Nearly 1.3 million Android-based TV boxes in about 200 countries have been found to be infected with malware

Security company
Vo1d hits over a million Android TV boxes
https://news.drweb.co.jp/show/?i=14900
New Vo1d malware infects 1.3 million Android streaming boxes
https://www.bleepingcomputer.com/news/security/new-vo1d-malware-infects-13-million-android-streaming-boxes/
1.3 million Android-based TV boxes backdoored; researchers still don't know how | Ars Technica
https://arstechnica.com/security/2024/09/researchers-still-dont-know-how-1-3-million-android-streaming-boxes-were-backdoored/
In August 2024, Dr.Web received multiple reports from users that their antivirus software had detected changes in the system file area. After investigating, it was found that several TV boxes were infected with the same malware.
TV boxes are devices that allow users to access streaming services by connecting them to their home TVs, and have become widespread with the rise of distribution services. All of the TV boxes found to be infected with malware this time were Android-based, but the OS they use is not the Android TV officially deployed by Google, but is based on the open source Android Open Source Project (AOSP) . OSs based on AOSP are used in a variety of smartphones and IoT devices, but unlike Android TV and other devices, they are not tested by Google for quality or safety.
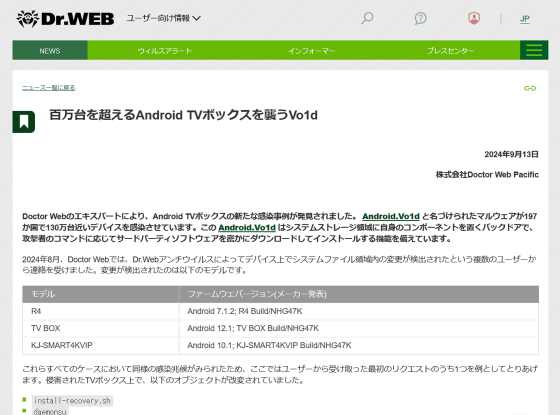
Android.Vo1d modifies objects on the TV box, such as “install-recovery.sh” and “daemonsu”, and creates four new files in the file system: “/system/xbin/vo1d”, “/system/xbin/wd”, “/system/bin/debuggerd” and “/system/bin/debuggerd_real”.
The main functionality is hidden in '/system/xbin/vo1d' and '/system/xbin/wd', and is said to download and execute files according to commands sent from the attacker's server, and monitor specified directories and install APK files.

The TV boxes infected with Android.Vo1d were running older Android-based firmware, such as 'Android 7.1.2; R4 Build/NHG47K', 'Android 12.1; TV BOX Build/NHG47K', and 'Android 10.1; KJ-SMART4KVIP Build/NHG47K'.
It is unclear how the malware infected the TV box, but Dr.Web believes that vulnerabilities in these firmware were targeted: 'Such versions contain unpatched vulnerabilities and are no longer supported for updates. For example, in this case, the user was using a model with Android 7.1,' Dr.Web said.
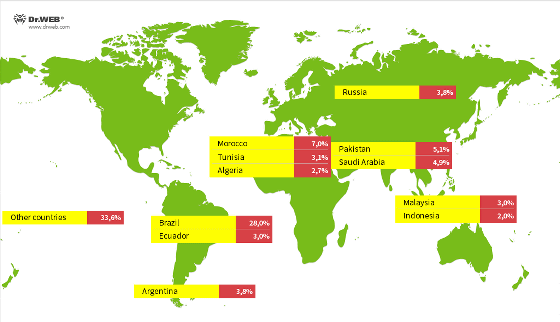
The map below shows the countries with the most Android.Vo1d-infected devices, including Brazil (28%), Morocco (7%), Pakistan (5.1%), Saudi Arabia (4.9%), Argentina (3.8%) and Russia (3.8%).
'At the moment, it is not clear how the TV box became infected with the backdoor. One possibility is an attack using intermediate malware that exploits vulnerabilities in the operating system to gain root privileges. Another possibility is the use of unofficial firmware with root privileges,' Dr.Web said.
Related Posts: