Ransomware watching Pokemon GO's Windows version application to encrypt the file and take it to the hostage is confirmed

A false app called "Windows version Pokémon GO (Pokemon GO)" was developed, a misunderstanding that it is a real Pokemon GO application, a person who installed it infects with Ransomware, so that the victim can not access the data of the terminal It is reported that threatening the ransom. Pokemon GO Ransomware is behaving differently than the general rantamware that has been reported so far.
PokemonGo Ransomware installs Backdoor Account and Spreads to other Drives
http://www.bleepingcomputer.com/news/security/pokemongo-ransomware-installs-backdoor-accounts-and-spreads-to-other-drives/
This Ransomware is a security researcher'sMichael GillespieWhat was discovered by Mr. The icon of the application is like this.

Ransomware infected by the victim's device scans the terminal first to see if it contains files with the following extensions:
.txt, .rtf, .doc, .pdf, .mht, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .jpg, .png, .csv, .sql, .mdb, .sln , .php, .asp, .aspx, .html, .xml, .psd, .htm, .gif, .png
Then, these filesAES, And added an extension ".locked" to the encrypted file. Prevent users from accessing files on the device. And when the work is completed, "If you want to access data on this terminal, please indicate" me.blackhat20152015@mt2015 "to show how to pay ransom"
Many of the past rantamware that was reported in the past were encrypting data, deleting it, and then displaying intimidation content. However, the point that Pantsmon GO's Ransomware does not delete the data, it differs from usual in that it displays intimidation contents in a state just encrypted. Also, when infected, creating a backdoor in a Windows terminal is different from other, so that the creator of the Ransomware can access the victim's terminal again at a later date.
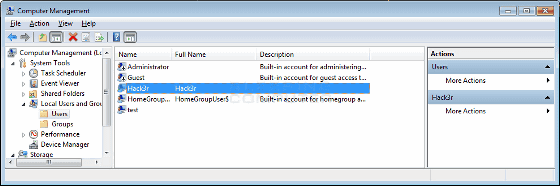
When it is infected with Panthem GO's Ransomware as follows, a user account "Hack 3r" is added to the terminal's Administrators group without permission. At this time, the Hack3r account will be hidden from being visible from the Windows login screen.
Also, the unique point of Pangemon GO's Ransomware is the creation of network shares on the victim's computer. However, this network sharing is not utilized at the time of article creation, its purpose is unknown.

In addition, this Pokemon GO Ransomware wants to copy its own executable file to the removable drive. A file called "Autorun.inf" is created in the removable drive infected by Ransomware, and another computer is also infected with Ransomware at the moment of connecting the drive to another computer, I will try to spread it. And, when copied from the external drive to the C drive of the computer, PokemonGo Ran Sumware is automatically called when the user tries to log in to the Windows account.
The target of Pokemon GO discovered this time is that people in the Arab region see from the language used in intimidation sentences. The following is a threat document, translating "Your file has been encrypted. Please contact [email protected] to get encrypted. Thank you in advance for your generosity I will represent ".
(: لقد تم تشفير ملفات كم, لفك الشفرة فلكسي موبيليس للعنوان التالي me.blackhat [email protected] وشكرا على كرمكم مسبقا
Finally, when the victim user logs in to Windows, the following screen saver will be displayed.

"123 vivalalgerie" of AES password means "Algeria million years", Arab and French languages were used in the program, "Sans Titre" written in the screensaver program is "French" Untitled (Untitled) ", it is expected that developers of Ransomware are Algerians. From the above characteristics, Pokemon GO Ransomware is still considered to be in the stage of "under development", and it is unknown how much infection spreading power will be acquired. From now on, it seems necessary to pay close attention when downloading & installing Pokemon GO related applications.
Related Posts: