A vulnerability has been discovered that allows system privilege elevation simply by connecting a Razer mouse.

A zero-day vulnerability that enables local privilege elevation was discovered in
Razer bug lets you become a Windows 10 admin by plugging in a mouse
https://www.bleepingcomputer.com/news/security/razer-bug-lets-you-become-a-windows-10-admin-by-plugging-in-a-mouse/
The first time you connect your Razer mouse or keyboard to your Windows PC, we recommend installing a tool called Razer Synapse. This Razer Synapse is a management software that allows you to set mouse buttons and macros.
Security researcher and white hacker jonhat discovered that the Razer Synapse installation process, which involves connecting a mouse or keyboard, is vulnerable to a zero-day vulnerability that makes it easy to gain system privileges on Windows.
Need local admin and have physical access?
— Jonhat (@ j0nh4t) August 21, 2021
--Plug a Razer mouse (or the dongle)
--Windows Update will download and execute RazerInstaller as SYSTEM
--Abuse elevated Explorer to open Powershell with Shift + Right click
Tried contacting @Razer , but no answers. So here's a freebie pic.twitter.com/xDkl87RCmz
The vulnerability requires that the Razer mouse, keyboard, and wireless dongle be physically connected to the PC. RazerInstaller.exe, the Razer Synapse installation executable, launches through a Windows process that runs with system privileges, so RazerInstaller.exe also gains system privileges.
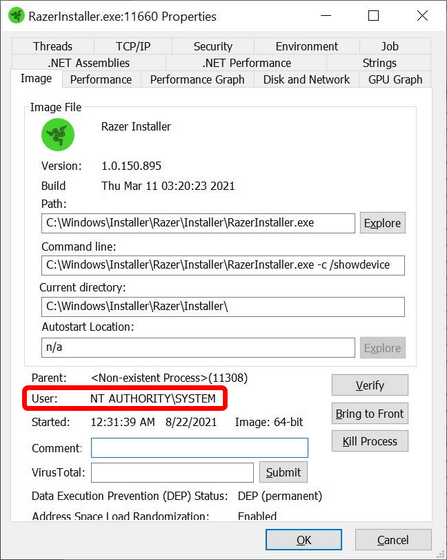
Then, when selecting the folder to install Razer Synapse, you can open PowerShell by holding down the Shift key and right-clicking the 'Select Folder' dialog.
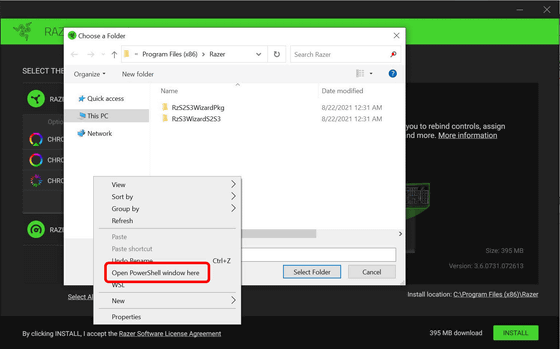
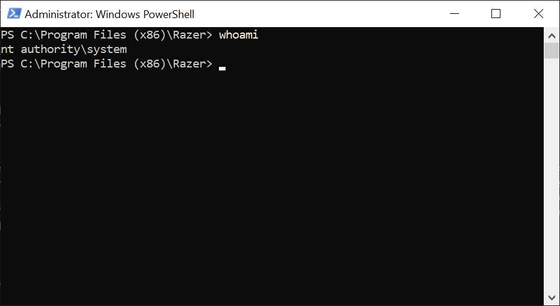
If you enter the 'whoami' command in the actual PowerShell that opens, you will see that you have system privileges.
Security researcher Will Dorman said, 'Given the combination of' the software is automatically loaded when you connect the USB 'and' install the software with system privileges ', other exploits are possible. There may be other packages, 'he said, pointing out that there may be other tools with similar vulnerabilities besides the Razer Synapse.
Many vulnerabilities fall into the class of 'How has nobody realized this before now?'
— Will Dormann (@wdormann) August 22, 2021
If you combine the facts of 'connecting USB automatically loads software' and 'software installation happens with privileges', I'll wager that there are other exploitable packages out there ...
According to Mr. jonhat, even if he contacted Razer at the beginning, there was no response, so it was released on Twitter, but after the release, Razer's security team said, 'We are working on fixing it as soon as possible.' It seems that there was a report. The vulnerability has already been posted on Twitter, but Razer will pay jonhat a bug-finding bounty.
I would like to update that I have been reached out by @Razer and ensured that their security team is working on a fix ASAP.
— Jonhat (@ j0nh4t) August 22, 2021
Their manner of communication has been professional and I have even been offered a bounty even though publicly disclosing this issue.
Related Posts: