How is the decentralized SNS Bluesky influenced by P2P technology?

`
Why isn't Bluesky a peer-to-peer network? | Paul's Dev Notes
https://www.pfrazee.com/blog/why-not-p2p
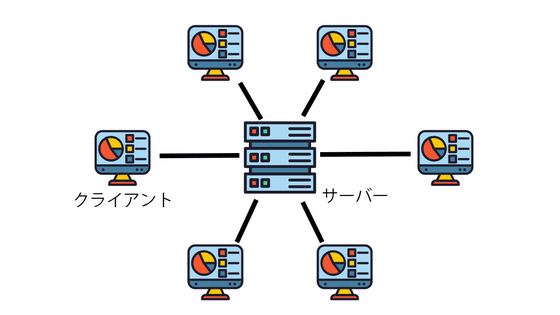
Among the computers connected to the network, the ``client-server'' model divides the roles into a ``server'' and ``client,'' and the client communicates by accessing the server. For example, in order to post a post on X (formerly Twitter) or retrieve someone else's post and display it on the timeline, you need to access the X server from a client such as a smartphone or PC.
Users' personal information and communication data are stored on the server and managed by the operator. It is called a centralized SNS because the authority to manage data and the platform is concentrated in the operator. While these centralized SNSs allow for efficient operation by allowing quick decision-making, they also have disadvantages such as the transparency of service operations and security risks.
This is where decentralized social networks such as Bluesky,
Masotodon, Misskey, and Threads use a federated network protocol called ActivityPub . Unlike a centralized system, ActivityPub's network has multiple servers (instances) operated by different operators. Users interact with any one of the instances, and different instances also interact with each other. In other words, each instance forms a small network, and these small networks form a larger network.
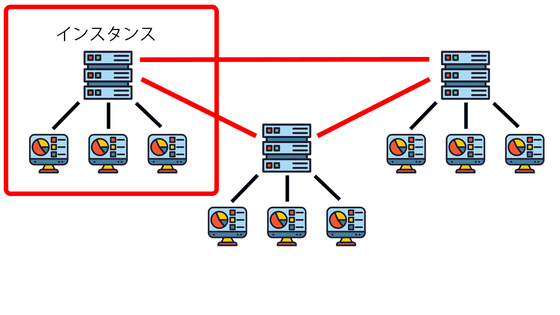
The federated type has the same structure as the centralized type in which users connect to one instance, but since users can freely move between instances, even if they are banned from one instance, they can still access SNS from another instance. Participation possible. However, if you move your instance, all user information such as profile and post data will be lost.
On the other hand,
In Bluesky's AT protocol, each user accesses a server called PDS (Personal Data Server). PDSs hold data such as user posts, 'likes' and 'shares', and PDSs communicate with each other. PDS information is aggregated on a server called Big Graph Service (BGS) and used as App View, a mechanism to display each post on the timeline on the application. However, at the time of writing the article, the AT protocol does not have a federation function.
The structure of holding data on one server is the same as ActivityPub, but with the AT protocol, user information is registered on a server called 'DID-PLC'. This DID-PLC is like a telephone directory that registers 'DID', which is a unique ID for users. Since this DID server exists separately from the PDS, user information can be carried over even if the PDS is moved.
According to Frenzy, Bluesky uses this network structure to combine the benefits of P2P with a federated network.
P2P itself is a technology that has existed for a long time; for example, the data transfer protocol BitTorrent is also a P2P communication protocol. BitTorrent accesses a server called a 'tracker' based on the torrent file, obtains information about the network to which clients connect, and joins. In this network, data is exchanged in pieces, with clients downloading and uploading data simultaneously. There are no servers in the network that aggregate and maintain data.
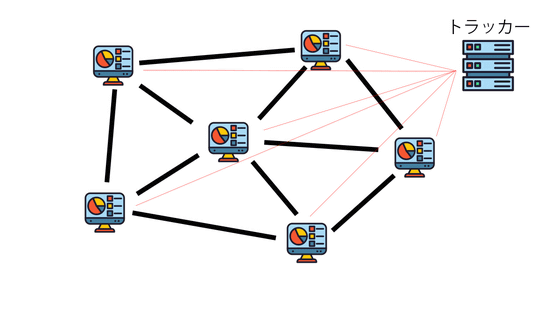
BitTorrent verifies data integrity by fragmenting files and recording and checking the hash values of the fragments in the torrent file. Furthermore, by introducing a hash tree, we are building a database while compressing the metadata part of torrent files.
In contrast, Bluesky stores user posts and operation history such as 'like' and 'share' in a data collection called 'repository' on PDS. According to Mr. Frenzy, this repository has a cryptographic structure called a ``Merkle search tree'' that uses a P2P hash tree, which allows for efficient verification of authenticity.
However, Mr. Frenzy argues that ``Bluesky cannot be called a P2P technology itself, and it is far from being called a federated type.'' Mr. Frenzy pointed out that the 'AT' in the AT protocol stands for 'Authenticated Transfer,' and the essence is the cryptographic structure of the authenticated database, and it may be more accurate to call it the 'cryptographic data web.' I argued that I could not.
Related Posts:
in Software, Web Service, Posted by log1i_yk