Avast distributes free decryption tools for DoNex ransomware and its variants

Avast, a security company that previously released
Decrypted: DoNex Ransomware and its Predecessors - Avast Threat Labs
https://decoded.avast.io/threatresearch/decrypted-donex-ransomware-and-its-predecessors/
Avast releases free decryptor for DoNex ransomware and past variants
https://www.bleepingcomputer.com/news/security/avast-releases-free-decryptor-for-donex-ransomware-and-past-variants/
Avast releases DoNex ransomware decryptor • The Register
https://www.theregister.com/2024/07/08/avast_secretly_gave_donex_ransomware/
'DoNext', for which Avast has released a decryption tool, is the predecessor of the ransomware 'Muse', which began to be used in April 2022. Muse then disguised itself as another ransomware called ' LockBit 3.0 ' in November 2022, renamed itself 'DarkRace' in 2023, and began calling itself DoNext in 2024.
DoNex is a targeted attack method, and has caused damage mainly in the United States, Italy, and Belgium. Although most cybercriminals tend to avoid targeting Russia, DoNex, which is unusual for ransomware, has also been confirmed to have caused damage in Russia and China.
If you are infected with DoNex, you will see a ransom note like this:
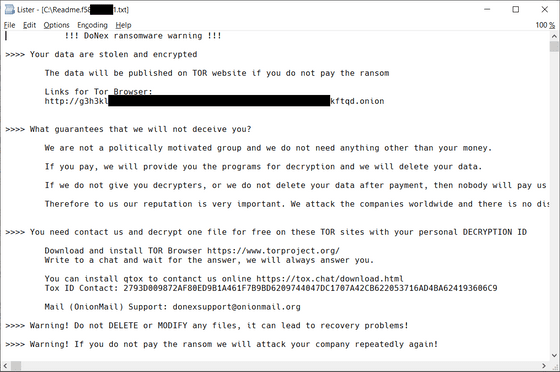
Avast, which has been working on this ransomware, has been secretly providing decryption tools to victims through law enforcement agencies since March 2024. It is common for security companies to covertly distribute decryption tools, with the aim of preventing cybercriminals from learning about and improving their ransomware flaws.
However, the DoNext flaws were widely
To install the decryption tool, first download the executable file ' avast_decryptor_donex.exe ' linked from the Avast public page and save it in a location of your choice.
Once saved, open the executable file, Avast recommends running it as administrator.
Once the tool has launched, click 'Next'.
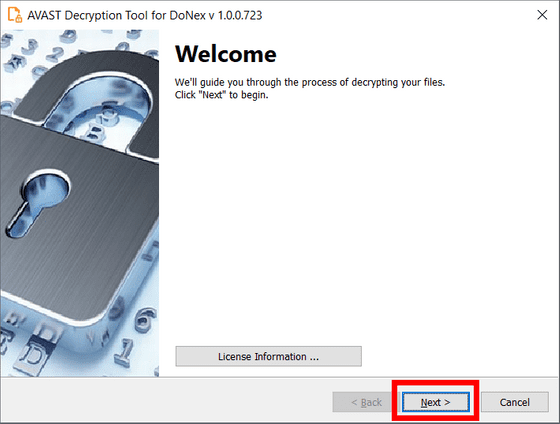
Next, specify the folder or directory to decrypt, but by default all local drives are specified. Once specified, click 'Next'.
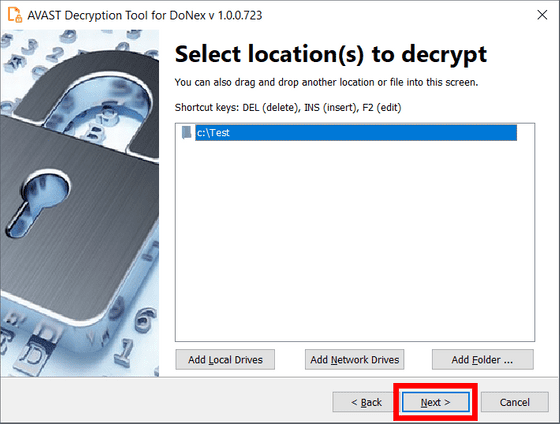
Next, specify the encrypted file and the original format file as samples and click 'Next'. It is recommended to specify the largest file possible.
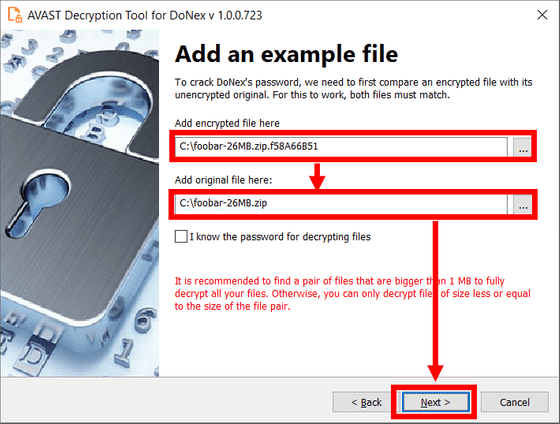
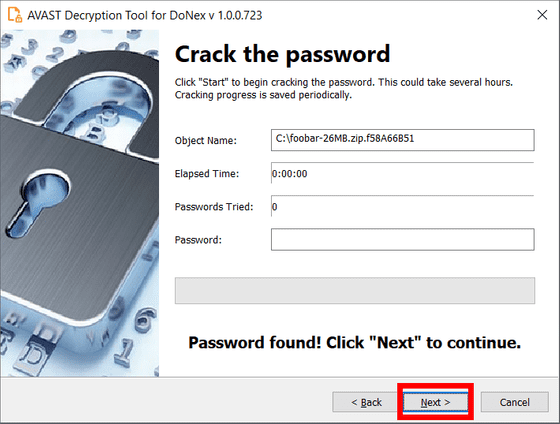
Next, the password cracking process is carried out, which requires a large amount of system memory but typically takes less than a second if memory is available.
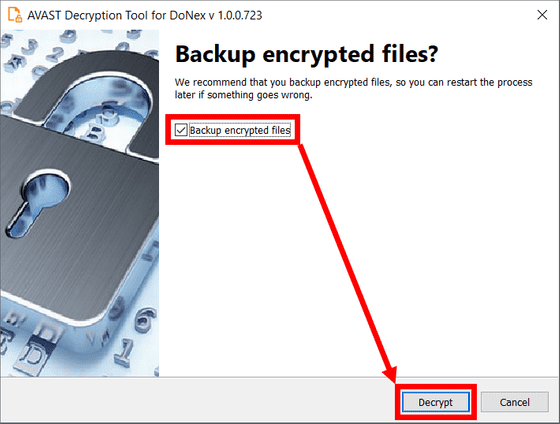
Finally, check whether you want to back up the encrypted files and click 'Decrypt' to decrypt them. The backup is for redoing the decryption process if there is a problem, and the backup option is checked by default.
Related Posts:







