Cookie theft malware aimed at YouTuber channel hijacking is used by Russian hackers

Researchers from Google's Threat Analysis Group (TAG) have announced that YouTuber has been targeted for phishing attacks using cookie theft malware since around 2019. The attack is known to be carried out by multiple hackers recruited in Russian-speaking forums.
Phishing campaign targets YouTube creators with cookie theft malware
Hackers are hijacking YouTube influencer accounts with fake collabs --Protocol — The people, power and politics of tech
https://www.protocol.com/russian-hackers-youtube-phishing
YouTube creators' accounts hijacked with cookie-stealing malwareSecurity Affairs
https://securityaffairs.co/wordpress/123630/hacking/youtube-creators-accounts-hijacked-malware.html
Cookie theft is an attack that allows you to access your account using session cookies stored in your browser, also known as a 'pass-the-cookie attack'. This method has existed for a long time, and it is said that it has become a security risk in recent years because social engineering has come to be used as the main attack method due to the spread of multi-factor authentication.

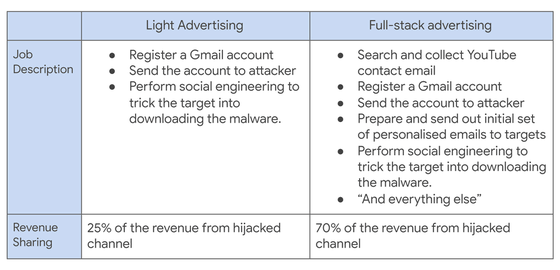
Many YouTubers post their email addresses on their channels and receive work deals. The attacker impersonates an existing company and sends a spoofed business email asking YouTuber to collaborate. The content of the email is an introduction to the company or product, but the body of the email and the attached PDF file contain malware download links.
Attackers have registered various domains to disguise themselves as companies and created websites for malware distribution, and at least 1011 spoofed websites have been confirmed at the time of article creation. Some of the camouflaged websites were disguised as Instagram, the game sales platform Steam, and the information site for the new coronavirus. In addition, YouTuber often uses Gmail for contact, and since Gmail detects phishing links, there were cases where it led to messaging apps such as WhatsApp, Telegram, Discord.
When the targeted YouTuber runs the software downloaded from the spoofed website, malware that steals session cookies and password information is launched and uploads the session cookie to the attacker's server. Normally, such malware can run permanently on YouTuber's PC, but it is limited to temporary action so that it will not be detected by security software.
When an attacker hijacks a YouTuber channel, it rewrites the channel name, profile image, and content into a brand for cryptocurrency fraud. The hijacked channel will broadcast a live movie that appeals, 'If you pay a certain amount, you will receive a virtual currency' while pretending to be a major technology company or a virtual currency exchange.

According to Google, job listings for a series of channel hijackers were posted on a Russian-speaking cyber forum. By hiring different hackers, Google explained that the techniques used were also diversified. Also, in the trading market of accounts existing in the underground, YouTuber channels were traded at a price of 3 dollars (about 330 yen) to 4000 dollars (about 440,000 yen) depending on the number of subscribers.
Google 'Detects and blocks phishing emails, cookie theft hijackings, and live delivery of virtual currency scams' 'Detects and blocks spoofed websites and malware downloads' 'Enhances and hijacks channel transfer workflows' It reports that it has dealt with channel hijacking by means such as 'detecting and recovering more than 99% of the channels that have been compromised' and 'strengthening the account authentication workflow to block suspicious behavior and notify the user'.
In addition, Google cites the following five methods to protect the channel from attacks.
・ Do not underestimate the warning of safe browsing.
-Perform a virus scan before running the software to verify the validity of the software.
-Enable 'enhanced protection' from Chrome's Safe Browsing settings.
-Watch out for encrypted archives.
· Enable 2-step verification to protect your account.
Related Posts:
in Security, Posted by log1i_yk







