation platform with all the modern features you need. Mintlify's hosted documentation site is on the 'mintlify.app' domain, and custom domains are also supported. In Discord's case, they simply proxy a specific route to the Mintlify documentation site.
Daniel narrowed his focus to 'how to render another Mintlify document through the Discord domain,' searching for
Two days later, on November 9th, Daniel investigated the npm package for running Mintlify's documentation site locally and downloaded the file archive linked to the code. He discovered the application's API endpoint, which was different from the one he had previously found and returned static files from the documentation repository.
When testing the API endpoints, Daniel found that accessing HTML and JavaScript files was not possible, but SVG files were. Since SVG files can contain embedded JavaScript, he uploaded an SVG file with the embedded script to Mintlify's documentation and was able to open the endpoint via Discord.
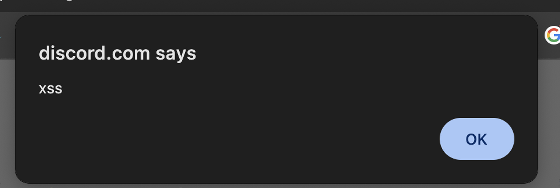
The method Daniel discovered could allow an attacker to simply insert a malicious link into a document, potentially stealing users' credentials. This type of exploit, known as a cross-site scripting (XSS) attack , is extremely rare on Discord.
Daniel shared the vulnerability with several friends, who also discovered other vulnerabilities in Mintlify. When Daniel and his friends reported the vulnerability to Discord, Discord took the vulnerability seriously and shut down the entire developer documentation for two hours to investigate the impact of the vulnerability. They then removed Mintlify and reverted to the previous documentation platform.
Mintlify, which learned of the vulnerabilities via Discord, also contacted Daniel directly. The Mintlify engineering team then worked with Daniel and other friends who discovered the vulnerabilities to fix them. The series of vulnerabilities was also reported on Mintlify's official blog.
Mintlify Security Event - November 2025
https://www.mintlify.com/blog/working-with-security-researchers-november-2025
'Fortunately, we discovered and disclosed this vulnerability responsibly, but it's a real-world example of how a single compromised supply chain can cause so many problems,' Daniel said.
Related Posts:
in Web Service, Security, Posted by log1h_ik