D-Link abandons patch for critical vulnerability affecting over 60,000 routers, urging users to 'replace' them

Several bugs, including a critical vulnerability, were discovered in multiple router models manufactured by Taiwanese telecommunications equipment manufacturer D-Link. However, D-Link indicated that it would not fix the vulnerabilities because support for those products had ended, and urged users to update their devices.
D-Link won't fix critical flaw affecting 60,000 older NAS devices
D-Link won't fix critical bug in 60,000 exposed EoL modems
https://www.bleepingcomputer.com/news/security/d-link-wont-fix-critical-bug-in-60-000-exposed-eol-modems/
D-Link urges users to retire VPN routers impacted by unfixed RCE flaw
https://www.bleepingcomputer.com/news/security/d-link-urges-users-to-retire-vpn-routers-impacted-by-unfixed-rce-flaw/
D-Link says it won't patch 60,000 older modems, as they're not worth saving | TechRadar
https://www.techradar.com/pro/security/d-link-says-it-wont-patch-60-000-older-modems-as-theyre-not-worth-saving
The vulnerabilities in question were discovered by security researcher Netsecfish in several models of D-Link network-attached storage (NAS) devices that are popular with small and medium-sized businesses.
The vulnerability, numbered ' CVE-2024-10914 ', affects the following models:
・DNS-320 version 1.00
・DNS-320LW Version 1.01.0914.2012
・DNS-325 version 1.01, version 1.02
・DNS-340L Version 1.08

CVE-2024-10914 has a
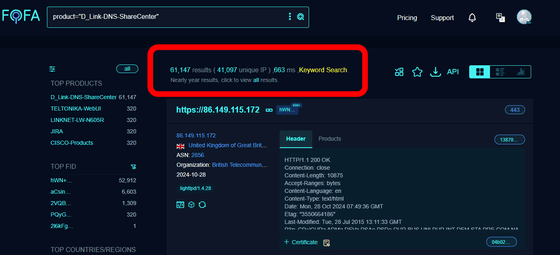
When Netsecfish searched for devices affected by CVE-2024-10914 on FOFA, an IoT device search engine, he found 61,147 devices across 41,097 unique IP addresses.
However, in
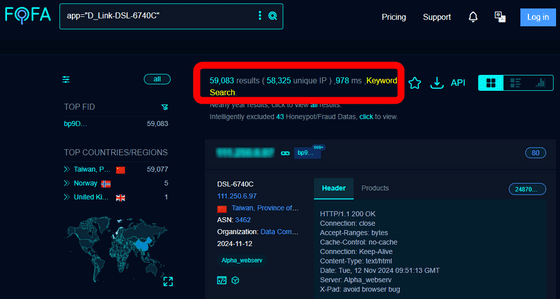
Subsequent research by security researcher Chaio-Lin Yu has found seven more vulnerabilities in the D-Link DSL6740C, including one that is rated as extremely severe (CVSS score 9.8) because it allows an attacker to change the password of any user.
It has also been confirmed that approximately 60,000 DSL6740C units are in operation.
In addition, the details of some vulnerabilities have not been disclosed because the risk of exploitation is so high. The following products are affected by this vulnerability, discovered by security researcher delsploit:
| Model | EOS |
|---|---|
| DSR-150 | May 1, 2024 |
| DSR-150N | May 1, 2024 |
| DSR-250 | May 1, 2024 |
| DSR-250N | May 1, 2024 |
| DSR-500N | September 30, 2015 |
| DSR-1000N | October 30, 2015 |
However, D-Link did not distribute any patches for these issues either, instead stating in its security advisory that customers should 'upgrade to newer products.'
'Even though scans found tens of thousands of exposed endpoints, D-Link decided not to address the risks,' said BleepingComputer, an IT news site.
In the comments section of BleepingComputer, comments such as 'It certainly seems like it's time to switch to a device from another manufacturer' and ' If that's the case, they should stop selling it on Amazon too' have been posted.
Related Posts:
in Security, Posted by log1l_ks