A method is devised to steal Tesla's electric car with the wireless operation device ``Flipper Zero''

Stealing cars from electric car manufacturer Tesla by building a fake Wi-Fi network using
Can a Tesla Stop Phishing and Social Engineering Attacks?
https://www.mysk.blog/2024/03/10/tesla-phone-key/
Researchers use fake charging station WiFi to hack into and steal your Tesla - Autoblog
https://www.autoblog.com/2024/03/10/researchers-use-fake-charging-station-wifi-to-hack-into-and-steal-your-tesla/
Want to Steal a Tesla? Try Using a Flipper Zero
https://gizmodo.com/want-to-steal-a-tesla-try-using-a-flipper-zero-1851316236
Tommy Mysk and Talal Haji Bakri, security researchers at Mysk, used the wireless control device Flipper Zero to create Tesla Guest, a Wi-Fi network used by Tesla as a guest Wi-Fi network in its service centers. Constructed in a pseudo manner.

At first glance, it appears on the user's smartphone as if it were Tesla's official Wi-Fi.
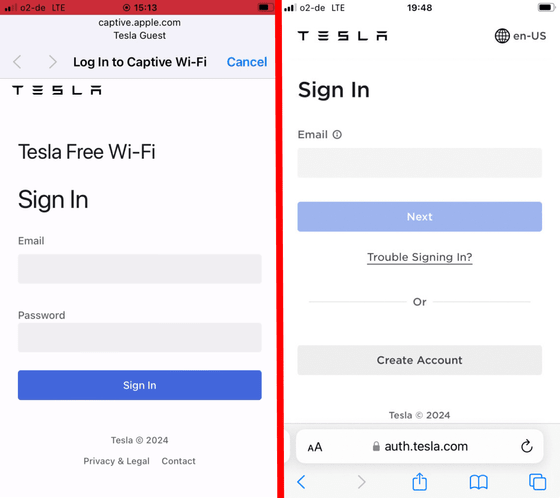
Additionally, we created a website that resembles a Tesla login page. Below is an image comparing the fake login screen created by Mr. Maisk et al. (left) and the real Tesla login screen (right).
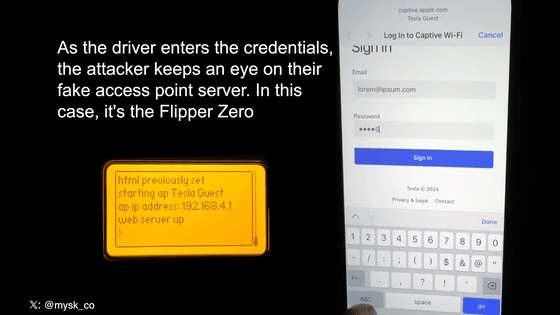
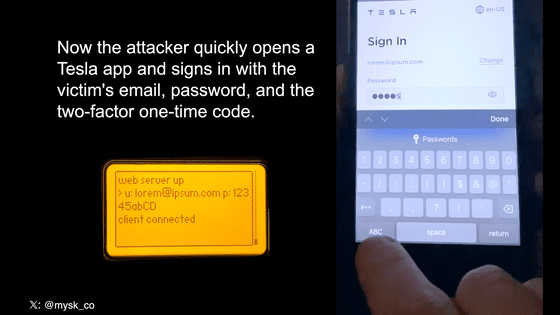
When you access the fake 'Tesla Guest' created by Mr. Maiske and others, the login screen for the above fake Tesla account will appear. Users are required to enter their email address and password to log into their Tesla account, as well as a one-time passcode for two-factor authentication, making the attacker feel as if they are signing in to Tesla's official website or app. This means that confidential information will be leaked to you.
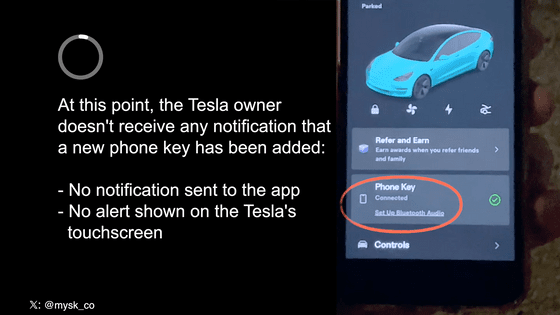
Based on this information, the attacker accessed the victim's real Tesla account. At that time, the victim will not receive a notification that a new sign-in to their Tesla account has occurred. It is also impossible to see how many active sessions a user has on Tesla's website.
Mr. Maisk et al. report, ``Simply broadcasting this Wi-Fi network near

