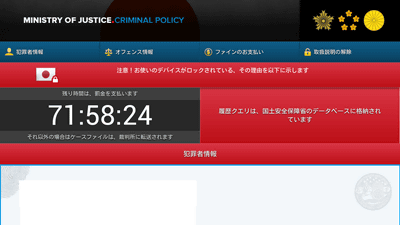
Introducing 'Good Will', a ransomware like a ransom that forces donations to the poor

GoodWill ransomware forces victims to donate to the poor and provides financial assistance to patients in need --CloudSEK
https://cloudsek.com/threatintelligence/goodwill-ransomware-forces-victims-to-donate-to-the-poor-and-provides-financial-assistance-to-patients-in-need/
CloudSEK's threat intelligence research team is working on an analysis of ransomware called 'Good Will.' According to the research team, ransomware that encrypts data on infected PCs and makes them unreadable usually distributes keys to decrypt the data in exchange for money. However, one group who uses GoodWill to launch an attack tells the victims to 'donate to the underprivileged.'
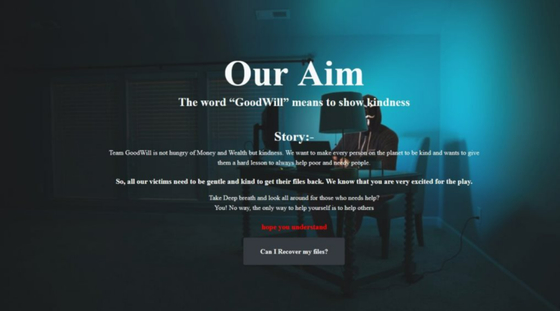
CloudSEK's threat intelligence research team first detected 'Good Will' in March 2022. Hackers who use this Goodwill to spread ransomware are believed to be conducting this attack not for financial purposes but for social justice. According to CloudSEK, the features of GoodWill are as follows.
· Written in
· Put the action to sleep for 722.45 seconds to interfere with the dynamic analysis of malware
· Encrypt data using the AES algorithm using the AES_Encrypt function
-Contains the string 'GetCurrentCityAsync' that attempts to detect the geographic location of the infected device
GoodWill-infected PCs will have encrypted documents, photos, videos, databases and other important files, and will not be able to access these data without a decryption key. The attacker then asks the victim for three social justice activities instead of the decryption key. The three activities that the attacker seeks are as follows.
1: Donate new clothes to the homeless, record their actions and post on social media
2: Take five underprivileged children to Domino's Pizza, Pizza Hut, or Kentucky Fried Chicken, take photos and videos of their meals, and post them on social media.
3: Provide financial support to those who need urgent medical care but cannot afford to do so, and record and share the audio.

After completing three social activities, the attacker will be asked to write 'How kind he became a victim of ransomware called Good Will' on Facebook or Instagram. Since there are no known victims of GoodWill, CloudSEK states that there are many unclear points in the attacker's tactics, techniques, and attack procedures.
After reporting that the victim has completed three social activities, the attacker confirms the victim's postings on social media. After confirming social activities, the attacker will provide a decryption kit that includes a video tutorial on the main decryption tools, password files and how to recover important files.
The CloudSEK research team has identified that the email address provided by the attacker belongs to an Indian-based IT security solutions company that provides end-to-end managed security services. In addition, GoodWill contains 1246 character strings, of which 91 character strings are said to have been included in the ransomware called 'Hidden Tear'. HiddenTear is an open source ransomware created by a Turkish programmer, and its proof of concept is published on GitHub. As a result, CloudSEK points out that 'GoodWill operators may be able to access GitHub and create new ransomware (GoodWill) with the necessary changes.'
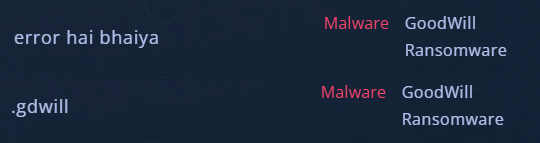
Among the strings included in GoodWill discovered by CloudSEK researchers, the following are interesting ones.
error hai bhaiya: This means Hinglish 'I have an error, brother', indicating that the operator is a Hindi speaker from India.
.gdwill: The file extension used by ransomware to encrypt files is '.gdwill'
In addition, among the network artifacts related to GoodWill, the ones discovered by the CloudSEK research team are as follows.
・ Http://9855-13-235-50-147.ngrok.io/ (GoodWill Ransomware Dashboard)
・ Http://9855-13-235-50-147.ngrok.io/alertmsg.zip
・ Http://9855-13-235-50-147.ngrok.io/handshake.php
・ Http://84a2-3-109-48-136.ngrok.io/kit.zip
Below is the Goodwill Ransomware dashboard
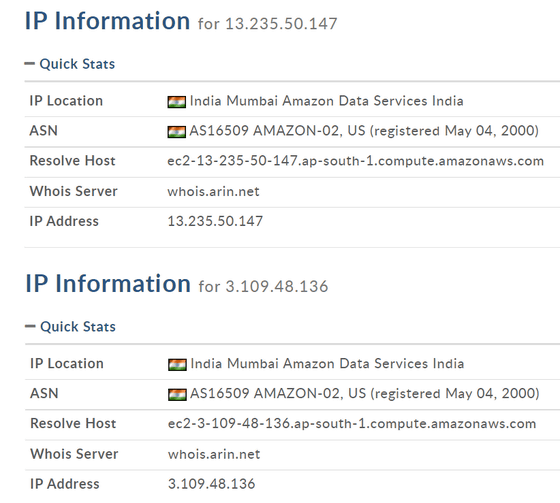
In addition, the attackers are using two IP addresses, '3.109.48.136' and '13.235.50.147', which have been revealed to be from Mumbai, India.
The effects of Good Will on CloudSEK are 'leakage of confidential information such as business practices and intellectual property', 'possibility of temporary and in some cases permanent loss of company data', 'possibility of business suspension of the company and it'. Incidental loss, 'Financial loss related to data recovery work', 'Possibility of damaging the company's reputation', 'Possibility of account takeover', 'Personal information such as the attacker's name, date of birth, address' May be used in combination with social engineering and theft of personal information. '
Related Posts:
in Security, Posted by logu_ii