Report that North Korean hackers are washing stolen virtual currency using cloud mining service

APT43-Report.pdf
(PDF file) https://mandiant.widen.net/s/zvmfw5fnjs/apt43-report
North Korean Hackers Use Cloud Mining Services to Launder Dirty Crypto - Decrypt
https://decrypt.co/124772/north-korea-korean-hackers-apt43-kimusky-cloud-mining-crypto-laundering
Newly exposed APT43 hacking group targeting US org since 2018
https://www.bleepingcomputer.com/news/security/newly-exposed-apt43-hacking-group-targeting-us-orgs-since-2018/
North Korean cyberhackers step up phishing attacks, target experts - The Washington Post
https://www.washingtonpost.com/world/2023/03/28/north-korea-hackers-phishing-attack/
North Korea is known for operating various hacker groups, and APT43 is one of the hacker groups that operates in line with North Korea's national ideology , Juche Idea. For more than five years, APT43 has been hacking government agencies, think tanks, and university professors with insight into North Korea-related international negotiations and sanctions, as well as key organizations in South Korea, Japan, the United States, and Europe. About.
Mandiant, which has been tracking APT43 since 2018, said in a report, ``Specifically, APT43 belongs to North Korea's main foreign intelligence agency , the Korean People's Army Reconnaissance General Bureau , and Mandiant has moderate We are evaluating it with confidence.'

APT43 uses virtual profiles and accounts impersonating others to send
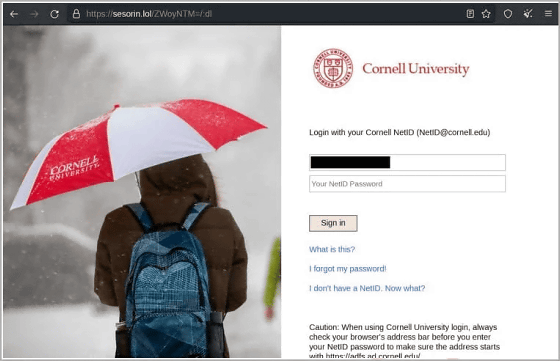
Below is a ``login page disguised as a Cornell University website'' that was actually created by APT43. Mandiant explains that hackers are using emails that impersonate legitimate people to lure targets to the page and steal the credentials they enter. Successfully stealing credentials from a target makes it easier to not only gather information from it, but also launch attacks against other related targets.
Phishing attacks have become more sophisticated in recent years, and more and more emails do not contain suspicious links or attachments, Klingner said. Instead, hackers have focused on building relationships with experts, in some cases 'commissioning' reports to masquerade as legitimate think-tank figures to gain North Korea-related insights. is.
In its report, Mandiant said, 'APT43 is primarily based on information held within the U.S. military, government, and defense industrial base, as well as research and policy devised by U.S. academic institutions and think tanks focused on nuclear defense policy and non-proliferation. I am interested in, ”he reported that he is also interested in similar non-profit organizations, universities, and manufacturers of sanctioned goods in South Korea. It has also been suggested that APT43 has also targeted healthcare and pharmaceutical companies during the pandemic and is sensitive to demands from North Korean regime officials.

In addition, APT43 is involved in cryptocurrency theft and money laundering targeting the general public to fund its activities. According to Mandiant, APT43 had developed an Android app targeting Chinese people looking to get loans in cryptocurrencies, stealing cryptocurrencies from users.
As to why APT43 is targeting individual users rather than cryptocurrency platforms and exchanges, Michael Barnhart, principal analyst at Mandiant, said, 'It spreads the attack across hundreds, if not thousands, of victims. This makes their activity less noticeable and harder to track than attacking one large target.' ``The pace of APT43's theft, combined with its success rate, is alarming.''
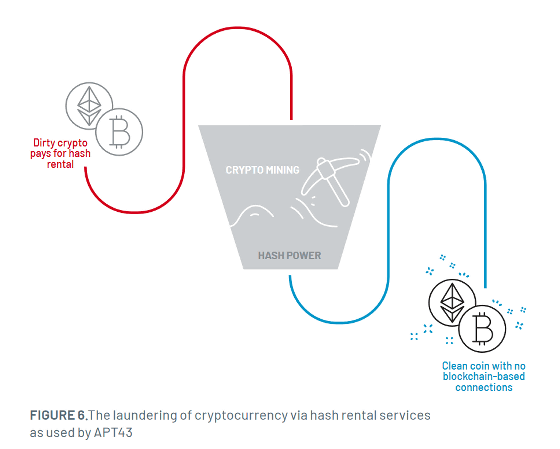
In addition, APT43 uses hash rentals that purchase part of the hash rate from mining companies and cloud mining services that borrow computer resources necessary for mining in order to launder the stolen virtual currency so that the origin is unknown. It is said that Mandiant reports that APT43 pays for stolen cryptocurrencies to use these services and converts them into clean cryptocurrencies.
Related Posts:
in Software, Web Service, Security, Posted by log1h_ik