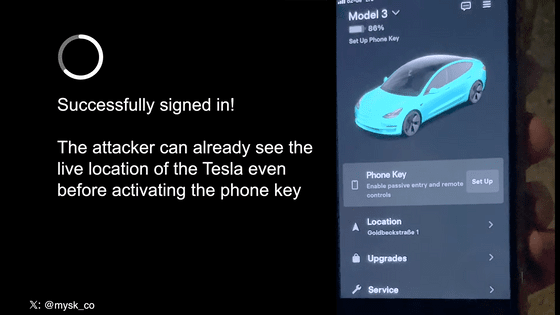
The attacker's compromised Tesla account displays multiple information about the vehicle, including its exact location and condition.
An attacker can also set their smartphone as a key to a vehicle by simply turning on Bluetooth and location services on the smartphone, pressing the 'Setup' button in the Tesla app, and walking by the vehicle.
Maiske et al., ``It would be too bold to steal a vehicle near a Supercharger, where the owner is likely to be nearby, even if they have information.The attacker can see information about the vehicle, so it is too bold to steal a vehicle near a Supercharger where the owner is likely to be nearby. Ideally, we would identify when the driver has left the vehicle and the vehicle is unattended.'
An attacker who has registered the key will be able to remotely operate the lights and unlock the vehicle doors.
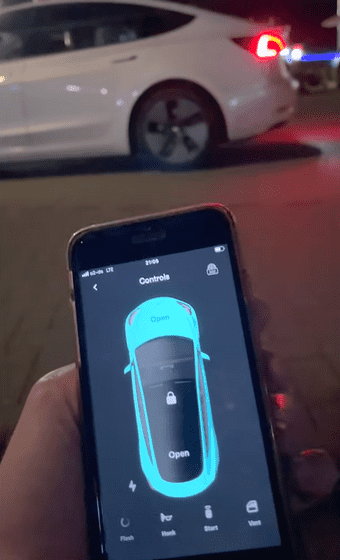
The attacker then gets into the vehicle, starts the engine, and steals the vehicle.
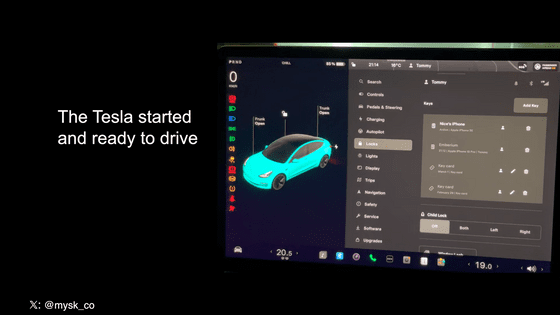
Tesla's owner's manual states, ``To set up a new smartphone key, you need a physical key card,'' but this experiment confirmed that this statement is incorrect. Mr. Maiske told Gizmodo, a foreign media outlet, ``Just by leaking an email address and password to an attacker, a driver could potentially have their vehicle stolen. This is insane. Attacks are based on phishing and social engineering. has been on the rise in recent years due to the rise of AI technology. Responsible companies like Tesla need to create threat models and consider the risk of information leakage.'
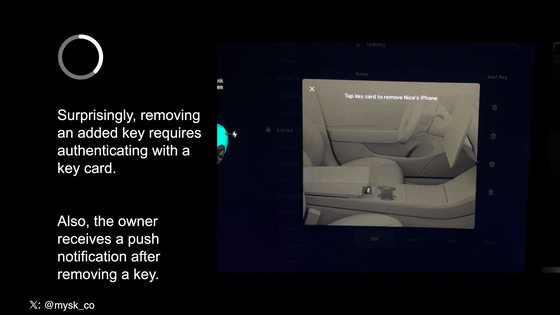
Mr. Maisk and his colleagues reported this result to Tesla, but Tesla said, ``This is just the result of an experiment and does not constitute a vulnerability that should be fixed immediately.''
'It's clear that Tesla cars are extremely vulnerable to phishing and social engineering attacks like this one,' Maiske said. ``Countermeasures should be introduced, such as ``notifying car owners when a new key is registered.''
Related Posts:







