What is 'Genesis Market', which was also the cause of a large-scale leak that sells login information for only 1000 yen?

It was reported on June 10, 2021 that
Inside the Market for Cookies That Lets Hackers Pretend to Be You
https://www.vice.com/en/article/n7b3jm/genesis-market-buy-cookies-slack
It was discovered on June 10, 2021 that EA, known for the ' Battlefield ' series and ' FIFA ' series, was hacked and a large amount of source code and internal tools were stolen.
EA is hacked and stolen 780 GB of source code and internal tools are sold - GIGAZINE

According to the IT news media Motherboard, the hacker who caused this incident used a cookie purchased for $ 10 (about 1100 yen) to log in to EA's Slack account and cheated the IT support staff inside the company The network was intruded.
Motherboard is in contact with this hacker and has found that the hacker purchased cookies at an invitation-only underground site called 'Genesis Market'.
A cookie is a small file that your computer uses to store a variety of information. Information entered by the user on the website, login information, etc. can be saved on the device as a cookie. You can read more about how cookies work below.
What are cookies? |GIGAZINE.BIZ

In addition, websites use cookies from advertising companies that are unrelated to the website the user has visited, allowing the website to track user behavior outside of its own site. This is called a third-party cookie , and in recent years there have been concerns about its use from the perspective of privacy.
According to Motherboard, using the Genesis Market, cookies and device fingerprints will allow hackers to create a 'replica' of the browser targeted by the attack.
Matthew Gracey-McMinn, head of research at Netacea, a cybersecurity company that investigated the Genesis Market, said data purchased on the Genesis Market could allow hackers to bypass two-factor authentication in some cases. This is because users logged in using Genesis Market data appear to be “legitimate users,” and “this kind of data makes hackers and victims almost indistinguishable,” Gracey-McMinn explained. bottom.
Also, the hackers who attacked EA didn't just buy a single cookie, they bought exclusive access to a bot running as part of a botnet . Bots, which are a type of malware, are commonly used for purposes such as ``making it impossible for law enforcement agencies to identify the location of hackers'' or ``DDoS attacks''. On the other hand, Genesis Market makes it possible to obtain cookie information related to web services by using bots, and is sold in units such as 'bots associated with 5000 cookies'. Web services include Facebook, Apple, Netflix, GitHub, Steam, Instagram, Adobe, Amazon, Google, Tumblr, Twitter, Dropbox, PayPal, LinkedIn, Slack, Spotify, Reddit, Pinterest, etc.
The hacker who attacked EA says that the Genesis Market can 'filter by URL' the desired web service. When Gracey-McMinn and others actually searched for bots related to 'Slack' on the Genesis Market, it became clear that there were more than 3,500.
The total number of bots sold on the Genesis Market was about 400,000.
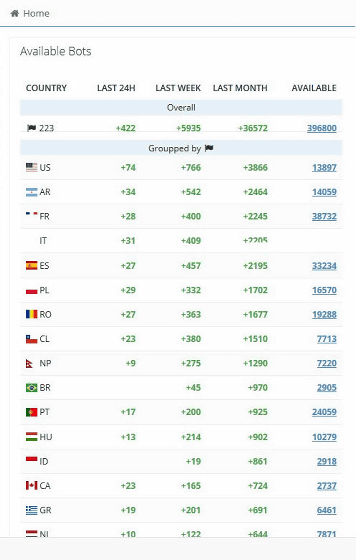
Hackers who purchase bots can get login information contained in cookies, such as email addresses and passwords, so they can access those websites. It can also use the Genesis Market browser plugin and login information to mimic victims at a more granular level. Moreover, if the bot is still active, information will continue to be collected, so data will continue to flow in without purchasing a new bot. ``Basically, if you buy early, you will get a bargain.In the end, you can get something worth hundreds of dollars (tens of thousands of yen) at 70 cents (about 77 yen).'' Gracey-McMinn said.
Gracey-McMinn and others believe there is one group behind the Genesis Market. The group originally sold the information they collected using malware, and later seems to have allowed others to sell the information as well.
Researchers say they can monitor attacks via plugins by reverse engineering the Genesis Market plugin, but they also say that attacks that do not use plugins are difficult to detect.
Related Posts:
in Security, Posted by darkhorse_log







