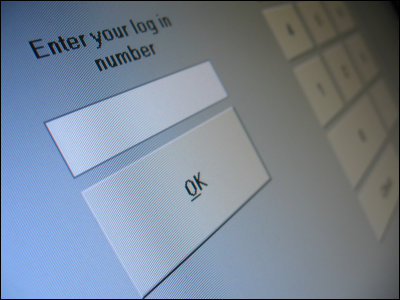
A method to steal passwords by imitating OAuth authentication such as 'Login with Google' and 'Login with Facebook' is devised.

Some web services allow '
Browser In The Browser (BITB) Attack | mr.d0x
https://mrd0x.com/browser-in-the-browser-phishing-attack/
Behold, a password phishing site that can trick even savvy users | Ars Technica
https://arstechnica.com/information-technology/2022/03/behold-a-password-phishing-site-that-can-trick-even-savvy-users/
OAuth authentication allows you to sign in to a web service using the registration information of another web service. For example, the following is the guidance screen for OAuth authentication displayed on the page of the image editing site 'Canva', and the characters such as 'Continue with Apple' and 'Continue with Google' that you can log in with the accounts of various services are lined up.
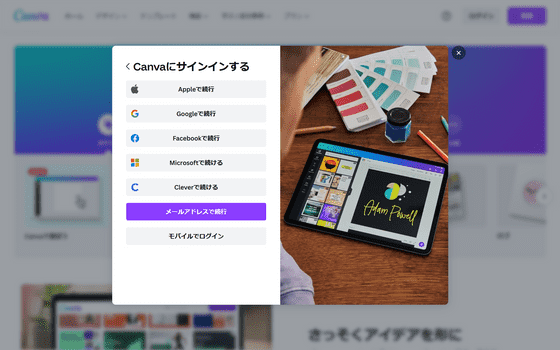
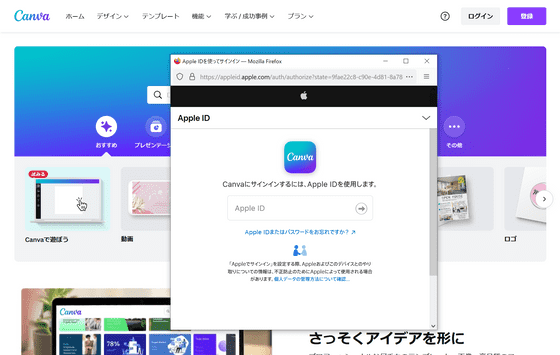
Click 'Continue with Apple' to open the OAuth authentication page in a new window. With OAuth authentication, authentication is performed based on personal information registered with Apple and Google, and each web service such as Canva is provided with only tokens that allow access. For this reason, it is a highly convenient authentication method for users who do not want to reveal their personal information to many web services.
As mentioned above, OAuth authentication is used in many web services because of its convenience. However, security researcher mr.d0x reports that it is very easy to spoof the authentication screen of OAuth authentication with HTML or CSS. In the image below, the left side is a fake Facebook authentication page created by Mr.d0x, and the right side is a real page. At first glance, there seems to be little difference between the two.
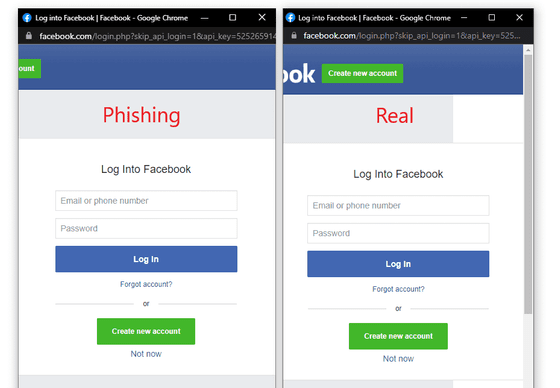
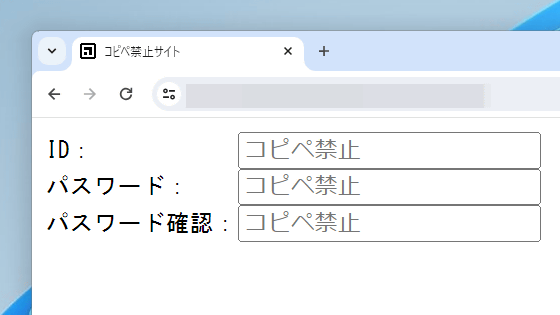
By embedding such a fake page in a fake website, users may unquestionably enter their credentials. It has also been confirmed that this technique was
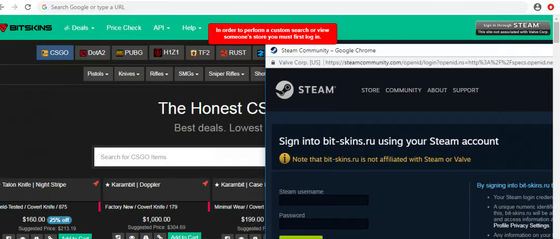
By Zscaler
Mr.d0x calls this technique a 'Browser In The Browser (BITB) attack' and states that 'few people notice a slight difference and it is basically indistinguishable from the real thing.'
Related Posts:
in Security, Posted by log1p_kr