Starting with takeover of Facebook account and finally bank account is made Sukarakan is a fraud scheme

A cracker takes over a Facebook account of a user and it is pulled out from the bank account of the relative to the deposit until the deposit becomes Sukarakan .... Such a fraud case has occurred and the way of doing it is clarified.
From full Facebook account takeover to an empty bank account - BadCyber
https://badcyber.com/from-full-facebook-account-takeover-to-an-empty-bank-account/
A terrible incidents that banks will be emptied while they are unknown are said to have occurred in Poland. Cyber security related mediaBadCyberI have clarified that method on the site.
The set of techniques starts with hijacking of the Facebook account first. Here, the login information of the user illegally acquired by malware, phishing fraud etc. method is used, and users who do not apply security measures such as two-step authentication become a good target. After successful hijacking, the cracker first checks the history of the chat and identifies the person closely tied to the account holder. It is the family of the accountant who tends to be targeted here, and it seems that many people like grandfather and grandmother are often targeted.
If you find a target that seems to be a fraud, the cracker tells that person "Hey grandma, will you send me 22 pounds sweaties (about 650 yen) to charge my pre-paid phone charges?" I will send you a message. And, if the target agrees to send money, we will send the following link.
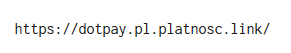
"DotPay" is the name of the company conducting remittance service in Poland, "platnosc" is Polish word "payment" in Polish. Such a service is widely used in Poland, and it is said that it is used in various transaction settlement places in cooperation with domestic banks. The remittance destination and remittance amount are set in advance in the link sent to the target, and the target can click on the link and log in to the bank site easily to make money transfer easily.
However, in fact, this link is supposed to be redirected to a fraudulent site that was skilfully imitated as follows. Credit cards, bank logos, etc. are displayed, and at first glance it is made to be confusing to be a fake site.

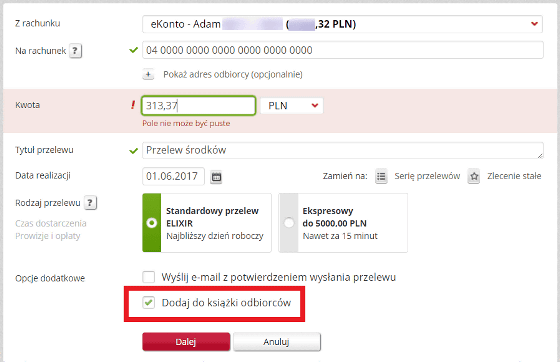
When the target enters login information to the account of the bank through this site, it seems that they all come to crackers hands. However, only 22 Poland ploty is transferred in this transaction, it is far from being stolen from the balance of the bank account. The function that a cracker exploits here is a function called "trusted transfer" (trusted remittance).
With this function, remittances made to the same account can all be executed without using the SMS authentication code. This is a function that is implemented to omit the procedure for transactions that you normally use to improve user convenience. In the portion indicated by the red frame, it is stated that "Add to the remittance destination list" and by checking this place, remittance to this account will be executed without going through a troublesome authentication process in the future It will be possible.
In this way, the cracker takes over the target bank account, remittances the balance to his account, and then converts it to bit coins. It seems that such a method has been confirmed many times in Poland over the last few weeks. It is difficult to find and regulate this illegal deal at the bank level and as effective protection measures are not taken over by Facebook account, there seems to be only the need to strengthen security with two-step verification. Also, it seems that it is only necessary to call attention to relatives so as not to respond to suspicious remittance requests.
Related Posts:
in Web Service, Security, Posted by darkhorse_log