CrowdStrike has caused PCs to become unable to boot in the past on Linux distributions as well

On July 19, 2024, a problem occurred worldwide in which 'Windows displays a blue screen and is forced to restart repeatedly,' causing disruptions such as
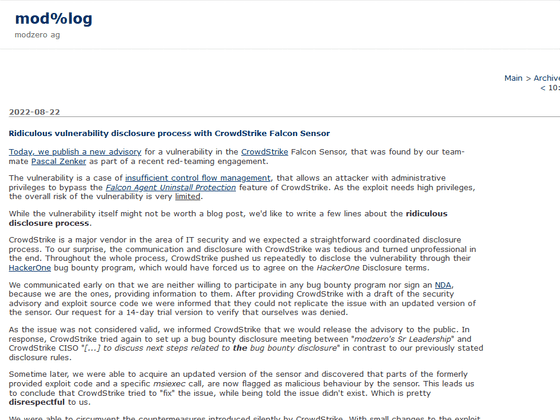
Ridiculous vulnerability disclosure process with CrowdStrike Falcon Sensor | mod%log
https://modzero.com/modlog/archives/2022/08/22/ridiculous_vulnerability_disclosure_process_with_crowdstrike_falcon_sensor/index.html

CrowdStrike broke Debian and Rocky Linux months ago, but no one noticed - Neowin
According to CrowdStrike , the cause of this issue was an error that occurred when strengthening the security of named pipes , one of the communication methods between programs, to address issues with ' Command and Control (C2) frameworks' commonly used in cyber attacks. This error is said to have caused repeated crashes and blue screens on PCs running CrowdStrike Falcon Sensor for Windows version 7.11 or later that were online during the update release period, and Microsoft estimates that the number of affected computers is 'approximately 8.5 million worldwide.'
In response to this issue, CrowdStrike CEO George Kurtz issued a statement apologizing to customers, stating, 'We are aware of the cause of this issue and are conducting a thorough root cause analysis.' 'The issue has been identified and isolated, and a fix has been distributed .'
There have been many reports of CrowdStrike-related problems in the past, including an incident in April 2024 when all of the Debian Linux servers at the research organization's CivicTech lab crashed simultaneously and refused to boot. It was later discovered that this was due to CrowdStrike updates being incompatible with the latest stable version of Debian, which supports certain Linux configurations. The CivicTech Lab discovered that removing CrowdStrike allowed the machines to boot, and took action to address the situation.
In addition, users who upgraded to
In addition, software developer Modzero has been pursuing a vulnerability that existed in CrowdStrike in August 2022. According to Modzero, this vulnerability allows an attacker with administrator privileges to bypass CrowdStrike's Falcon Agent Uninstall Protection function when control flow management of the CrowdStrike Falcon Sensor is insufficient .
Although the overall risk of this vulnerability was very limited because an attacker would need high privileges to exploit it, Modzero reported the vulnerability to CrowdStrike, who in turn informed Modzero that the issue could not be reproduced in the latest version under development and determined that the issue was not valid.
The latest version released after that flagged the vulnerability pointed out by Modzero as 'malicious behavior'. It has been confirmed that the same vulnerability appeared when Modzero made a small change to CrowdStrike's exploit. Modzero criticized, 'Vendors and researchers need to act responsibly and show mutual goodwill and transparency.'
Related Posts:
in Software, Posted by log1r_ut