Ultra-simple passwords such as 'Password 1234' were used in large quantities at US government agencies

When setting a password for a device or web service account, it is common to take measures such as `` lengthening the number of characters '' and `` not using simple numbers and words '' to prevent dictionary attacks. However, there should be many people who use simple passwords such as '1234' and 'abcd'. A security audit conducted by the United States Department of the Interior revealed that one in five passwords used within the department consisted of easily guessable strings. In addition, we found that most of the participants did not have multi-factor authentication enabled.
P@s$w0rds at the US Department of the Interior: Easily Cracked Passwords, Lack of Multifactor Authentication, and Other Failures Put Critical DOI Systems at Risk | Office of Inspector General, US Department of the Interior
https://www.doioig.gov/reports/inspection/psw0rds-us-department-interior-easily-cracked-passwords-lack-multifactor
One of the typical methods of breaking through password protection is a ``dictionary attack'' that uses a list of strings that are often used in passwords, such as ``Password1234'' and ``qwerty''. The Security Audit Team of the United States Department of the Interior has identified ``terms used in the US government'', ``terms used in pop culture'', ``passwords exposed in past data breaches'', and ``character strings made up of adjacent keys on the keyboard''. ”, created dictionary data of 1.5 billion words, and performed dictionary attacks on the password hashes of 85,944 accounts.
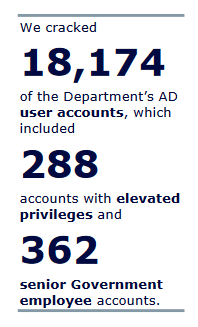
As a result of the attack, we succeeded in revealing 18,174 passwords, equivalent to 21% of the total. Of the accounts whose passwords were exposed, 288 had high privileges and 362 were government official accounts.
Below are the top 10 accounts used among the passwords exposed by the dictionary attack. In addition to very simple passwords such as 'Password-1234' and 'Password1234', obfuscation by changing 'o (o)' of 'Change It Now!' to '0 (zero)' 'ChangeItN0w!' Since the attacker has already incorporated measures such as changing 'o (o)' to '0 (zero)' and changing 'a (a)' to '@ (at mark)', these measures are completely doesn't make sense.
| password | number of accounts |
| Password-1234 | 478 |
| Br0nc0$2012 | 389 |
| Password123$ | 318 |
| password1234 | 274 |
| Summ3rSun2020! | 191 |
| 0rlando_0000 | 160 |
| Password1234! | 150 |
| ChangeIt123 | 140 |
| 1234password$ | 138 |
| ChangeItN0w! | 130 |
In addition, security audits revealed that most Department of Home Affairs departments did not have multi-factor authentication enabled, making password breaches directly linked to data breaches. It is said that the system used by the audit team to break through the password cost up to 15,000 dollars (about 1.98 million yen), but based on the audit results, the audit team said, ``If an attack with sufficient resources If someone obtains a password hash and carries out an attack, it may record a success rate similar to ours, ”he said, calling for enhanced security.
Related Posts:
in Security, Posted by log1o_hf