'Fingerprints' that identify website users may be worse than thought
Our website uses cookies to help us identify you when you visit us at a later date and to serve you ads based on your browsing history. However, since Firefox and others are equipped with a protection function that blocks cookies and prevents them from being tracked, 'fingerprints' are becoming used as a substitute for cookies. Developer bitestring points out that this 'fingerprint' does not work with the method that prevented cookies, and it is a bad thing.
Web fingerprinting is worse than I thought - Bitestring's Blog
Bitestring uses a feature demo from FingerprintJS, a company that offers 'fingerprinting' as a service, to demonstrate just how bad fingerprinting can be.
The procedure of the demonstration experiment is as follows.
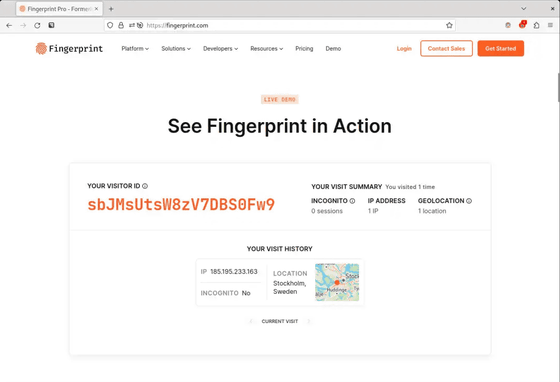
1: Access 'FingerprintJS (https://fingerprint.com)' for fingerprint generation
2: View the generated fingerprint
3: Clear your web browser cache and all other site data
4: Revisit 'FingerprintJS'
5: View fingerprints and browsing history. Even without cookies or other site data, the same fingerprint is generated, giving you a history of previous browsing.
6: Clear your web browser cache and all other site data again
7: Access 'FingerprintJS' in private browsing mode
8: Display the fingerprint and check how it differs from the past two browsing times.
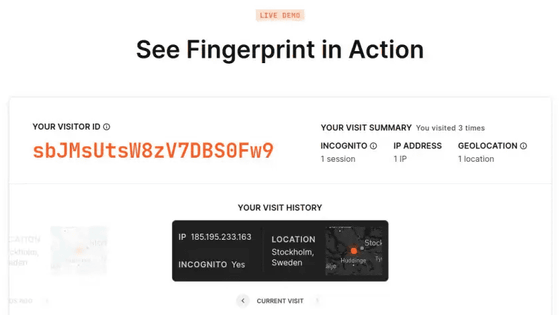
Below is the result of Mr. bitestring actually trying with Firefox. The fingerprint generated by the first access is 'sbJMsUtsW8zV7DBS0Fw9'.
Despite deleting all accessed information, the fingerprint is the same for the second access.
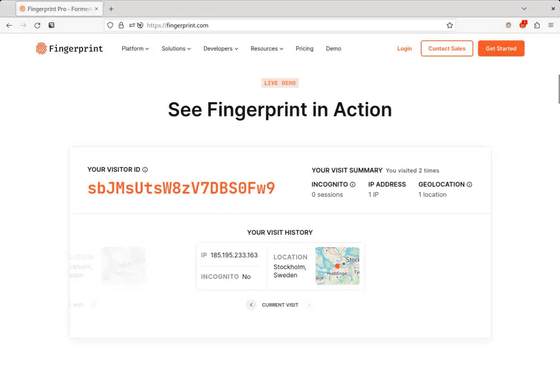
Furthermore, even after deleting all information and accessing in private browsing mode, the fingerprint was the same.
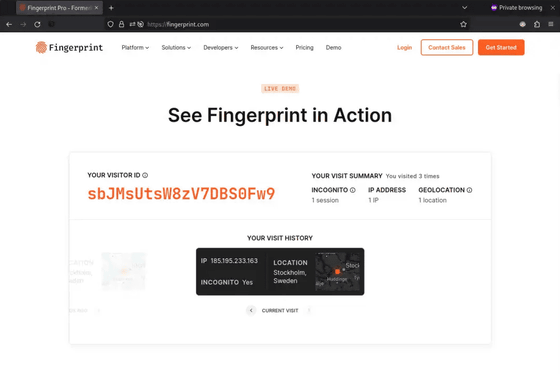
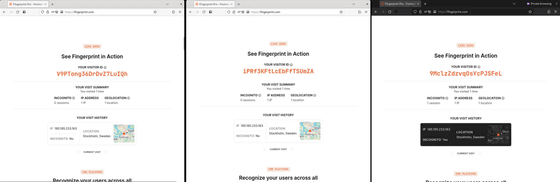
However, Firefox has an option called 'privacy.resistFingerprinting' that increases resistance to fingerprinting, and when enabled with this value set to 'true', 'FingerprintJS' can no longer recognize past browsing. . The following images are the first, second, and third accesses from the left, and the fingerprints are all different.
Similarly, when checking with other web browsers, Google Chrome and Chromium web browsers are powerless to generate fingerprints, and the fingerprints are the same for different sessions.
