Hackers impersonating security firm ESET sent phishing emails to Israeli organizations, possibly attacking pro-Palestinian organizations

By
It has been discovered that a partner company of Slovakian security company ESET was hacked and sent phishing emails to an Israeli organization with the aim of infecting PCs with a wiper, a type of malware that erases data. The identity of the hacker is unknown, but experts point out that the methods used are similar to those of pro-Palestinian organizations or Iranian hacking groups.
EIW — ESET Israel Wiper — used in active attacks targeting Israeli orgs | by Kevin Beaumont | Oct, 2024 | DoublePulsar
https://doublepulsar.com/eiw-eset-israel-wiper-used-in-active-attacks-targeting-israeli-orgs-b1210aed7021
Hackers reportedly impersonate cyber firm ESET to target organizations in Israel
https://therecord.media/hackers-impersonate-eset-wiper-malware
Hacker Hits ESET's Partner in Israel to Send Malware That Can Wipe PCs | PCMag
https://www.pcmag.com/news/hacker-hits-esets-partner-in-israel-to-send-malware-that-can-wipe-pcs
ESET partner breached to send data wipers to Israeli orgs
https://www.bleepingcomputer.com/news/security/eset-partner-breached-to-send-data-wipers-to-israeli-orgs/
The cyber attack came to light on October 9, 2024, when a user posted on ESET's official forum that he had received a suspicious email warning him that a government-backed attacker was attempting to break into his PC.
The email, purporting to be from 'ESET Advanced Threat Defense Team' with the address '[email protected]', contains a download link for a compressed file hosted on an ESET domain.
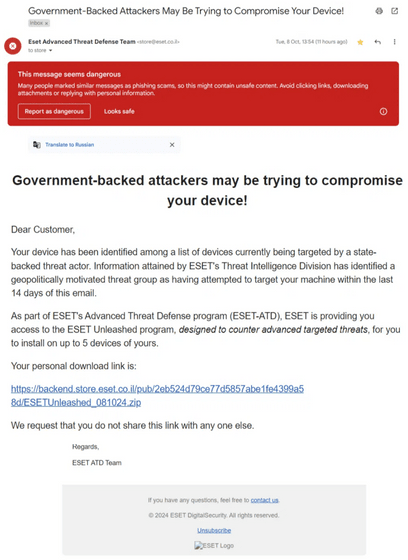
When cybersecurity researcher Kevin Beaumont verified the link, he found that the archive indeed came from a domain owned by ESET's Israeli subsidiary, meaning that the hackers were able to get past ESET's defenses.
'My belief is that someone was compromised because the ESET store and mail servers were being used. The breach occurred over a week ago but for some reason has not been made public,' Beaumont wrote in an Oct. 18 blog post.
The executable file 'Setup.exe' included in the compressed file contains malware that will erase all data on the PC if executed.
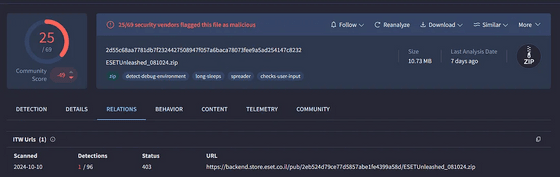
ESET, meanwhile, acknowledged the security incident but denied that its infrastructure had been compromised. In response to media inquiries, the company said that the attack was not carried out by ESET, but by Comsecure, ESET's distributor in Israel.
In a social media post, ESET said: 'We are aware of a security incident affecting one of our partners in Israel last week. Based on an initial investigation, the limited malicious email campaign was blocked within 10 minutes. ESET technology blocked the threat and our customers are safe. ESET was not compromised and is working closely with our partners to further investigate and continue to monitor the situation.'
We are aware of a security incident which affected our partner company in Israel last week. Based on our initial investigation, a limited malicious email campaign was blocked within ten minutes. ESET technology is blocking the threat and our customers are secure. ESET was not…
— ESET Research (@ESETresearch) October 18, 2024
Beaumont said the phishing emails targeted cybersecurity personnel at organizations across Israel.
At the time of writing, it is unclear who carried out the cyber attack, but the date of the attack was the day after October 7, 2024, which marks one year since Palestinian extremist groups, including Hamas, invaded Israel, and the method used included the use of a data wiper. Based on this, Beaumont suggested a connection with the pro-Palestinian group 'Handala' or the Iran-related hacker group 'CyberToufan.'
In July 2024, Handala launched a phishing attack impersonating security company CrowdStrike and claimed responsibility for the attack.
Phishing scams taking advantage of the worst IT outage in history, the CrowdStrike problem, are on the rise - GIGAZINE
By Alpha
Related Posts: