Western Digital NAS 'My Book Live' all data erasure case turned out to be a zero-day vulnerability

In June 2021, there were a series of reports that all the data stored in the NAS 'My Book Live' made by Western Digital (WD) had disappeared, and
WDC-21008 Recommended Security Measures for WD My Book Live and WD My Book Live Duo | Western Digital
https://www.westerndigital.com/support/productsecurity/wdc-21008-recommended-security-measures-wd-mybooklive-wd-mybookliveduo
CVE-2018-18472: Western Digital My Book Live Mass Exploitation --Censys
https://censys.io/blog/cve-2018-18472-western-digital-my-book-live-mass-exploitation/
Hackers exploited 0-day, not 2018 bug, to mass-wipe My Book Live devices | Ars Technica
https://arstechnica.com/gadgets/2021/06/hackers-exploited-0-day-not-2018-bug-to-mass-wipe-my-book-live-devices/
On June 24, 2021, a report was posted on the official WD forum that 'all data stored in My Book Live has been deleted.' Since similar reports continued after that, the person in charge of WD reported that he started investigating to clarify the cause, and said, 'It is recommended to disconnect My Book Live from the Internet.' It was.
Western Digital's NAS 'My Book Live' is experiencing a phenomenon that all data disappears, officially saying 'Anyway, disconnect the Internet immediately' --GIGAZINE
Then, on June 25, 2021, WD said, 'I checked the log file of My Book Live that had the problem and found that it was being accessed from multiple IP addresses. It indicates that you were accessing My Book Live directly via the Internet, 'he said, reporting that the data erasure incident was due to a cyberattack that exploited a vulnerability in My Book Live.
In addition, reports of users affected by the data erasure attack and restored log files revealed that the attacker was performing My Book Live initialization using multiple IP addresses. WD, who received this report, said, 'It is probable that the attacker exploited CVE-2018-18472 and then the vulnerability to reset it to the factory default state,' said multiple vulnerabilities in the data erasure attack. State the view that was being used.
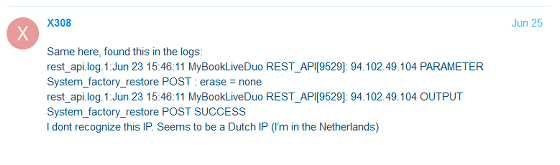
On the other hand, according to security company Censys , it is enough to use CVE-2018-18472 to actually carry out a data erasure attack on the product. Nonetheless, the reason why there are traces of multiple vulnerabilities being exploited is that 'an attacker other than the attacker who first used CVE-2018-18472 to gain unauthorized access to My Book Live You may have performed a data erasure attack. '
In addition, WD reported that 'users affected by this attack have succeeded in recovering data using data recovery tools. We investigated the effectiveness of these tools. We are showing a willingness to continue responding to data erasure attacks.
Related Posts:






