'Sha256 Algorithm Explained' that visualizes the calculation process of the hash function 'SHA-256' in an easy-to-understand manner
Developed by the National Security Agency (NSA) in the United States,
Sha256 Algorithm Explained
https://sha256algorithm.com/
When you access Sha256 Algorithm Explained, it looks like this.
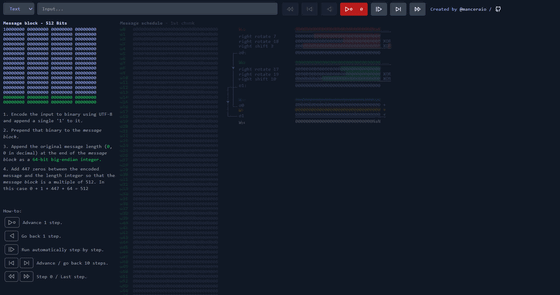
Enter your favorite character string in the input field at the top. This time, I entered the URL of GIGAZINE 'https://gigazine.net/'. Then, the message block that converted the entered URL into
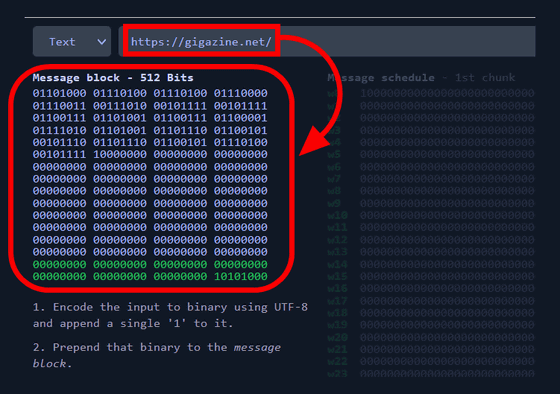
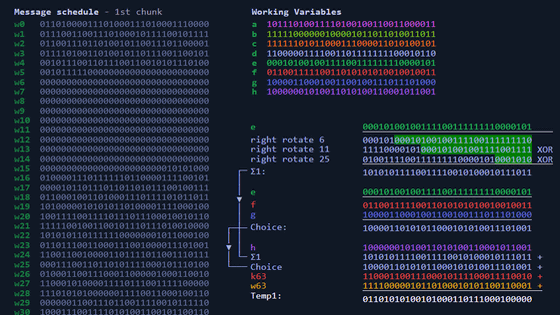
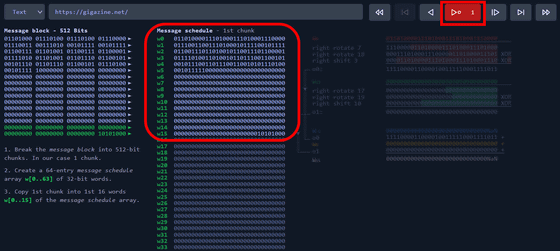
Click the red play button in the upper right to go one calculation step. First, a message schedule of 32 bits x 64 lines = 2048 bits is generated based on the message block composed of the binary of the input character string.
For example, in the following case, circular shift (right rotate) and logical shift (right shift) are performed on the 1st and 14th lines, the exclusive OR of each result is obtained, and ρ0 and ρ1 are calculated. increase. Then, the result of summing ρ0 and ρ1 on the 0th and 9th lines is written on the 16th line of the message schedule.
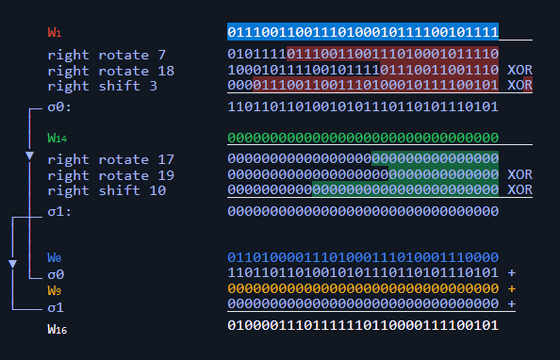
By proceeding with this calculation in order from the top, a message schedule will be generated.
