Researchers demonstrate that there is a risk of SSH private keys being stolen when a calculation error occurs

SSH is a protocol that uses encryption and authentication technology to securely communicate with remote computers, but it has been demonstrated that if a calculation error occurs during the RSA signature performed at the start of communication, the SSH private key can be analyzed. it was done.
(PDF)Passive SSH Key Compromise via Lattices
In a first, cryptographic keys protecting SSH connections stolen in new attack | Ars Technica
https://arstechnica.com/security/2023/11/hackers-can-steal-ssh-cryptographic-keys-in-new-cutting-edge-attack/
With SSH, the user creates a 'signature' when connecting, and the server verifies the signature to confirm whether the user is the correct user. RSA is used as the signature creation algorithm, and if a calculation error occurs when creating the signature, the private key will be stolen.
The implementation of RSA signatures has been generalized by dividing a calculation-intensive operation into two smaller operations, but one of the two operations may have an incorrect result even by 1 bit due to a bug such as a hardware failure or overflow. If the private key is returned, a signature that can be analyzed using the private key may be generated.
The paper actually analyzed SSH communication data collected over the past seven years through public Internet scans. Of the approximately 3.2 billion signatures included in the data, approximately 1.2 billion were signatures using the RSA encryption method, and 0.048%, or 590,000, were signatures with errors.

When this attack was applied to these 590,000 items, it was possible to extract 4,962 private keys. It is stated that the number of unique private keys remained at 189 because many hosts shared SSH keys or created signatures multiple times.
The basic attack mechanism can be applied to communications that use RSA, and
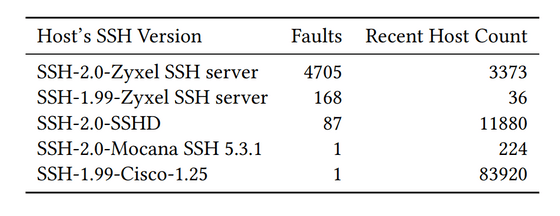
It is said that this vulnerability can be countered by simply checking whether the signature has been generated correctly before sending it.For example, OpenSSH, an SSH software integrated into Linux, was developed in 1999. This issue has been addressed since its release. On the other hand, when we investigated which SSH software created the problematic signature based on the signature version information, as shown in the figure below, 'Zyxel' was the most common, and problems were also confirmed with 'SSHD', 'Mocana', and 'Cisco'. it was done.
Keegan Ryan, the lead author of this paper, said, ``Even a single bit of memory flipping can expose the private key, so it is important that measures to detect and suppress errors work with 100% accuracy.'' is important.”
Related Posts:
in Security, Posted by log1d_ts