Succeeded in recovering virtual currency equivalent to about 4 billion yen stolen by North Korea

Chainalysis, a cryptocurrency analysis company, has seized $30 million worth of cryptocurrency worth over ¥75 billion (at the time) stolen by a North Korean-backed cybercriminal group. reported success.
$30 Million Seized: How the Cryptocurrency Community Is Making It Difficult for North Korean Hackers To Profit - Chainalysis
Feds claw back $30 million of cryptocurrency stolen by North Korean hackers | Ars Technica
https://arstechnica.com/information-technology/2022/09/feds-claw-back-30-million-of-cryptocurrency-stolen-by-north-korean-hackers/
In March 2022, the game ' Axie Infinity ', which collects NFTs ( non-fungible tokens ) expressed in the form of monsters, fights and breeds them, was hacked, resulting in 173,600 ETH ( Ethereum ). 25.5 million USD coins stolen. The amount of damage was over 75 billion yen when converted to Japanese yen at the rate at the time, and it was reported that it was the largest hacking damage related to virtual currency. At the time of writing the article, the value of Ethereum has dropped to 50-60% since the end of March 2022, so the total damage has decreased to about 47 billion yen.
More than 75 billion yen is stolen from the side chain of the game ``Axie Infinity'' where you can get virtual currency just by playing-GIGAZINE
In a subsequent investigation, the Federal Bureau of Investigation (FBI) announced that the North Korean cybercrime group Lazarus Group was involved in this hack.
It turns out that a North Korean cyber crime group was involved in the ``theft of 75 billion yen from NFT games''-GIGAZINE

In this incident, five of the nine private keys held by the Ronin Network transaction validator , which runs the sidechain Ronin Bridge that supports Axie Infinity, were accessed by the Lazarus Group. It turns out that malware disguised as a LinkedIn job was used to infiltrate the Ronin Network.
``Fake recruitment'' was used as a method of 75 billion yen hacking theft - GIGAZINE

Lazarus Group stole 173,600 ET and 25.5 million USD coins and then laundered them. It seems that more than 12,000 different virtual currency addresses were used for this money laundering.
According to Chainalysis, the money laundering method adopted by North Korean cyber crime groups such as the Lazarus Group can be roughly divided into the following five steps.
1: Send the stolen Ethereum to the broker's wallet.
2: Anonymize all Ethereum transactions with Tornado Cash.
3: Convert Ethereum to Bitcoin.
4: Mix Bitcoin.
5: Redeem Bitcoin.
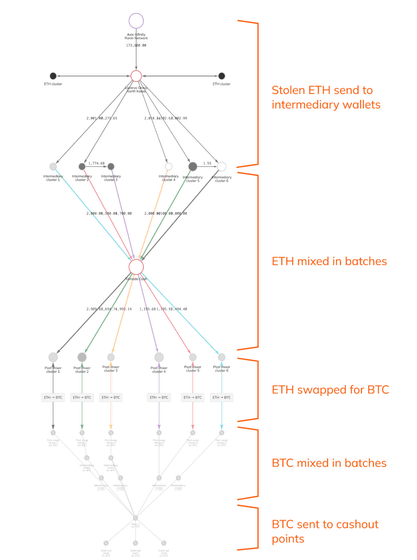
The most important part of this series of processes is Tornado Cash, a service that anonymizes Ethereum transactions by mixing multiple virtual currency transaction data. Tornado Cash has the purpose of protecting the privacy of traders, but it is actually being used for money laundering. In response, the US Treasury Department's Office of Foreign Assets Control (OFAC) designated Tornado Cash as sanctioned in August 2022.
Since Tornado Cash became subject to OFAC sanctions, the Lazarus Group has to rely on the trick of ``making the flow of stolen virtual currencies opaque by conducting large-scale transactions through the exchange of multiple types of virtual currencies.'' no longer get By tracking this transaction with their own tools, FBI and Chainalysis succeeded in seizing virtual currency equivalent to about 10% of the stolen assets. Chainalysis said, ``It shows that it is becoming more difficult for unscrupulous merchants to successfully cash out their illicit cryptocurrency profits.''
Chainalysis added, “The seizure would have been impossible without public-private cooperation. Many of the stolen assets from Axie Infinity remain untouched in hacker-controlled cryptocurrency wallets. , we hope to continue working with the cryptocurrency ecosystem to prevent them and other criminals from cashing out their stolen assets.”
Related Posts:
in Software, Web Service, Security, Posted by log1i_yk




