Phishing scams taking advantage of the worst IT outage in history, the CrowdStrike problem, are on the rise
By
On July 19, 2024, Windows-based devices around the world crashed one after another, affecting a total of 8.5 million devices, causing damage to various institutions and companies, including airports and critical infrastructure such as medical facilities. Taking advantage of this issue, which has been called the 'worst IT outage in history,' it has been reported that there has been a sharp increase in phishing scams disguised as CrowdStrike and malware disguised as recovery tools.
Falcon Sensor Issue Likely Used to Target CrowdStrike Customers
https://www.crowdstrike.com/blog/falcon-sensor-issue-use-to-target-crowdstrike-customers/
Fake CrowdStrike fixes target companies with malware, data wipers
https://www.bleepingcomputer.com/news/security/fake-crowdstrike-fixes-target-companies-with-malware-data-wipers/
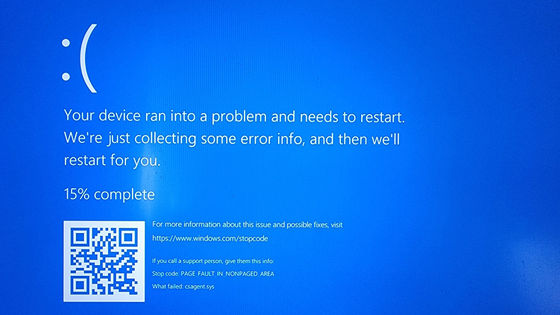
The CrowdStrike issue that occurred on July 19th involved a malfunction of the CrowdStrike Falcon sensor, a security solution installed on Windows devices, causing the OS to repeatedly display a blue screen and restart.
CrowdStrike CEO George Kurtz issued an apology for the incident, and CrowdStrike and Microsoft are working together to release recovery guidance and tools to resolve the situation.

As organizations around the world worked to restore services, several organizations reported that they had been hit with a flurry of cyberattacks exploiting the issue since the outage began.
In
Additionally, malware analysis platform AnyRun has reported indications that malicious actors are attempting to impersonate CrowdStrike in phishing scams.
For example, cybersecurity researcher g0njxa reported that the Remcos RAT Trojan, disguised as a “CrowdStrike Hotfix”, was being used to phish online banking users.
#Remcos RAT being delivered as a fake Crowdstrike Hotfix, targeting @bbva bank
— Who said what (@g0njxa) July 20, 2024
from: /portalintranetgrupobbva.com
Delivered via Dropbox
C2: 213.5.130.58:443
Detonation: https://t.co/6kt15AWD36 pic.twitter.com/49dXSEvqto
In addition, it has been reported that a data wiper has been distributed disguised as an update from CrowdStrike, and when installed, it overwrites all files on the device with empty files with a capacity of zero bytes.
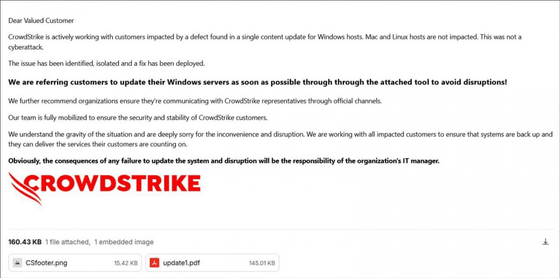
In connection with this data wiper, the pro-Iranian hacktivist group Handala claimed responsibility for the attack, saying it had sent emails to Israeli companies disguised as CrowdStrike delivering the data wiper.
Below is a phishing email sent by Handala to targeted companies, which was spotted by IT news site BleepingComputer with a PDF file attached that contained detailed instructions on how to apply the fake update and a link to where it was distributed.
In a blog post, CrowdStrike
CrowdStrike CEO Kurtz also urged customers to 'remain vigilant and ensure that you engage with official CrowdStrike representatives, as we expect adversaries and malicious actors will exploit this incident.'
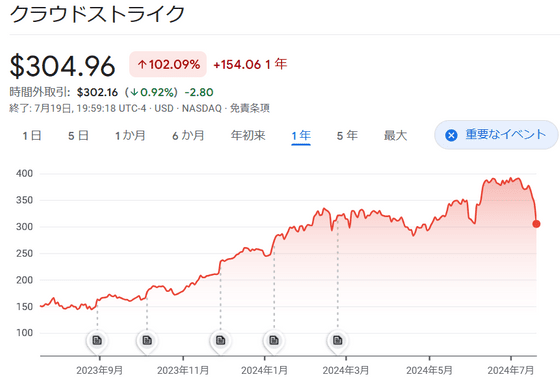
CrowdStrike's stock price fell 11.1% on July 19, the day the issue occurred. The company's stock price had risen nearly 118% in the 12 months prior to the issue.
Related Posts:
in Security, Posted by log1l_ks