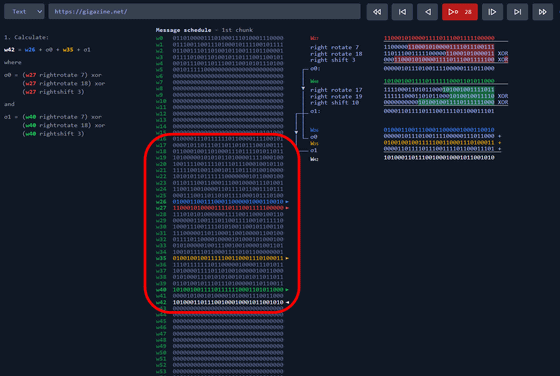
When all the message schedules of 32bit x 64 lines are generated, it looks like this.

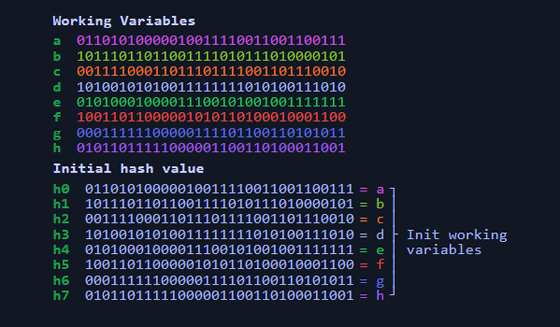
Then calculate the hash from the message schedule. The 'Working Variables' a to h combined with the message schedule are the eight variables that make up the hash. The initial values of these eight variables are set to a fixed Initial hash value. In SHA-256, a binary obtained by evolving the square root of the prime numbers 2, 3, 5, 7, 11, 13, 17, and 19 into two is used as the initial hash value.
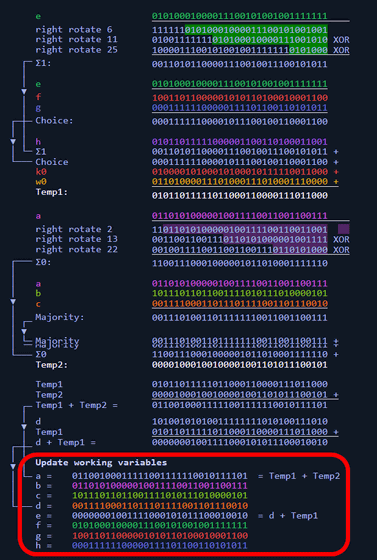
The calculation is complicated, but the hash calculation basically uses circular shift and exclusive OR as well as message schedule generation. A mechanism that calculates new hash variables a to h from a specific line of the message schedule and hash variables and overwrites them.
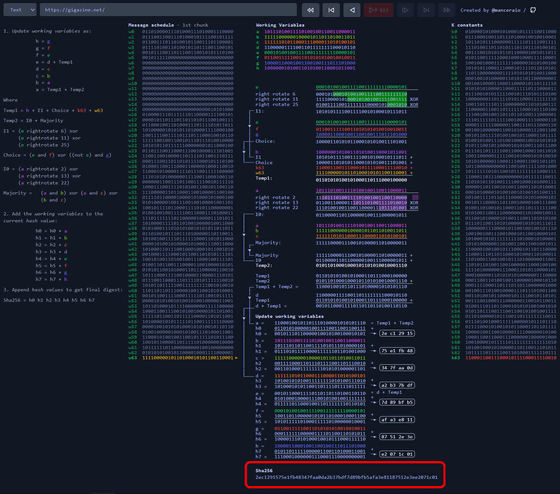
This calculation is carried out in order from the top of the message schedule, and the final hash variable is converted to hexadecimal HEX and arranged, and summarized in a 256-bit hash. The SHA-256 hash is obtained by repeating complicated calculations based on the binary of the original data, and it is extremely difficult to restore the original data from the hash.
Related Posts:
in Review, Security, Web Application, Posted by log1i_yk