Malware appears that uses GitHub notification emails to trick users into thinking they are from the security team

Ian Spence, an open source software (OSS) developer, reported in a blog post the existence of malware that exploits GitHub notification emails.
GitHub Notification Emails Hijacked to Send Malware - Ian's Blog
Spence is involved in OSS development on GitHub and frequently receives notification emails from GitHub. One time, Spence received the following email. The email said, 'A security vulnerability has been detected in your repository. Please contact us for more information,' and the sender was listed as 'Github Security Team.'
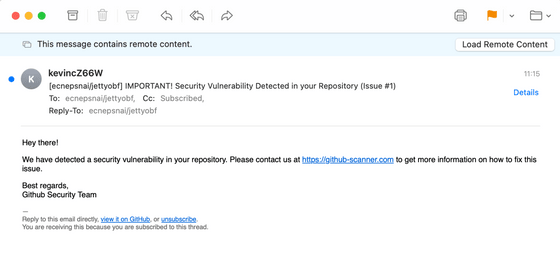
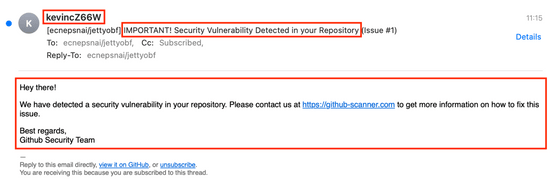
In fact, the email is not a message from the security team, but simply a notification email when a new GitHub issue is created. The content of the issue is a place where users can freely write, so the part in the red frame in the email is written maliciously by an attacker.
When Spence clicked on the link, he was greeted with a screen requesting a CAPTCHA, as shown below.
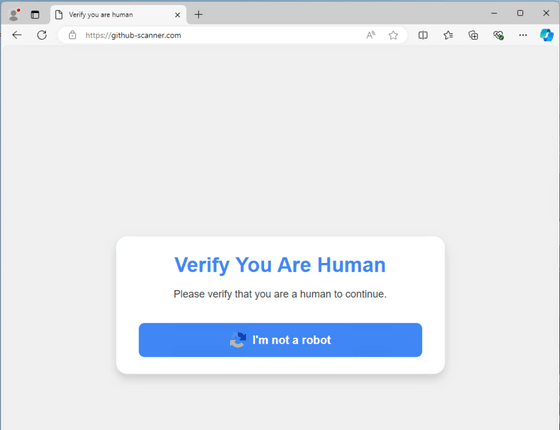
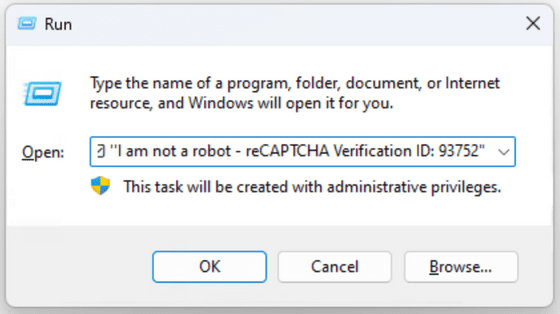
While most CAPTCHAs require users to simply click on a specific image, this site requires users to open Windows' Run and paste a command into the program. When Spence pasted the command into Notepad, it said to launch PowerShell and download and execute a command from a specific site.
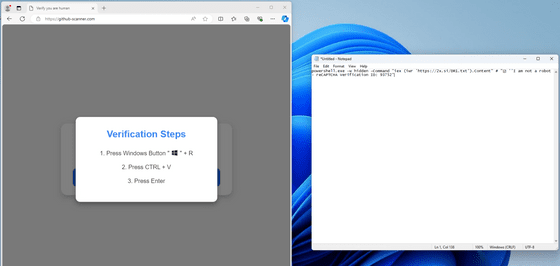
A comment was inserted after the command to hide the actual command when it was pasted.
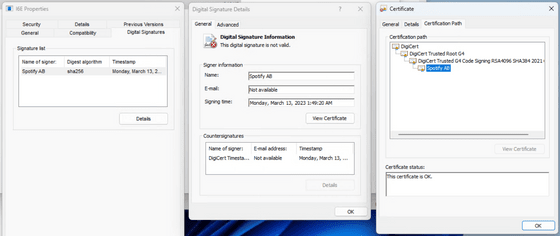
Of course, executing the command will install the malware. The signature of the malware executable file is invalid and it is disguised as Spotify, but because it is a file downloaded via PowerShell, it can be executed without any warning on Windows.
This malware is said to steal cryptocurrency-related data from browsers, email clients, files, etc. A detailed analysis of its operation has been conducted by security company CYFIRMA, so if you are interested, please check it out.
Related Posts:
in Free Member, Security, Posted by log1d_ts