A cyber security company explains about the new Linux malware 'Shikitega' with high stealthness

Researchers at cybersecurity firm
Shikitega - New stealthy malware targeting Linux | AT&T Alien Labs
https://cybersecurity.att.com/blogs/labs-research/shikitega-new-stealthy-malware-targeting-linux
New Linux malware combines unusual stealth with a full suite of capabilities | Ars Technica
https://arstechnica.com/information-technology/2022/09/new-linux-malware-combines-unusual-stealth-with-a-full-suite-of-capabilities/
New Linux malware evades detection using multi-stage deployment
https://www.bleepingcomputer.com/news/security/new-linux-malware-evades-detection-using-multi-stage-deployment/
According to researchers, there are two main reasons why Shikitega is difficult to detect. First, it is polymorphic malware that encrypts itself with a different encryption key each time it is infected. This prevents detection using pattern matching that matches known viruses with suspected infected files. In addition, it seems that it is difficult to identify the source because it uses a legitimate cloud service to host a C2 server that serves as a stepping stone.
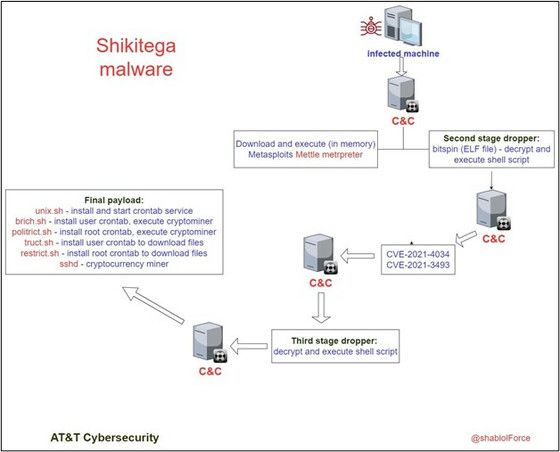
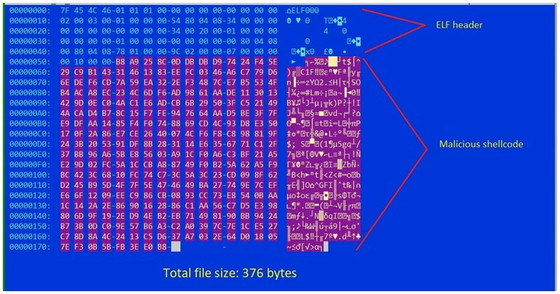
The primary dropper that creates and drops a file containing Shikitega's malicious code is a very small executable, just 376 bytes. The simple module delivered first is encoded by combining a multi-stage infection chain where each link downloads and executes the next link in response to part of the previous link. By using a polymorphic encoder during this distribution, it is difficult to capture the details of the malware.
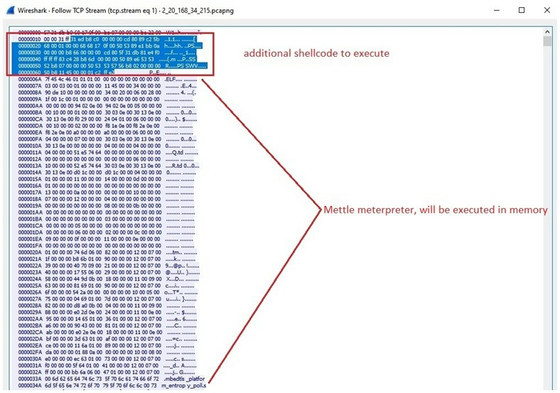
Shikitega's C2 server responds with
Although the purpose of Shikitega as malware is not clear, researchers believe that one purpose is to send software for mining cryptocurrencies. However, in addition to that, webcam control and credential theft are also being carried out at the same time, and there are concerns that mining is not the only function of the malware and that it has other ultimate goals.
A research team at AT&T Alien Labs has reported a sharp increase in Linux malware since 2022, urging system administrators to ``apply available security updates and prevent threats on all endpoints''. Use EDR with continuous monitoring and regularly back up your most important data.”
Related Posts:
in Security, Posted by log1e_dh