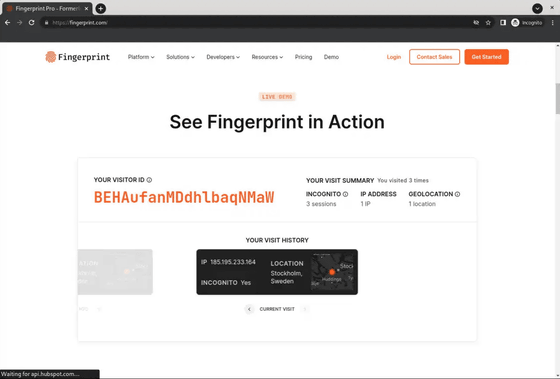
First access with Chrome
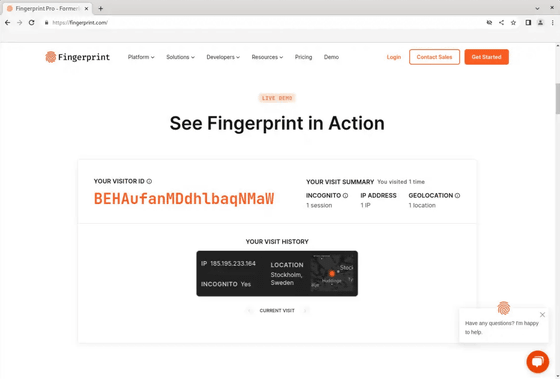
Second access with Chrome
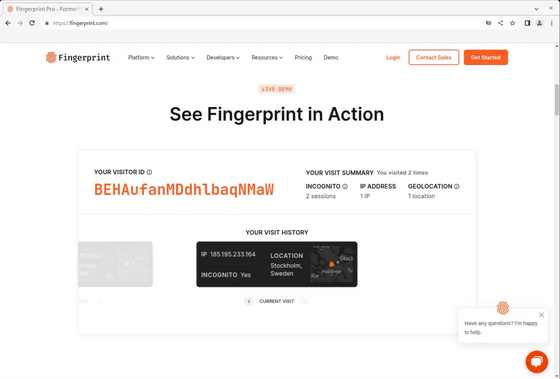
3rd access with Chrome
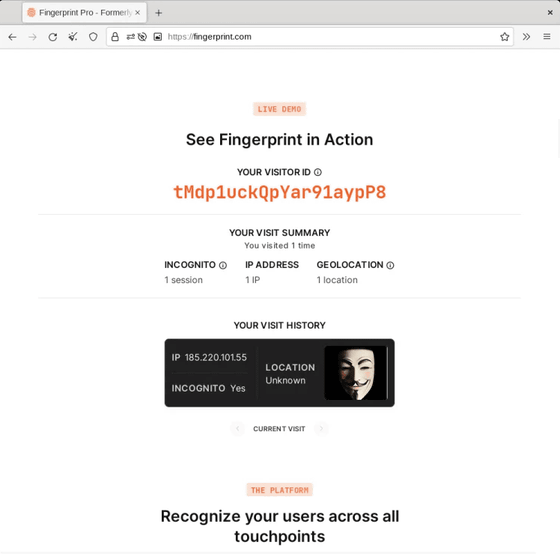
Tor Browser makes browsing sessions more private, and fingerprints were never the same across different sessions.
First access with Tor Browser
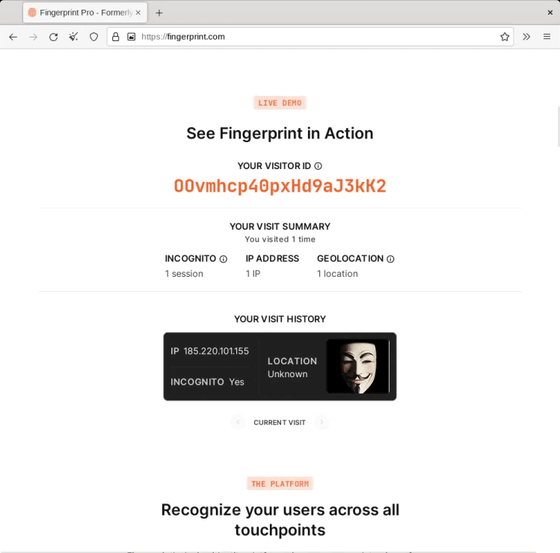
Second time accessing with Tor Browser. Since it always works in private browsing mode, he said that he did not access it for the third time.
From these results, Mr. bitestring says that if you want to protect yourself from fingerprints, use Tor Browser, set 'privacy.resistFingerprinting' to 'true' in Firefox, and use Brave if you use a Chromium browser. is recommended.
The fingerprints were not the same in the mobile version only when 'privacy.resistFingerprinting' was set to 'true' in Tor Browser and Firefox. It seems that the fingerprint is the same even if you clear the session every time with Firefox Focus , which claims to be a privacy-first browser.
Related Posts:
in Note, Posted by logc_nt