What is 'eBPF', a technology that prevents crashes even if an inappropriate update is made to the kernel area?
On July 19, 2024, an update distributed by cybersecurity company CrowdStrike caused 8.5 million Windows PCs worldwide to become unable to boot. Updates to the kernel, which is the core part of the OS, are always likely to cause serious problems, as in the case of CrowdStrike. eBPF is a technology that prevents crashes caused by such kernel updates.
No More Blue Fridays
You can learn more about the CrowdStrike incident by reading the article below.
CrowdStrike's Blue Screen of Death issue affected 8.5 million Windows devices, less than 1% of the total - GIGAZINE

The cause of the CrowdStrike incident is believed to be a mistake in a configuration file that CrowdStrike updates and distributes several times a day. An invalid address was specified in the configuration file, causing the kernel driver to try to read invalid memory, causing the system to crash.
What was wrong with CrowdStrike's code that caused many Windows to have blue screens?

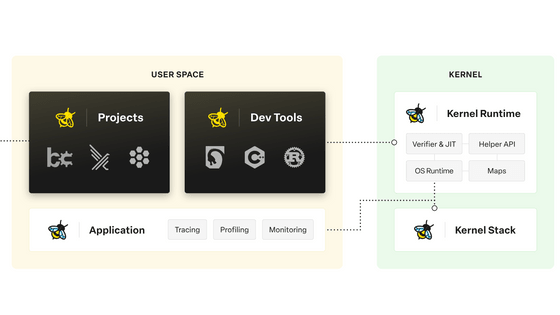
Web browsers provide an isolated execution environment for running JavaScript from untrusted sites. eBPF does the same thing in the kernel, statically verifying programs to ensure their safety and running them in an isolated kernel environment. If unsafe code is found during the checks, the program is rejected, without crashing the entire system.
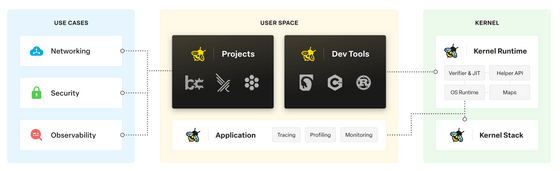
eBPF was first released in 2014 and was incorporated into the Linux kernel in 2017. As of 2024, major IT companies such as Google and Meta are using eBPF to detect malicious activities within their systems and improve security.
Development of eBPF for Windows is also underway, and as eBPF becomes more widespread, it will be possible to prevent security software from crashing the system.
Related Posts:
in Software, Posted by log1d_ts





